Attack Mitigation is a process of monitoring the vulnerabilities in your system to stop the threat from penetrating the network. It is a good practice, but it should not be mistaken for security measures. It’s important to prevent attacks right at their onset by using an appropriate measure, which is also referred to as defense in ethical hacking. This will reduce the number of successful attacks over time without sacrificing network security should something go wrong with your defenses while you’re performing mitigation processes. It is not just about preventing potential attacks, but also preventing incidents. This can be achieved by identifying the vulnerabilities that can have negative effects on your business and working to mitigate the risks.
Vulnerability: A vulnerability refers to a weakness or inadvertent error in your system that allows outsiders such as hackers to gain access to your system without you being aware. A hacking attempt is called an attack if it breaks down security measures and causes damage or threat to an organization’s data and intellectual property.
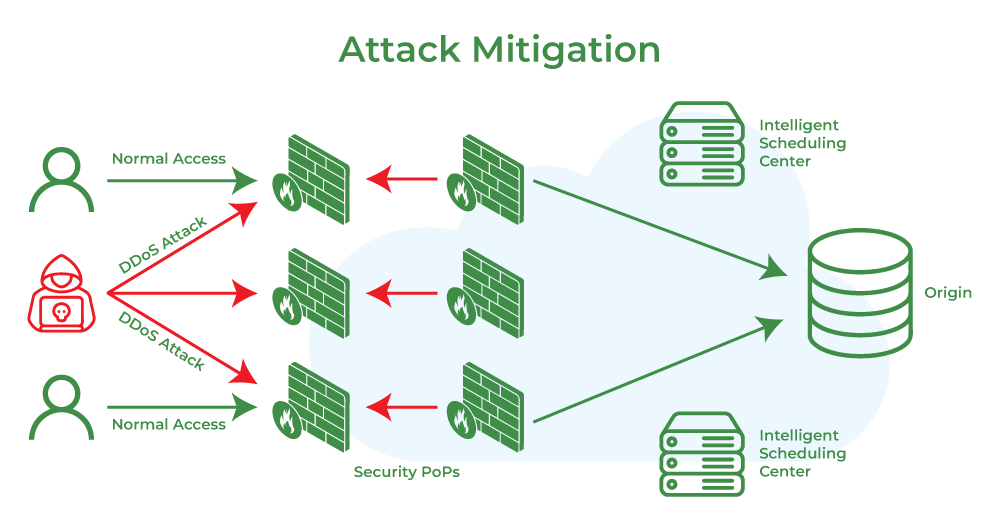
Mitigation: Mitigation refers to the process of removing or blocking access from a source with malicious intent, usually by using appropriate control systems. Using mitigation of existing vulnerabilities prevents future instances of attacks from occurring in normal conditions. Attack Mitigation in Ethical Hacking is an ongoing process to ensure the protection of our system from acts of malicious intent.
Steps of Mitigation of a cyberattack:
- Authentication: Authentication is the process of determining whether someone is who they claim to be. As you can see from the following diagram, authentication removes access from an attacker only after the attack has been detected by an IDS/IPS, and only when it’s known that access was gained inappropriately. Attackers typically follow this path. They scan your network in order to find IPs with vulnerabilities.
- Next, they’ll attempt to gain unauthorized access by exploiting those vulnerabilities
- Then they’ll use techniques like Credential Harvesters or Phishing to gain access to sensitive information
- Finally, they’ll use that sensitive information to compromise your systems (or your clients’ systems) The following diagram shows how IDs/IPS can detect these activities, but it doesn’t include any mitigation steps.
Key Points:
- Authentication removes access from an attacker only after the attack has been detected by an IDS/IPS and only when it’s known that access was gained inappropriately. This means that an attacker gets access to your network without your permission, but doesn’t get access to your sensitive data.
- Authorization is the process of granting or denying specific privileges to a certain user or device on your system.
- It prevents attackers from getting the data they want when they want it unless they follow specific behavior such as those outlined in ACLs (Access Control Lists) and RBAC (Role-Based Access Control).
Countermeasures:
- Attack Mitigation in Ethical Hacking involves the process of monitoring vulnerabilities in your system to prevent them from being exploited. It is a best practice but it should not be confused with security measures.
- Attack mitigation involves using various security control mechanisms to detect, prevent and mitigate attacks.
- Detection: Detection refers to identifying a malicious act or threat by monitoring activity that could potentially harm the overall security of your system. There are various techniques used for detecting an attack such as Intrusion Detection Systems / Intrusion Protection Systems (IDS/IPS), sniffers, honeypots, etc.




