Source Port Randomization for Caching DNS is a technique used in the Domain Name System, which is a set of text files that translate alphanumeric domain names like “google.com” to numerical IP addresses like “74.125.79.125”. It is important because DNS is one of the most common ways to get around firewalls and proxy servers, which makes them useful in malware, and cyberattacks. When source port randomization for caching DNS is enabled on a local computer’s TCP/IP setup or firewall settings, it can make it difficult for these networks to target the computer for malicious activity because they would not be able to predict what its source port will be each time it connects with them.
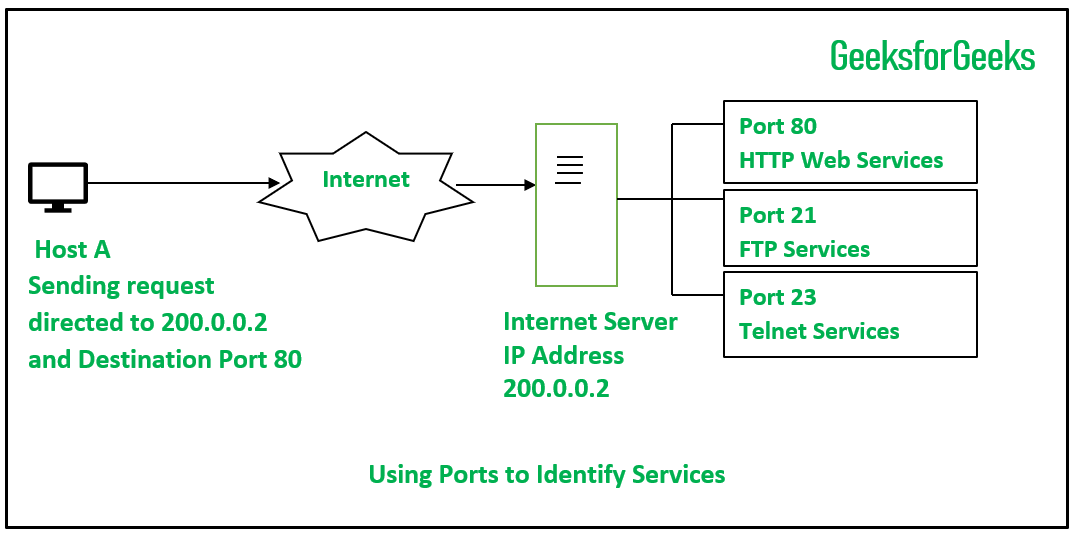
If you are running a caching DNS server, you should enable source port randomization (also called UDP source port randomization or UDP/TCP source port randomization) to protect the DNS resolver from spoofing attacks that can use any randomized and predictable mapping of the TCP/UDP ports on the server to query TCP-based DNS resolvers.
Working:
The following is a list of terms for those who wish to know more about what this is:
- Source Port Randomization: The process in which an incoming packet, such as a DNS query, is assigned an IP address and/or port number other than one implied by the underlying protocol.
- Spoofing attack: An attack where an attacker impersonates another person, computer, or network in order to gain access to information.
- UDP: The User Datagram Protocol is a connectionless protocol for sending packets of data. Unlike TCP, UDP does not guarantee delivery nor does it guarantee the ordering of data that is sent from one machine to another over the internet.
- TCP: The Transmission Control Protocol is a connection-oriented protocol that provides guaranteed delivery of data sent over an IP network. It also provides a mechanism for detecting and recovering from packet loss and error conditions on a transmission channel.
Source Port Randomization for Caching DNS is a technique used in the Domain Name System, which is a set of text files that translate alphanumeric domain names like “google.com” to numerical IP addresses like “74.125.79.125”. It is important because DNS is one of the most common ways to get around firewalls and proxy servers, which makes them useful in malware, child pornography, and cyber attacks. When Source Port Randomization for Caching DNS is enabled on a local computer’s TCP/IP setup or firewall settings, it can make it difficult for these networks to target the computer for malicious activity because they would not be able to predict what its source port will be each time it connects with them.
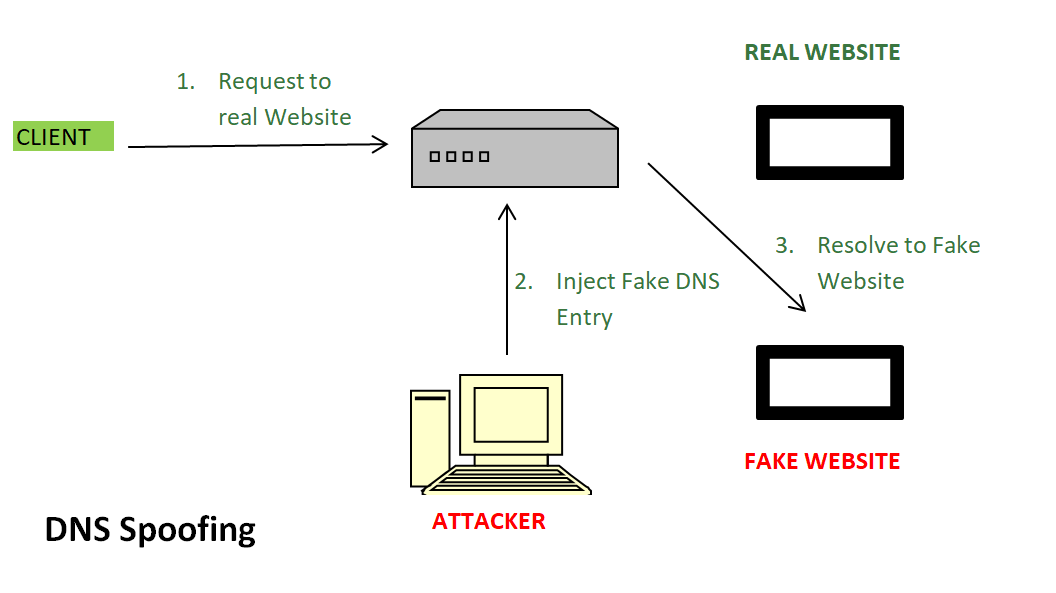
Key Points:
- If a DNS server is not randomizing the source port, it is allowing possible DNS spoofing attacks.
- Spoofing attacks are very useful for attackers to find out the IP address of a computer and gain information about that computer such as usernames, credit card numbers, passwords, etc.
- Network administrators and security professionals who use DNS in their networks should be aware that some network devices do not pass the IP source port to the resolver stack when they query a DNS server.
- They often do this by default because they are expecting either TCP or UDP requests and do not realize that the gotipc and gotdns packages will make all queries look like UDP to them.
Countermeasures:
- Enable randomization of the source port on the DNS server.
- If you are running a caching DNS server, you should enable source port randomization (also called UDP source port randomization or UDP/TCP source port randomization) to protect the DNS resolver from spoofing attacks that can use any randomized and predictable mapping of the TCP/UDP ports on the server to query TCP-based DNS resolvers. Note that this will not help if attackers have compromised your cache.
Conclusion:
When Source Port Randomization for Caching DNS is enabled on a local computer’s TCP/IP setup or firewall settings, it can make it difficult for these networks to target the computer for malicious activity because they would not be able to predict what its source port will be each time it connects with them.




