Computers are a necessity in today’s world. Our daily activities involve computers, making them a significant part of the modern world. Over the years, the use of computers has grown significantly. With the increasing demand for computers and related services, including computer and internet-related services, we often hear about internet crimes or cyber crimes very commonly.
Cyber crimes are increasing with the growing demand for the internet. With an increasing number of cybercrime cases reported each year, awareness of cyberattacks is very important. Cyber crimes/cyberattacks are done by hackers who unethically want to breach user data and steal sensitive information from the user accounts. The purpose behind cyberattacks is mostly related to personal or organizational gains, which may be achieved financially or emotionally.
Here in this article, we will discuss one of the most common forms of cyber attack i.e. HTTP flooding which is used by attackers to breach user privacy.
HTTP Flooding Attack:
- HTTP flooding attack is a layer 7 (Application Layer Attack) which is really dangerous and harmful as it is easy to attack websites using HTTP flooding.
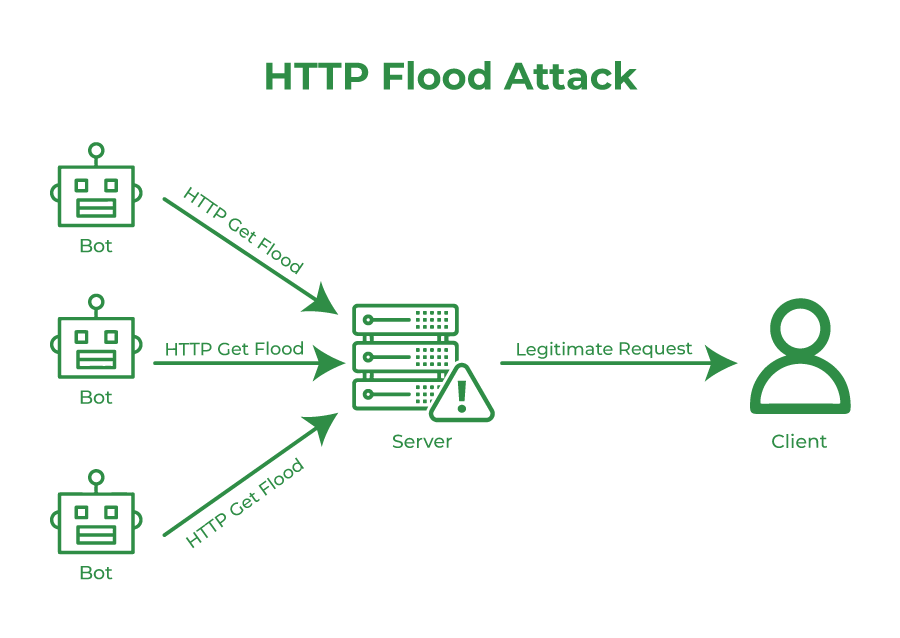
- HTTP flooding is a form of DDoS (Distributed Denial of Service) where an HTTP flood attack makes use of HTTP to get an HTTP post requests to carry out the cyberattack.
- The main purpose of an HTTP flooding Attack is to bring down a desired or needed site/ server by flooding it with a huge number of HTTP requests.
- The huge number of HTTP requests make the site/ server unresponsive and thus bring them down and inaccessible for use.
How to Perform HTTP flooding Attack:
- The flooding of HTTP requests is carried through bots which flood the computer with a huge number of requests. For each request to the server/ computer, thousands of unauthorized requests are flooded along with the user request.
- This huge volume of HTTP requests that flood the browser make use of bots that are supported by Trojan Horses for generating them.
- HTTP GET Requests are easy to create requests and make use of bots for generating a huge flood of requests. While the HTTP POST Requests, on the other hand, involve complex processing and are therefore not preferred over HTTP GET Requests to carry the HTTP flooding process.
The Appearance of HTTP Flooding Requests:
- HTTP flooding is an extremely dangerous form of cyber attack as the appearance of HTTP flooding requests makes them very difficult to distinguish.
- HTTP flooding requests appear like valid URLs and cannot be questioned or distinguished based on their appearance structure.
Prevention from HTTP Flooding Attacks:
It is very important to know the different ways in which HTTP flooding attacks can be prevented. Below are some of the ways listed to prevent HTTP flooding attacks:-
1. Computational Machines: Computational JavaScript machines can help detect if requests are coming from a bot and help in timely identifying flooding requests.
2. Web Application Firewall: The Web Application firewall will help in protecting from abnormal flooding of calls. Thus, securing the computer system from HTTP flooding attacks.




