An identification attack is a type of social engineering attack in which the attacker tries to gain information from public sources such as public records and directories, data listings from websites and social media sites, or through research. This is a form of information gathering that is done for any number of reasons, however, this type of attack should not be confused with the more targeted attacks that are generally done to more specific target groups.
The goal of an identification attack can range in its importance depending on who’s being targeted. The attacker might want to get information that they could use in more targeted attacks on more specific groups of people. If the victim is a high-level executive, the attacker may not care about getting information; however, if the intended victim is a less important member of society, such as a rookie cop or administrator at an organization, then the attacker will care greatly about gathering any and all publicly available information that can be used to identify them.
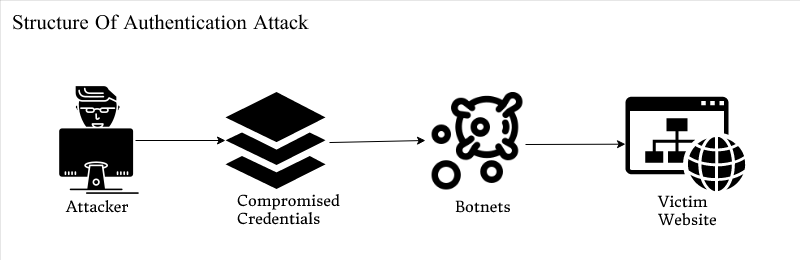
Types of Identification Attacks:
- The difference between social engineering and identification attack is that social engineering involves persuading someone with which some sort of incentive (such as money, goods, favoritism and social status).
- An identification attack is simply targeting someone and gathering as much information on them as possible, whether they are a good target for another reason.
- Identification attacks, unlike social engineering attacks, do not require the attacker to know or be known by their victim.
- A lot of times in identification attacks, the victim will never know that they were targeted; in fact, many victims don’t even know that there are such things as identification attacks.
- However, when it comes to social engineering attacks, an attacker has to be known by the victim for some sort of benefit in order for the attack to be successful.
Identification attack is still often used with other types of cyber security threats. For example, malware attacks frequently include identification attack components. Many computer viruses will download and install other malicious programs that allow the attacker to gain access to the victim’s files through identification attacks. The more cybersecurity threats that are used together, the greater chance of detection.
As a form of social engineering attack, an identification attack does not always follow a set pattern of action. Typically, the attacker will combine several techniques in an attempt to gather as much information as possible on their intended victims.
Identification Attacks generally involve the gathering of information in a passive manner. In most cases, an attacker will not contact the victim directly, but instead, use publicly available sources of information. Some common sources of information include:
- Website pages: A website page can give a lot of information about its owner. This includes things like where they went to college and what job they have, along with pictures that can be used for facial recognition or voice recognition.
- Social Media Pages: Many social media sites offer users the ability to display certain personal details such as their birthday and place of birth.
- Public Records: This is a fairly common source of information for an attacker. Typically, this type of information is available to download online or can be obtained by requesting the information through an online form.
- Directories and Direct Mail: These are primarily used in identification attacks that take place in public places like malls, parks, social events, and more. These often provide detailed information on everything from where someone went to school to what they do for fun. They also frequently offer other valuable pieces of information like credit card numbers, e-mail addresses, and phone numbers.
Conclusion:
Identification attacks are one of the most common forms of social engineering. They are used by many attackers to gain information on potential targets before they move in with another trick. In this case, the attacker uses an identification attack to gain as much information as possible on a person before they decide to manipulate them into giving up even more private data. In many ways, this type of attack is almost safer for the attacker because it does not involve direct contact with the victim, making it a lot harder for them to be detected. Although identification attacks can have similar consequences as other types of social engineering attacks, it is not always easy for companies and individuals to detect them due to their non-conventional nature.




