A botnet is a collection of compromised computers (called bots) residing on the internet that can be controlled by cybercriminals. Botnets are used for all sorts of nefarious purposes, from spamming to stealing confidential information from computers to launching cyber attacks on other websites.
The point is that unsecured wireless networks are a gateway for hackers and other malicious actors to gain access to your devices without your consent and make various changes. This post will show you how these networks work and give you some preventative measures you can take in order to protect yourself against them.
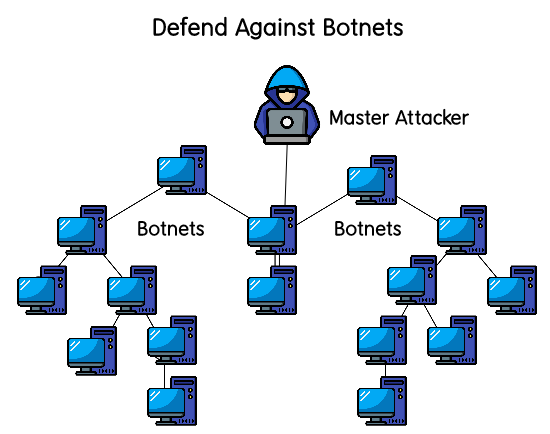
Types of Botnets:
There are two main types of botnets: local and remote. A local botnet is a botnet that resides on the same physical network as your devices (for example, your home or office network). Remote botnets are remotely located from your devices and can be on a totally different network.
1. Local Botnets: A local botnet is any computer that has been compromised by an attacker and can be controlled via a botnet command and control server. To create a local botnet, you need to compromise a computer that is connected to the internet, which requires the following:
- An attacker scans the internet for computers with unsecured wireless networks or open ports with weak passwords.
- Once a computer is compromised, the attacker has the ability to access your other computers and run malicious commands.
- It only takes one open wireless network or device with an open port to expose your entire network to an attack. Keep in mind that any computer connected to the same network as an infected device may also be vulnerable to attack.
The best way to prevent local botnets is by properly configuring your wireless router so that it’s not susceptible to attacks. The following tips will help you secure your router: - Use strong passwords on all the devices on your network, including your wireless router.
- Turn off all the unnecessary services on your wireless router, including FTP and telnet.
- Immediately change your administrative password if you suspect it’s been compromised.
- Disable remote administration on your wireless router so that other users cannot access it.
- Ensure that ports are closed (including the default ports: 23, 80, 443, 3389, 3306). Any open port is an open door for hackers to gain access to your computer.
- Change the default IP address of your wireless router to put some distance between yourself and a hacker who may be scanning the internet for insecure routers.
2. Remote Botnets: If you have sensitive data (e.g., credit card info, social security numbers, etc.) on your computer or laptop, you are at risk of having it stolen from you. An attacker can use a botnet to target a specific system and gain control of that device for the purpose of stealing valuable information. The best way to prevent remote botnets is by maintaining an up-to-date antivirus solution installed on your computer. Make sure that any antivirus solution has full virus definitions that are updated daily to stay ahead of the malware game. Also, make sure that you only download your software from reputable sources and never run any software that you aren’t familiar with. Other preventative measures are similar to those of local botnets:
- Keep your device (e.g., computer, laptop) patched and updated regularly. The less vulnerable your computer is, the less likely it will be hacked.
- Use strong passwords on all the devices on your network and change them regularly.
- Disable remote administration on all of your devices to avoid malicious attacks by unauthorized users.
- Stay aware of suspicious activity on your computer such as pop-ups, etc., and immediately quarantine questionable files until a virus scan has been completed.
- Do not open suspicious email attachments.
- Use encrypted data storage such as the KeePass non-cloud solution if you are storing valuable information on your computer.
- Encrypt your entire hard drive using disk encryption software like TrueCrypt to prevent unauthorized access to your data in case of a physical loss or theft of your device.
- Firewall your computer to avoid malicious attacks by hackers attempting to exploit vulnerabilities in your system.
- Keep all the applications and services on your computer patched and up-to-date. Keep in mind that a program is only as secure as its weakest link, which is why it’s important to keep everything patched and updated regularly.