Summary
- A massive hack has revealed that location data company Gravy Analytics is hoarding sensitive data such as user coordinates.
- Hackers have revealed that location data is being stored by misusing the real-time bidding process, which allows firms to bid for ad space within popular smartphone apps.
- Dating apps like Tinder and Grindr, plus games such as Temple Run, Candy Crush, and others, are among the impacted apps.
There’s a certain level of trust involved when we share our location data with smartphone apps, even if it’s a big-name app we use almost every other day. The downside is that malicious firms can always try to take advantage of that situation and access data they’re not supposed to. A massive hack has now brought another such instance to light wherein a data broker has put the location data of millions at risk.

AT&T and Ticketmaster hacker arrested after threatening to leak customer data
According to authorities
Almost every popular app out there comes with ads now. It’s usually meant to help the app developer keep the lights on while customers get to use the app without paying a dime. Location data companies in the past had to pay app developers to include code within their apps to obtain location data. But as investigative journalist Joseph Cox writes in Wired and 404 Media, interested parties no longer need to use this method, and instead go through a process called RTB or real-time bidding.
With RTB, ad firms bid against each other for the user’s attention inside a particular app. This process involves apps sharing some data with advertisers, which can include, among other things, your location data. What this hack reveals is that Gravy Analytics, a location data company, is holding onto a lot of the user data, including smartphone coordinates, and is willing to sell it off to the highest bidder. Gravy’s clientele includes both government and commercial entities, which raises even more fears about illegal surveillance.
Security researcher Krzysztof Franaszek told 404 Media that a majority of the hacked geolocation data had been obtained through IP addresses and not GPS data. Regardless, the sheer volume and type of apps affected here, coupled with the fact that this appears to have gone on without the knowledge of the app developers, is quite alarming.
Thousands of apps across multiple categories are affected
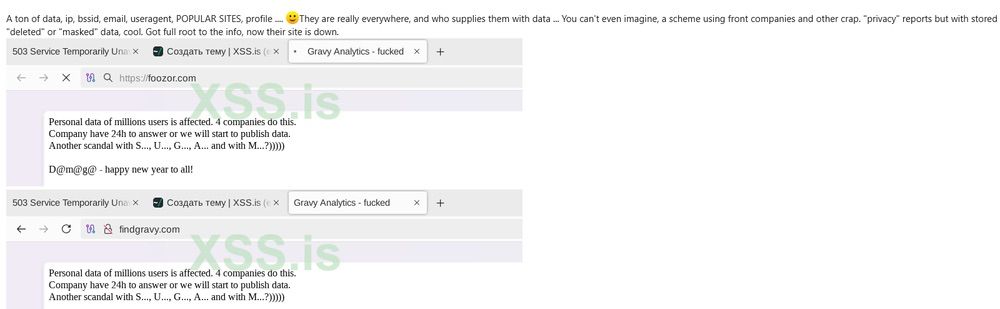
Hackers posted this screenshot on the cybercrime forum XSS
While the entire list is too long to list (over 12,000), some major names mentioned are dating apps like Tinder and Grindr, flight tracking app Flightradar24, a number of period tracking apps, VPN apps, plus games like Temple Run, Subway Surfers, and Candy Crush. The folks at 404 Media have compiled an exhaustive spreadsheet containing some of these apps, which you can find here.
“A location data broker like Gravy Analytics getting hacked is the nightmare scenario all privacy advocates have feared and warned about. The potential harms for individuals is haunting, and if all the bulk location data of Americans ends up being sold on underground markets, this will create countless deanonymization risks and tracking concerns for high risk individuals and organizations,” Zach Edwards, senior threat analyst at Silent Push told 404 Media.
Some app makers like Tinder and Grindr (both owned by Match Group) told 404 Media they had no business with Gravy Analytics. It’s worth mentioning that this user location data hoarding affects both Android and iOS devices. Google and Apple are yet to comment on this damning report, though we suspect it won’t be long till they issue a statement.

7 privacy-focused Android apps I use to keep my data secure
Essential Android apps to lock down your data
The hackers who brought this story to the fore uploaded data samples detailing Gravy Analytics’ culpability in the matter. Additionally, the hacker group posted messages on two Gravy websites briefly detailing the nature of the hack. Screenshots of these messages were then posted on the obscure cybercrime forum XSS, which isn’t publicly visible. However, a source of 404 Media managed to access them (pictured above) and shared it with the publication.