Heartbleed bugs are categorized as Common Vulnerabilities and Exposures, the standard information security vulnerability name managed by MITER as CVE-2014-0160. This is a buffer over-read-if the system allows data access, that should be restricted. This allows an attacker to steal the private key of the server certificate. If the server version is vulnerable to heartbleed, cybercriminals can obtain the private key and impersonate the server. The results can be quite disastrous, as it makes it impossible to connect securely to the server and personal information can be easily disclosed. By exploiting the heartbeat option and not performing proper boundary checks, an attacker can gain access to personal information such as names and passwords and private keys that encrypt transmitted content. Breaches can include primary and secondary key materials, actual content, and promotional materials.
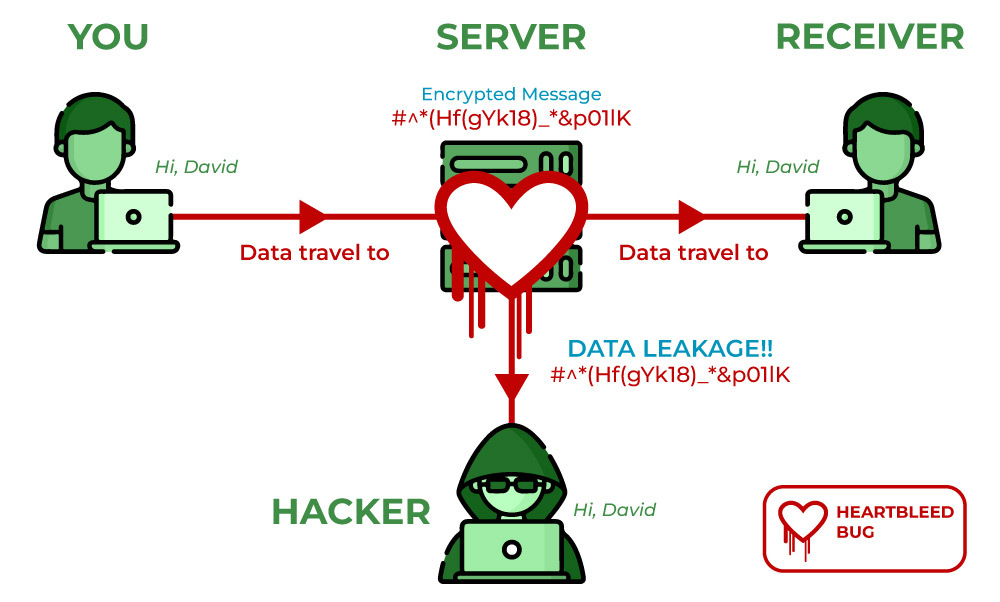
The primary key material is an encryption key that allows decryption of traffic, and the secondary key material means credentials such as username and password. Content can include emails, instant messages, documents, social security numbers, medical records, and financial information. Promotional material can include technical details such as security mechanisms and memory addresses.
History:
- The vulnerability was individually identified by the Codenomicon Security Engineering team, which consists of Riku, Antti, and Matti, and Google Security’s Neel Mehta, who reported to the OpenSSL team.
- Codenomicon’s security research team discovered a major security flaw while working to improve the Safeguard capabilities of the Defenses security testing platform.
- They reported it to the Finnish Department of Transportation and informed OpenSSL, which had already happened in the meantime.
- Engineers at the Finnish cybersecurity firm Synopsys Software Integrity Group have dubbed the error as “heartbleed” and created a special website to inform the public.
Working:
- OpenSSL is one of the most common SSL implementations that allows systems to communicate using SSL encryption technology.
- Open source projects have been around since 1998 and are becoming very popular. It is primarily developed by volunteers and is attended by at least permanently active developers to review the contributions of the developer community to the project.
- A vulnerable version of OpenSSL has existed for more than two years since March 2012, before the flaw was discovered and disclosed. As a result, systems running earlier versions of OpenSSL (prior to 1.0.1) were not vulnerable.
Countermeasures:
- Updated OpenSSL to version 1.0.1g, fixing the heartbleed bug on servers of your organization.
- In case you are running cloud servers, check with your hosting provider if they have updated their OpenSSL installation recently.
- Change all the passwords that could have been compromised by exploiting this vulnerability.
- Connections should be terminated to the vulnerable systems (once their respective administrators have updated the OpenSSL installations) until new passwords can be issued for them.
- All the systems (including routers and firewalls) that are configured to use automatically generated or pre-shared keys must be changed immediately in case they were using older versions of OpenSSL.




