A proxy Trojan is a type of computer virus that disguises itself as something else, such as a harmless file or website. When a user accesses it, the proxy Trojan hijacks their browser and sends the user to bogus websites or downloads malicious files. Proxy Trojans can be used in two ways: for stealing information (including passwords) from unsuspecting users, and for launching attacks on other computers. Proxy Trojan is a manipulative program that can be used for a variety of destructive purposes. Its primary aim is to steal sensitive data by infiltrating targeted devices and extracting confidential information. It can be used in a variety of ways- as a spy, or a virus.
Working:
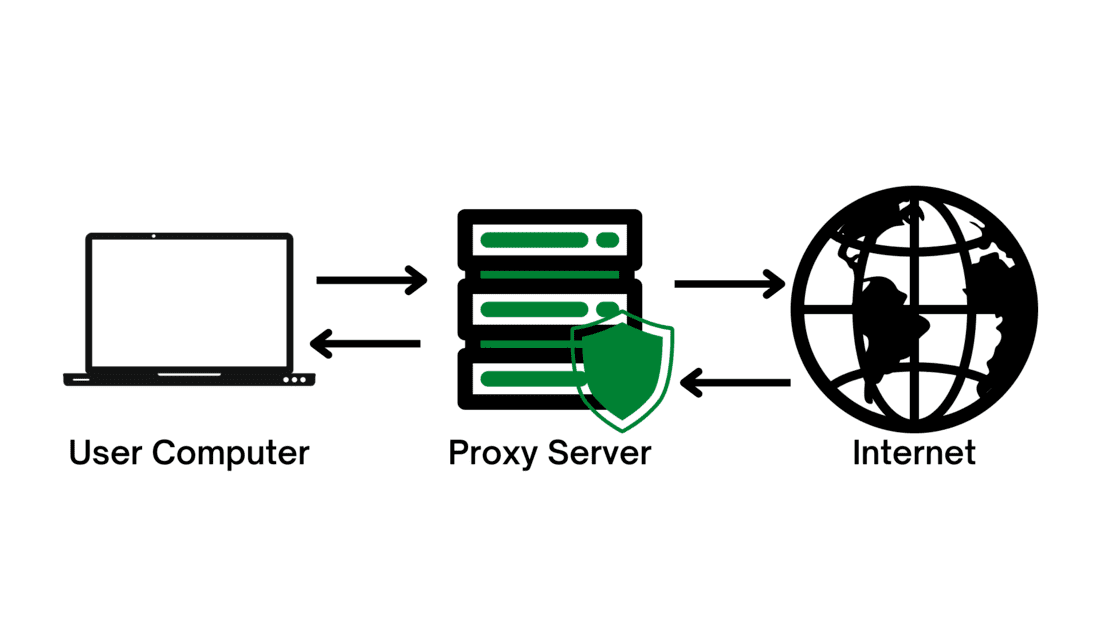
Proxy Trojans first invade devices by infiltrating legitimate apps or websites that are used by the target user. Once they are installed, they start to actively seek out sensitive data, such as credit card numbers, login information, and even passwords. They use various stealth techniques to avoid being detected, and once they have collected the data they want, they typically delete their presence from the infected device. The proxy server has its own IP address, which is known to the user’s computer and through which communication between the server and the user’s computer takes place. When a user’s computer sends a web request, the web request is first sent to the proxy server. A proxy server sends requests to the Internet on behalf of a user’s computer, then collects data from other servers and serves it to the user. Because a proxy server can change a user’s IP address, other web servers cannot obtain a user’s location on the Internet.
Trojan:
A trojan is also known as the Trojan horse virus. It is a type of computer malware that does not replicate like viruses and worms. It is the malicious code that hides in the system and steals the user’s important information or controls the user system. When a user downloads unknown software or clicks on an unknown link, then there is a chance for a Trojan virus to get into the user system. After entering in the system, it starts controlling and taking significant information from the system like email and passwords.
Proxy Trojan Features:
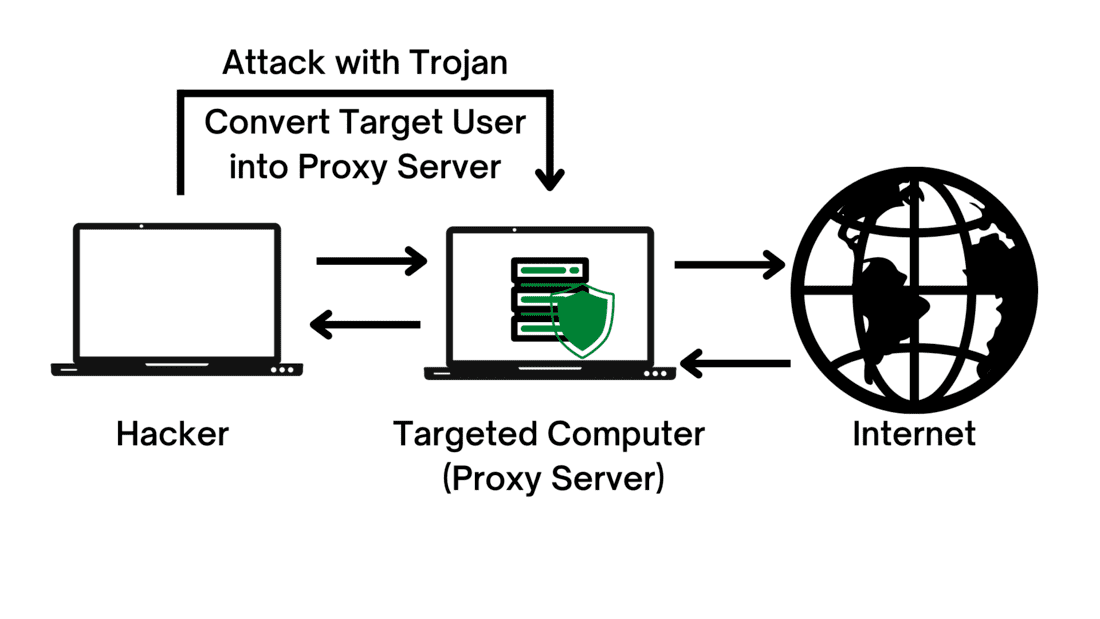
- Proxy Trojans are malicious code specially designed for hijacking, which turns the target user’s computer or device into a proxy server.
- It gives hackers full access to the user’s computer or device. Hackers can then use the hacked device for a variety of illegal activities like credit card frauds, cyber-attacks on other devices, etc.
- Proxy Trojan also has a special feature that helps hacker in hiding the actual location of the original host device (target user and hacker computer location).
Preventive Measures:
Below are some preventive measures:
- Regularly back up your files to help reduce data loss.
- Updating the operating system from time to time helps protect the system from security breaches.
- Never click on unwanted links or download unwanted files. Phishing emails are one of the methods which hackers use to spread Trojan horses or other malicious viruses.
- Use 2-factor authentication to protect sensitive information or account.
- Use a security suite and antivirus software to protect your device or computer from all known and unknown viruses, malware, etc.