Non-electronic password attacks are forms of hacking that seek to bypass any form of authentication or authentication system. Typically, a non-electronic password attack will use an automated script to probe for passwords on the network. One way this may be done is by placing port scanning software on an access point, expecting to gain access without being noticed by the intended users. Another way is through social engineering. In this case, intelligence services send phishing emails or send malware through apps like WhatsApp and Viber, which would then attempt brute force login attempts on the networks they are sent from. Due to the nature of these attacks, this is where effective countermeasures come into play. Most large corporations or organizations will have security teams that are tasked with reducing the chances of an attack from occurring in the first place through a number of means.
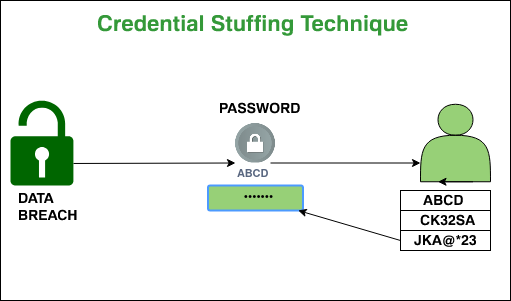
Non-Electronic Password Attack on a System:
One way to reduce the effectiveness of a non-electronic password attack is to introduce two-factor authentication. Two-factor authentication typically consists of a password, as well as some sort of physical or digital token that can be used in order to prove your identity. Whilst this may not completely stop those who wish to do harm from attacking the company, it will make it much harder for them. This is because two-factor authentication requires more than just a password, in this case, access to the token linked to your account. This means that whilst it does not prevent a non-electronic password attack from occurring, it will help to reduce the chances of an attack succeeding.
Another way that some companies try to combat these kinds of attacks is by constantly changing their passwords. To keep employees from writing them down or having to remember them, they are changed frequently by corporate policy. Due to the fact that these passwords are often still traditional alphanumerical strings, they can be cracked by brute force. One way around this is to implement a password policy where you have longer, much more secure passwords. These password policies should also include things such as changing the character case or requiring digits along with letters in the password string. Another way to combat non-electronic password attacks is through the use of VPNs and other forms of encryption. By using forms of encryption, an attacker will either not be able to intercept your traffic or will have significant difficulty doing so.
Key Points:
- Non-electronic password attacks are typically carried out through brute force or social engineering.
- Non-electronic password attacks are typically stopped by the use of two-factor authentication and constantly changing passwords.
Countermeasures:
- 2-factor authentication.
- Long, complex password policy.
- Encryption.
- Use 2FA with a strong password and remember how to reset it. Use encryption. (Not sure of the best one, but this is key!) Keep your system up to date as much as possible.
- We want to limit an adversary’s ability to move laterally. Be careful when opening email attachments, and use antivirus software.
Conclusion:
Non-electronic password attacks are a serious risk to computer security, and should not be taken lightly. This is both due to the ease with which they can be perpetrated and the number of attacks that take place. Although it may seem an unlikely attack at first, well-intentioned employees may inadvertently be caught up in such an attack themselves. To prevent an attack from occurring, you can do a number of things. This includes implementing two-factor authentication as per above, or simply changing your password on a regular basis. Keeping systems updated and running antivirus software will also go a long way in keeping your systems secure from harm.




