Stuxnet is a powerful and malicious computer worm that first appeared in 2010. It is also reported to be the largest and most expensive malware of this type. It exploited a previously unknown Windows zero-day vulnerability to infect the targeted system and spread to other systems. The virus primarily targeted separators at uranium enrichment plants in Iran. However, cyber attackers have modified and adapted it over time to attack other facilities, such as power plants and gas pipelines. No country has officially acknowledged the development of Stuxnet, but it is widely believed that the United States and Israel co-developed the worm. Stuxnet was the first virus to physically destroy an infected device. The malware seriously sabotaged Iran’s nuclear program, but due to its aggressive nature, it inadvertently spread beyond Iran’s nuclear facilities. However, it did not cause any significant damage to external devices outside its original target area.
Working:
Stuxnet is an intelligent and intrusive malware. However, it has been carefully designed to only affect targets in a specific configuration and cause minimal damage to other devices. Because the nuclear facilities were intentionally air-gapped and isolated from the global network, Stuxnet was most likely transmitted via USB sticks carried by agents within these facilities. It contains man-in-the-middle code that spoofs sensor signals to avoid shutting down the target system due to anomalous behavior. It’s also unusually large, written in a variety of programming languages, and spreading rapidly.
Stuxnet targets three system layers:
- Windows operating system
- Industrial software applications for Siemens PCS 7 and WinCC
- Programmable Logic Controller Siemens S7
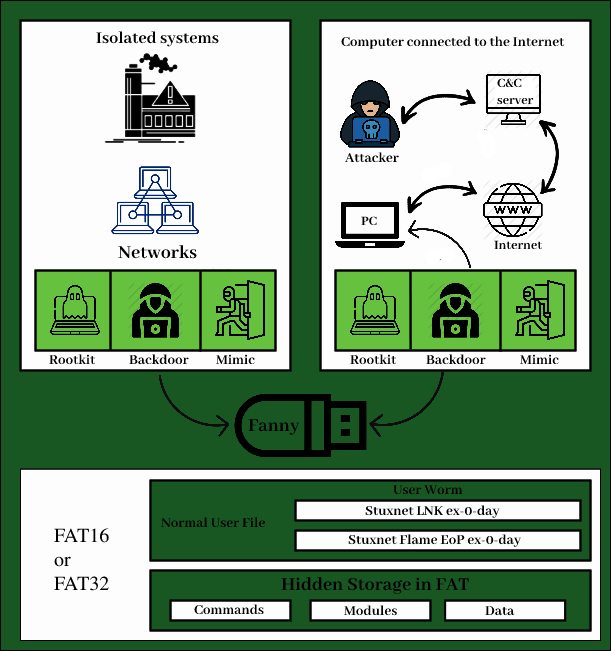
Impact of Stuxnet Virus:
Stuxnet is considered the largest and most expensive malware development project in history, too big for anyone but the state to create. It was also too accurate to damage anything other than equipment used only at Iranian uranium enrichment plants. Stuxnet contained a valid security certificate stolen from a legitimate software company and some of his zero-day exploits infected the technician’s girlfriend’s PC. This combination allowed Stuxnet to easily compromise a PC once an infected USB stick was plugged into his USB port. However, these three approaches highlight the vast resources at the Stuxnet developers’ disposal. A valid security certificate is well protected. Zero-day exploits (vulnerabilities unknown to the software vendor in the software being exploited) are extremely difficult to find. A single zero-day exploit is rarely found in malware. At the time, it was unthinkable to associate multiple malware with a single malware. Finally, linking an attack to the acquisition of a physical USB stick by a technician guarded by heavy security measures requires extraordinary skill.
Subsets of Stuxnet Virus:
Stuxnet has had a major impact on future malware development. Here are some legacy Stuxnet examples:
- Flame: Flame is sophisticated spyware that also targets Iran and other Middle Eastern countries. It was primarily targeted at educational institutions and government agencies.
- Havex: It is primarily targeted at Western countries, but with similar intentions. Spy on aviation, defense, energy, and pharmaceutical companies.
- Duqu. Duqu is a collection of computer malware that also exploits zero-day vulnerabilities on Windows. It is very similar to Stuxnet and also targets Iranian nuclear organizations. Businessman.
- Triton: Triton targeted a petrochemical plant in Saudi Arabia. Dubbed “the deadliest malware in the world,” Triton can cause system failures.
Key Points:
- Stuxnet is a malicious computer worm that many experts believe was jointly created by American and Israeli intelligence services.
- The worm allows the attackers to break into industrial control systems, such as those that manage the flow of power in electrical grids, gas pipelines or nuclear plants.
- The virus can cause these devices to malfunction if it detects them running on what its designers think are Windows 2000 or XP operating systems – typical outdated software in many for-profit industries.
- Stuxnet is unlike normal malware because it causes physical damage to equipment under certain conditions.
- It might have been designed to cause dangerous malfunctions in power plants and other infrastructure by severely damaging their hardware.
- The worm is a sophisticated piece of malware with a large number of advanced features to accomplish this.
- One such feature is the ability to change its signature within that software, making it very hard to detect.
- Stuxnet displays malevolent software behavior and can keep running even if certain antivirus programs are installed.
- In addition, Stuxnet masquerades itself as a normal Microsoft file that does not seem suspicious at first glance. People who notice it on their hard disk will not suspect that it is a malicious program. It’s very akin to a terrorist who disguises themselves as an ordinary citizen in order to plot an attack.
Conclusion:
The actual identity of the authors of the Stuxnet attack seems likely to remain a secret forever. However, in the wake of Stuxnet, America and Israel have been working together with new vigor to increase cyberwarfare capabilities. In other words, it is expected that future malware will come from this partnership between these two countries in order to fully understand how computers work.




