Sniffers are software or hardware devices that can be used for wiretapping over a computer network, such as LAN or WAN. They are used to collect data by listening and capturing IP packets. These devices usually have the ability of recording data which includes email, chat, web browsing, and information about your phone calls.
- Sniffers are also known as network monitoring tools or network intrusion detection systems (NIDS).
- They can be made to sniff an entire network segment or a single computer or workstation.
- They can also be equipped with the ability to automatically follow a target MAC address from a bridge card to an interface on the victim machine.
- They can also scan for available wireless networks within range and associate themselves with one of them before moving on to capture traffic.
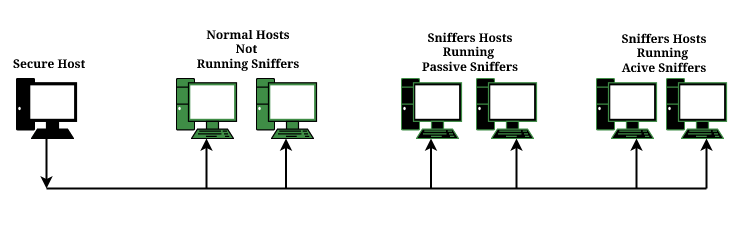
Types of Sniffing Attack:
Sniffing attacks can be used to gain unauthorized access to computer networks and monitor or alter network data. Sniffing is a method of monitoring network traffic in order to acquire sensitive information. This can also be done on Wi-Fi as well as wired networks without providing any credentials. Examples of sniffing include:
- Passive sniffing: This involves recording the activity of users logging onto the system and using that captured data for further analysis or unlawful purposes, such as identity theft or financial fraud.
- Active sniffing: This involves having an attacker install software on targeted parts of a computer’s operating system, like certain firewalls, servers, routers remote access services, etc., thus monitoring all traffic passing through it.
Sniffing Protocols and Technologies:
In the following section of this article, we will discuss some commonly used sniffing protocols and technologies.
IEEE 802.3: The IEEE 802.3 protocol is used for Ethernet, and it is a data link layer protocol used to transmit network packets between a station device such as a workstation, printer, or server and a host device such as a networking hub or switch. It works on CSMA/CD (Carrier Sense Multiple Access with Collision Detection) principles which mean that when more than one host sends a packet at the same time to the same destination, these packets collide with one another thus generating errors and are retransmitted until they reach successfully to their destination.
Detection of Sniffer in Your Network:
To detect a sniffer in your network, you need to watch out for the following signs, which will mean the presence of a sniffer.
- Presence of strange traffic and at a high rate:
Strange traffic is any type of transmission that doesn’t seem to make sense, like phone calls you don’t recognize, strange file transfers, or emails that are sent to you from unknown senders.
This is due to the fact that these transmissions will be ignored by legitimate users, but if they show up in your log file or alert notification center, it will be a sign of sniffer activity on the network. - Lack of proper firewall: One defense against sniffing attacks is to have a dedicated firewall that is not shared with other networks in your organization.
- Modification of your ARP tables: ARP (Address Resolution Protocol) is a technique used by the IP layer to map an IP address to a physical networking address.
- MAC spoofing: MAC spoofing is the practice of altering the Media Access Control (MAC) address assigned to your NIC. This is usually done intentionally so that it may be used on another network.
- Traffic flooding on different ports: Sniffers can be able to sniff data when it is sent over the network but if all ports are blocked, then they will not be able to acquire all data packets which means that some information remains secure from sniffers and their presence has been successfully detected and log file access will be prevented from them.
Key Points:
- Sniffers can be detected by watching out for strange network traffic and a lack of firewall.
- The IEEE 802.3 protocol contains frames that are used to transmit data on the Ethernet segment.
- MAC spoofing is a method used to allow machines to use a different and typically invalid MAC address for communication purposes so that sniffers may not be able to detect it and any information sent will remain secure from them.
- You can also use packet sniffer and packet analyzer software like Aircrack or Wireshark for detecting the presence of a sniffer in your network, especially if the sniffer is hidden from your eyes by using encryption hardware which makes it invisible to the network traffic (unlike default wireless access points).
Countermeasures:
- Encryption: It is the most common defense strategy against network sniffing. Encryption is a method of securing information by converting it from its original form to another form which can only be decrypted through the use of an encryption key or password.
- Firewalls: Firewalls are used to prevent unauthorized access to sensitive data on a network. Firewalls provide security control for networks, host computers, and individual users in a networked environment.
- Access Lists: Access lists define which users or systems can gain access to specific resources on the network. We sometimes refer to this as ACLs (Access Control Lists).
- Secure protocols: Many protocols can be made secure using various techniques like authentication, encryption, and authorization.
Conclusion:
With the information given in this article, you can start detecting sniffers in your network by taking some preventive measures. These measures can help you avoid getting inside your network and provide important information to unauthorized users. The presence of sniffers on the network may lead to security breaches which will result in the loss of valuable data among other problems. Having a good firewall and using encrypted protocols such as SSH (the Secure Shell) may also be a solution for sniffing detection.




