When someone tries to access any part of our personal computer system then PC intrusion occurs. Every Personal Computer (PC) which is connected to the internet is a target of hackers and cybercriminals.
There are several ways an intruder can try to gain access to your computer. They can :
- Access your computer to view, change, or delete information from your computer: Once the attacker got access to the computer, initially attacker will attempt to view the information, if the information is valuable attacker may sell the collection information to gain financial benefits. An attacker may delete or change information if the objective of the attack is to distract the smooth functionality of computer.
- Crash or slow down your computer: The system may get crash if the attacker deletes system files, bootstrap loader file, bootstrap loader file is responsible to load the operating system. System performance may get slow if the system file is deleted or modified.
- Access your private data by examining the files on your system: Once the attacker got access to the system, he may access private or sensitive data of the system. After analysis of this data, an attacker may get valuable information that may be misused or sold to a third party for financial gain.
- Use your computer to access other computers on the Internet User’s computer is connected in network, if the attacker got access user’s system. He may use the user machine to get access to another network machine by executing various commands such as ping, traceroute, dig, etc.
Personal Computer Intrusion can occur in any of the following forms:
- Sweeper Attack: Cybercriminals erase all the information or data like cache, cookies, internet history, or documents from the system by a malicious program.
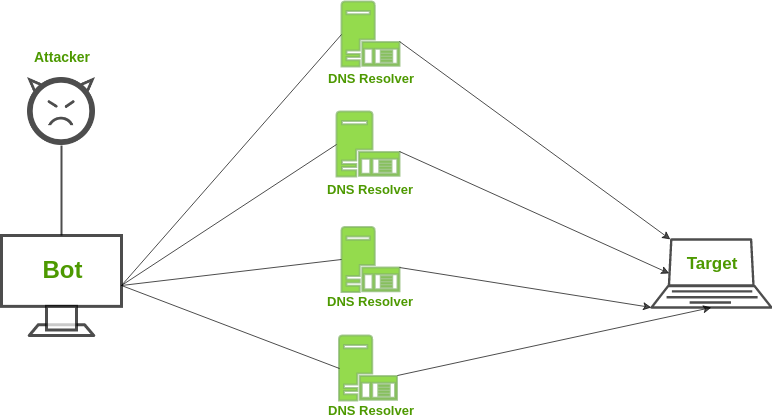
- Denial of Services: DDos type of attack in which attackers may shut down the PC services making it irascible to its original user. All the system applications and stored resources come to a halt.
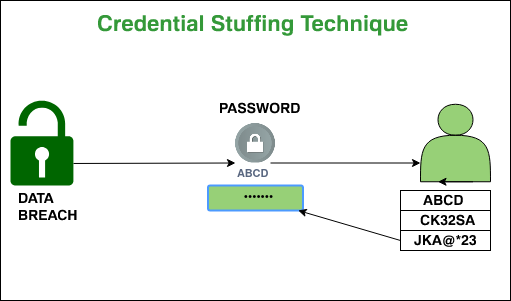
- Password Guessing: Most hackers crack passwords of system accounts by guessing and gaining remote entry into our personal computer system. Hackers can use this form and may damage the security system in our PC.
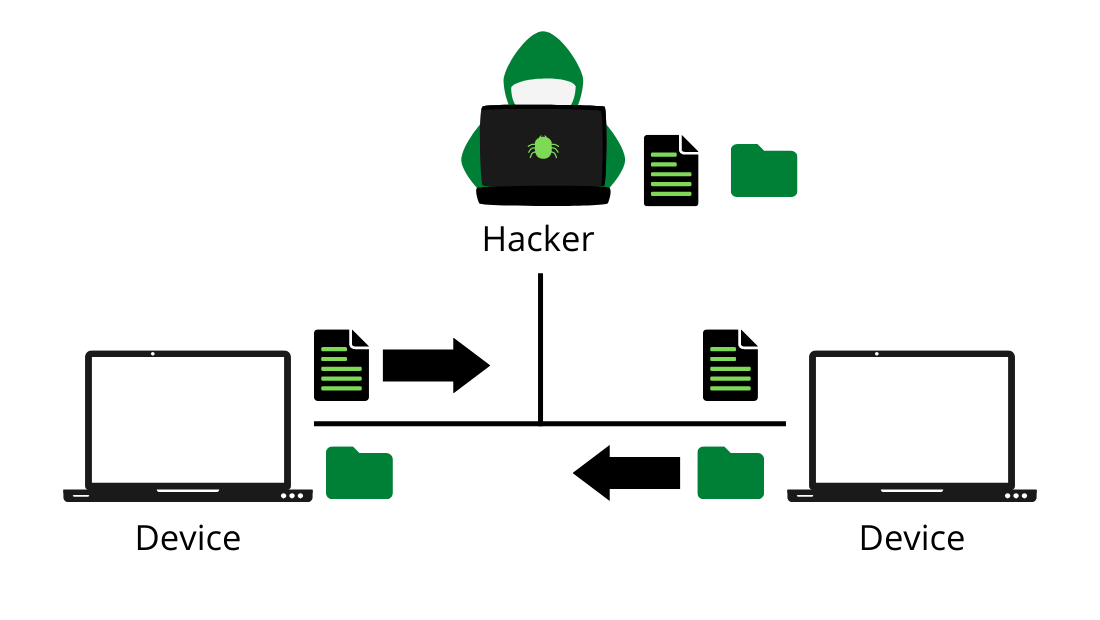
- Snooping: Snooping refers to opening and looking through files in an unauthorized manner. Snooping may involve many types of things such as gaining access to data in an unauthorized way, casually observing someone else’s email, or monitoring the activity of someone else’s computer through sophisticated snooping software. It involves monitoring keystrokes pressed on the keyboard, capturing of passwords and login information, interception of emails and other private communication, and data transmission.
- Eavesdropping: When cyber vandals or attackers listen to a conversation that is traveling over devices like computers, servers, or other network devices, it is called eavesdropping. Formally we can say that the intentional interception of someone else’s data as it passes through a user’s computer to a server or vice-versa is called eavesdropping.




