Cyber security is the security of the web and related services related to the web. Cyber security is the way to prevent many cyber attacks from taking place. Cyber security ensures that awareness of the cyber-attacks along with the different forms of cyber attacks are well-known to people so that they can prevent the cyber attacks from taking place. Cyber security also makes the computer network users aware of the norms they must follow if they ever get stuck in any kind of cyber attack so that the users can deal with the cyber attack efficiently. The different types of cyber-attacks that cybercriminals adopt are dependent on the vulnerability of the computer network they want to target. It thus becomes important to know about the cyber attacks, the mechanism involved while executing cyber attacks, their types, and preventive ways behind the cyber attacks.
Port Stealing Attack:
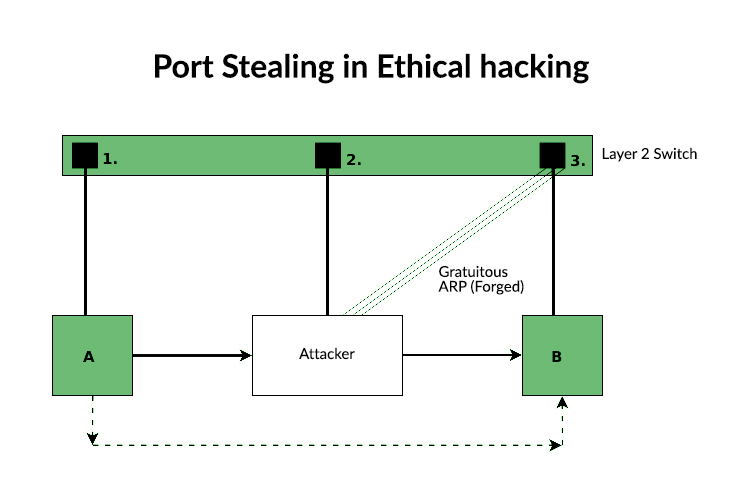
Port stealing is a man-in-the-middle attack via a LAN switch. It attempts to intercept packets sent to another host by stealing the switch’s port from the desired host. This attack is intended to be used only on the local network. The attacker uses the victim’s stolen MAC address to force the switch to modify the forwarding table. Packets sent to the victim’s computer are sent to the port to which the attacker is connected. (Ettercap) From this point on, an attacker could read the information in the packet, cause a delay, or prevent the packet from reaching the victim. Port stealing uses a switch The connection between the MAC address binding and the physical port itself.
Key Points of Port stealing Attack:
- A Port Stealing attack is a very dangerous cyber attack as it involves stealing the traffic that is assigned to a port in a computer networking.
- Port stealing attack got its name as it steals the original port of the user and directs all the traffic to the attacker’s port.
- Unknowingly, pretending as the original port – the data gets stolen and all the confidential information is passed to the attacker.
- Port Stealing attack makes the computer network represent a legitimate user’s identity by sending a fake MAC address as their source address.
Mechanism of Port Stealing Attack:
- Port Stealing attack is another form of a Man in the Middle cyber attack. Here, in this attack, the attacker aims of getting access to internal confidential information and packets.
- Port Stealing attack is based on the machine where the user’s MAC address forcefully manipulates the switch behavior of managing the forwarding table.
- The switch has the tendency to transfer the frame to the authorized owner of the MAC address.
- When the cyber attacker does the work of sending huge frames to the computer system, the system then unknowingly regards the last frame of the attacker as correct and leads to the sender transferring its data to the attacker based on this unwanted misconception.
Prevention from Port Stealing Attack:
Port Stealing attack can be prevented by proper vigilance of the attack and by following below preventive ways to prevent attackers to enter the computer system through port stealing -
- Timely updating present Switch address: Keep updating the address of the switch on regular basis. This makes the address a less vulnerable target to cyber attackers.
- Making use of good quality switches: Ensure using of enterprise-grade switches, which prevent any kind of malicious attack that may result in port stealing.




