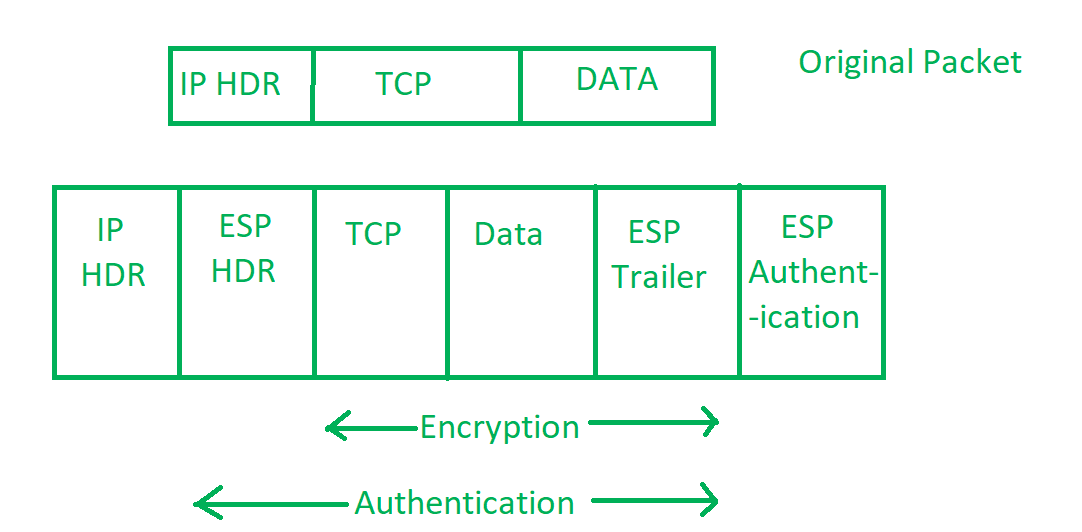
In the world of computer hacking, IPsec enumeration is a process by which attackers are able to perform authentication on an IPsec system. It can allow them to gain access to the network and gather information.
IPsec Enumeration:
IPsec’s enumeration is the process of gaining access to security keys by determining the possible encryption algorithms that are being used. It is done by determining what key can be used for each IP address, based on public information. IPsec relies on a shared secret for its authentication and encryption. The trick is to find out what that shared secret is, by making a request using an unknown IP address and checking whether you get a response.
Enumeration process:
Most of the time when someone performs this type of attack, they will verify various keys until they find one that works. As a result, the attacker can determine everything about a computer’s public and private IP addresses, as well as the encryption methods used. They will also be able to get information about whether an individual certificate is trusted by security appliances. How is it done? There are two ways that this type of attack can be carried out:
- Manual/Active: To carry it out manually, you first need to get the public IP address for the machine you want to hack. Next, you will send a packet with an unknown key, and receive a reply if the key works. If there is no response, then you need to try different keys until one works.
- Passive: To do this type of attack passively, all you need is access to a trusted security device that offers monitoring services in order to obtain information about IPsec keys and other encryption algorithms.
Prevention:
Ensure all possible IPsec keys are being used: There are some organizations that have a significant number of IPsec keys, and it is easy for an attacker to determine them all. You need to ensure that all possible keys are being used. This will make it harder for attackers to guess the right key. Use certificate pinning or authenticated encryption: If you use certificate pinning, you will ensure that only specific certificates can be used when encrypting traffic. In addition, this will ensure that packets are only encrypted using trusted certificates. Authenticated encryption is similar in nature, as it allows you to use specific encryption keys.
Some common defenses against IPsec type of attack:
- Use a hardware token. This will cut down the amount of time it takes to get an unknown key and also protect against man-in-the-middle attacks.
- Shorten the lifetime of the keys
- Change the encryption algorithm used in IPsec. The majority of firewalls and intrusion detection systems (IDS) will rely on a pre-configured list of algorithms that are allowed to be used with specific public keys. If you change your algorithm config, most IDS won’t be able to detect it as it is still in your standard list (which has not been updated).
- Don’t use the same security key for PPTP and L2TP/IPsec transmissions. This way, an attacker won’t be able to perform a man-in-the-middle attack on your PPTP server and initiate an L2TP/IPsec connection with the user for which, he has the encryption algorithm.
- Make sure that your firewall hides private data from other networks. This is why it is important to keep an open mind about the new and unproven firewalls such as Untangle or pfSense. These firewalls can hide Private information from other networks once you set them up correctly from your internet connection.
Conclusion:
IPsec Enumeration is an attack in which hackers are able to crack encryption codes via trial and error. Currently, it is one of the most popular methods for hacking into computer systems. However, there are a number of defenses that can help you protect your network from this type of attack.