Code Access Security is an extremely important concept and one that all ethical hackers need to know and understand. This is the way in which Windows can be configured to determine what code execution should look like, either allow everything, allow only signed code, or allow only certain users to execute different code.
Main Content:
Code Access Security is used to ensure that code that is designed to be run on computers is more secure. This protects the systems from viruses, worms, and other types of malicious code. The process of Code Access Security helps keep the system safe from unauthorized access, and it can also firewall out some attacks.
In order for Code Access security to work effectively, it must be configured properly before it is used. One main function of Code Access Security is to ensure that only trusted code can execute on a computer. In order for code to become trusted, the following steps must be completed:
- The publisher must sign the .Net assembly using a strong name key file (snk file) or by using a strong name.
- The .Net assembly must be present in the Global Assembly Cache (GAC).
There are several default rules that are automatically set for all assemblies. These rules are:
- All code is unverified, which means it cannot be run.
- No permissions can be granted to the code to be run on the system. This effectively blocks code from running. This can’t be changed unless you alter the security configuration for the system on which this code is being executed, or you change these default rules by using Code Access Security Policy files.
Examples of Code Access Security:
A company may want all the code that it owns and creates, to be able to run on a system. It can create a Code Access Security Policy file with special permissions that will allow the code that it signs and creates, with strong names, to execute properly and securely. This way, the company will have more control over its own assemblies, rather than allowing all of their assemblies to run on the system with default permissions. It is also possible to allow more than one type of Code Access Security Policy file to run on a system at any given time.
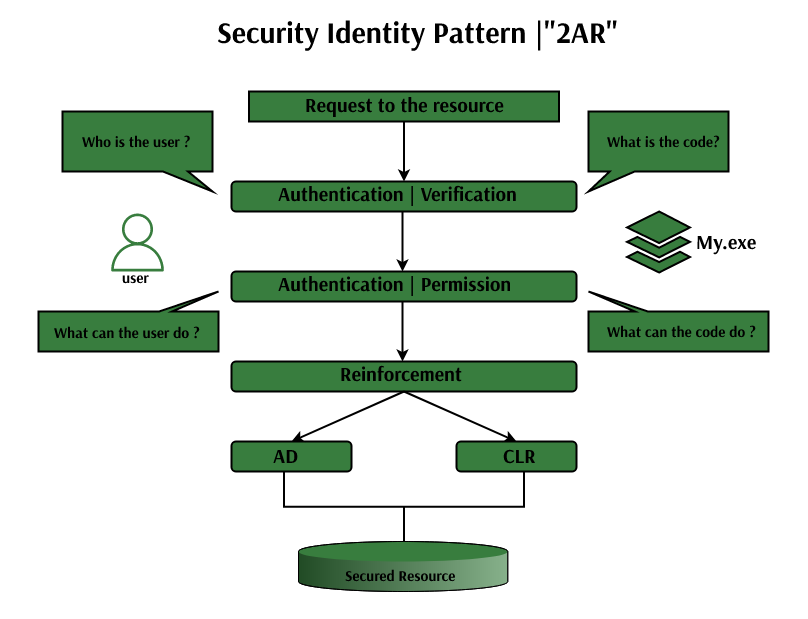
Elements of Code Access Security:
Each security framework needs a component, (for example, client name, secret key, etc.) to differentiate the clients and figure out what a client should or shouldn’t do. CAS separates and appoints consents to applications instead of individuals. It distinguishes congregations utilizing proof. Every component is the way that a gathering can be recognized, for example, area, hash code, and the mark of the get-together. The proof is the data that the runtime collects about a gathering to decide in which code groups the gathering has a place. Code groups thus acknowledge a gathering of a consented set. There are three primary parts of code access security.
- Proof code
- Gathering
- Authorizations
Types of files used in Code Access Security:
- Any of these files can be used as custom security settings to make sure that only trusted code will execute on a system. For example trusted code will only run if it is signed with a strong name key file, or you grant specific permissions using the special permission registry entries.
- Code Access Security Policy Files are files that control how Code Access Security works on a computer. These files are used to let Code Access Security know how to run code. They are used in order to either allow or block certain code from running on the system.




