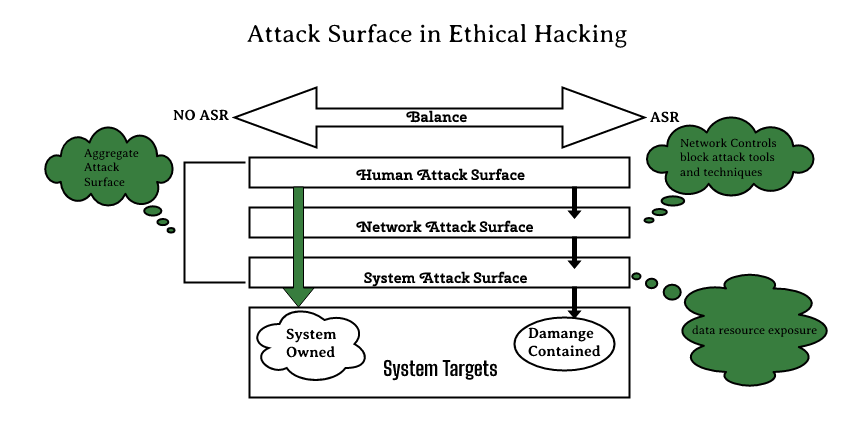
Attack surface is the general term for the areas of a system, device, or network that contain security vulnerabilities that may be exploited. The attack surface of an organization’s computer systems and devices can often vary significantly depending on what they are used for and how they have been configured. This is not to be confused with “attack surface in ethical hacking”, which relates to the potential risk posed by vulnerabilities within a given operating system or application installed on a computing device.
In practice, this method can be used to determine if a device is vulnerable to known and unknown forms of attack, one example of this would be to analyze the operating system an attacker might use.
For example, if an organization’s IT infrastructure uses the Linux operating system for its email platform, then it is possible that this could be subject to an attack using the shell shock vulnerability. Attack surfaces can also be examined for vulnerabilities in non-operating system software, as well as hardware devices like switches and routers – though these are typically harder to patch.
Types of Attack Surfaces:
- Passive: A passive attack surface refers to a system or network that has either been compromised by an attacker (i.e., the individual is already providing resources) or has not yet been compromised by an attacker, but provides its own security services (e.g., password authentication).
- Active: An active attack surface includes a system or network in which an attacker may directly interact with elements of the infrastructure, such as users and devices. Active attacks on a target are typically performed during reconnaissance and pre-attack phases when more information about the target is desired before initiating any destructive actions.
Prevention from Attack Surfaces:
- Attack surface reduction (ASR) is a security measure designed to reduce the number and variety of potential attack surfaces available to an attacker.
- ASR is distinct from vulnerability management, which concentrates on reducing the likelihood that a vulnerability can be exploited by an attacker.
- By removing unnecessary features and functionality from products, services, and systems that are deployed in live environments, an organization can greatly reduce its overall exposure to vulnerabilities.
- ASR can be achieved through a number of mechanisms, such as Methodology for attack surface reduction.
- The approach for attack surface reduction is similar to the methodology for software testing.
- Attack surface metrics, which help to calculate risk and return of investment (ROI).
- There are various tools available in the market that can perform some or all of these tasks related to attack surface analysis and reduction. Some examples are Microsoft Baseline Security Analyzer(MBSA), WebInspect, WebEssentials, Windows Defender Exploit Guard, Nessus, and several others.
Key Points:
- Attack surfaces can be divided into a number of categories which can be used to gain a better understanding of what is being searched for.
- Port scans and OS-specific exploits have been used for decades, but more recently it has become more common for ethical hackers to use software designed specifically to examine web server configuration, application security, and software vulnerabilities themselves – using tools such as WebScarab and various web application scanners.
- All of these methods are targeted at the operating system itself rather than a specific piece of application software.
- In order to successfully find vulnerabilities in the software that has been installed on a networked device, it is important for an ethical hacker to have a good working knowledge of what is installed.
- This requires a detailed understanding of the organization’s IT architecture and its associated risks, as well as knowing how to use the technologies required to perform assessments.
- Vulnerabilities are also often identified during penetration testing activities, where security testing is performed using an external remote connection; this activity can help identify potential command injection bugs and other flaws in software or hardware which allow unauthorized access.
- Software designed specifically for attack surface analysis runs on Linux systems and typically uses an agent or client-server model.
Conclusion:
In ethical hacking, attack surfaces are searched for using software that is specifically designed for this purpose; typically these applications will examine various data like file permissions, network ports, running processes, and more so that any vulnerabilities present can be quickly identified and patched as appropriate.