There are currently 592 payload modules in the latest Metasploit Framework release. Before moving forward let’s begin with what is payload and basics of payload, Payload is a code that will be executed on the system and decides what to do after launching our exploit.
Check Availabilities In Metasploit:
After opening msfconsole, metasploit provides a great database of all kinds of exploits. For example, you can use the command search type: exploit platform: Unix to search exploits for Unix systems.
You’ll get a large list of potential exploits to attack your target. And commands such as those given below can be used directly in the console.
use exploit/unix/local/chkrootkit
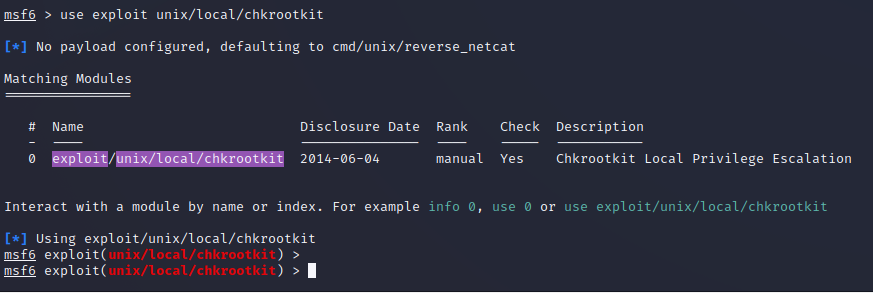
There are many payloads that are available in Metasploit, so it might be overwhelming to figure out which payloads you can use for specific exploits. Luckily, you can easily view the payloads that are supported for an exploit.
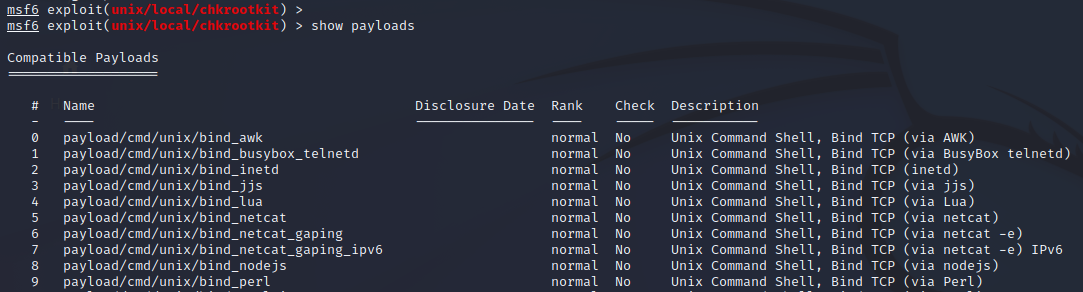
After you choose an exploit, you can run the following command to view the payloads that are available:
show payloads
How To Use a Specific Payload?
To use a specific payload in your exploitation, use the following command
Set PAYLOAD Payload-name Example: set PAYLOAD windows/adduser
Multi handler is the one and only exploits which can handle all the available payloads in Metasploit. It can deal with all the payloads no matter what the purpose of the payload is and how the connection is being established. It is the backbone of Metasploit for exploiting the targets.
Meterpreter:
The meterpreter payload is the most powerful weapon in the Metasploit framework. It can do various tedious tasks. It can log all the keystrokes, take screenshots, obtain hashes, set itself to be persistent on reboot, migrate to other services, see the process IDS, kill the processes, etc.
VNC Injection:
This is a pleasant payload that gives you a graphical user interface to control the remote system.
thatWorking:
The VNC Injection payload sends a small VNC server to the Windows system we are attacking and then connects to that VNC server. As we discussed meterpreter is a powerful payload we can use to get an interactive shell. Here we would like to present some key options we can use in meterpreter. Descriptions took from the help menu of meterpreter.
| Command | Description |
|---|---|
| Migrate | Once we exploit a process, we will get privileges that exist in that process. If the user suspects & terminates it, then we should re-gain control again. So before the victim suspects our process we should migrate to another trust process that has more privileges like “explorer.exe” |
| Help | Among many commands, we are listing only a few here. If you use the “help” command it gives a complete list of commands it does support. |
| Channel | Displays information about active channels |
| Exit/Quit | Terminate the meterpreter session |
| Info | Displays information about a Post module |
| Load | Load one or more meterpreter extensions |
| hashdump | Dumps the contents of the SAM database |
| Read | Reads data from a channel |
| Write | Writes data to a channel |
| File system Commands | Cat, CD, del, download, edit, getlwd, getwd, Icd, Ipwd, Is, mkdir, pwd, rm, rmdir, search, upload |
| Networking Commands | Ipconfig, portfwd, route |
| System Commands | Clearev,drop_token, execute, getpid, getprivs,getuid, kill, ps, reboot, reg, rev2self, shell, shutdown, steal_token, sysinfo |
| User interface Commands | Enumdesktops, getdesktop, idletime, keyscan_dump, keyscan_start, keyscan_stop, screenshot, setdesktop, uictl |
| Webcam Commands | record_mic, webcam_list, webcam_snap |
| Elevate Commands | Getsystem |
| Timestamp Commands | timestamp |
There are many payloads available, but we are discussing only some of those.(description from metasploit), for the remaining payloads along with the description you can find them in the List of Payloads.
| MetaSploit | Description |
|---|---|
| adduser | This payload is used to add a new user to the target system. |
| shell_bind_tcp | Listen for a connection and spawn the command. |
| shell_reverse_tcp | Connect back to the attacker machine and spawn a command shell. |
| speak_pwned | Victim PC says You got pwned. |
| upexec->bind_tcp | Listens for a connection and Uploads file and Runs it. |
| metsvc_bind_tcp | Stub payload for interacting with meterpreter service. |
| dll-inject | Injects DLL |
| VNCinject | Injects a VNC dll, So we can connect to the victim with VNC. |
| exec | Execute an arbitrary command. |
| message box | Prompts a message box with user-desired data. |




