Evan Porter
Updated on: December 20, 2023
Think of the damage that one talented hacker can do. Now imagine what they can do with an army of computers at their disposal, amplifying their resources on an order of thousands or millions.
These “armies” actually exist, and they’re called botnets.
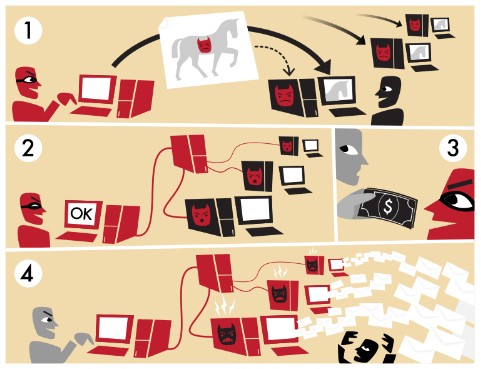
Botnets are groups of computers that have been infected with malware. A hacker or attacker can then remotely control all of the computers in the botnet as a group to do things like send spam messages, conduct DDoS attacks, generate fake web traffic, serve ads to everyone in the botnet, or coerce payment from users to be removed from the botnet.
Here’s our guide to how botnets are created and used, and how you can protect yourself from being recruited into one in 2024.
How Are Botnets Created?
Tom-b / CC-BY 1.0
To carry out large scale attacks or disruption, a botmaster or bot herder will start by creating a piece of malware that allows them to remotely and secretly control a host computer.
From there, they need to get hundreds, thousands, or even millions of people to unwittingly install that malware on their computer.
Typically, hackers do this through the use of a Trojan horse virus, meaning the malware disguises itself as a harmless document or program and tricks users into installing it.
This can take many forms, including:
- A seemingly benign email attachment (like an invoice), either from a known or unknown sender. Downloading it will trigger installation of the malware.
- A pop-up ad warning that your computer has a virus. Clicking on the ad to fix the issue will download and install the malware.
- A software download from an untrustworthy website may actually turn out to be botnet malware.
Personal computers aren’t the only devices that are vulnerable.
In 2024, with so many of our home devices and appliances armed with Internet connectivity (called the Internet of Things), even your smart thermostat, DVR, gaming console, and home security camera could get recruited by a botnet to perform illicit tasks.
Once the malware has been installed on a device, the attacker will be notified and that device will be under his or her remote control.
How Are Botnets Used?
Once a large botnet has been created, the possibilities for malicious use are nearly endless.
Most commonly, botnets are used to conduct Distributed Denial-of-Service attacks (or DDoS).
There are many different kinds of DDoS attack, but generally hackers will use a botnet to send a massive surge of web traffic or requests to a website, app, or server. The overwhelming influx of activity will often cause the target to crash.
DDoS attacks are commonly used to harm rival businesses, take down certain web content (political or terrorism-related), by gamers to get ahead of their competitors, or simply by trolls to cause disruption.
Botnets can also be used to do things like:
- Send email spam
- Generate fake web traffic to drive revenue
- Coerce payment from a user to remove their device from the botnet
- Be rented out or sold to other hackers
Typically, botnets can be very difficult to detect without the use of antivirus software.
The goal of a botnet, unlike other forms of malware, is not usually to steal your information or coerce payment from you (though they can). Often, the botmaster will simply use your computer for small and ordinary-seeming tasks like pinging a certain website or network.
To you and your device, this activity barely registers. But when a million computers execute the same task at once, the results can be catastrophic for the target of the attack.
How to Protect Your Computer from Becoming Part of a Botnet
Pexels
Botnets sound pretty scary, and the truth is they can be put to some seriously nefarious uses.
But keeping your computer or device from being recruited by one is relatively simple.
Here are a few tips that will keep you safe in 2024:
Run regular antivirus scans
This is the absolute best and most effective way to deal with any form of virus or malware, including botnet malware.
A reputable antivirus will prevent most botnet malware from ever being installed on your computer, and will usually be able to easily remove it if you’ve already been infected. Brands such as Norton, Malwarebytes, Bitdefender and TotalAV are some of the most highly-recommended brands.
Never download attachments from email senders you don’t know
Luckily, most modern email providers like Gmail and Outlook are pretty good about filtering out messages that look like spam or viruses.
However, one malicious message could still easily slip through the cracks.
Be very careful about opening messages from senders you don’t recognize. If you do, absolutely never download any attachments until you can find out exactly what it is and who it’s from.
You should also be wary of unexpected attachments even from known senders, as their computers could be infected by the botnet and they could be unknowingly propagating the malware.
Botnet Trojans can be super sneaky! They’re often disguised as important looking documents like invoices, bill, and receipts. If you’re not expecting it and it’s not immediately clear what it is, don’t download it.
Run regular software and operating system updates to patch vulnerabilities
The world of malware moves incredibly fast. New viruses are created every single day, which is a challenge for antivirus and software creators to keep up with.
Most trusted antivirus providers and operating systems will offer frequent updates and patches in order to protect against the latest known vulnerabilities.
It’s easy to put off or ignore regular software updates, but they could be key to keeping you protected from malware.
Avoid untrustworthy websites & ads
A common way bot masters trick users into downloading their malware is through placing intriguing ads or downloads in their path during web browsing.
Avoid downloading free software from unfamiliar websites and don’t click on pop-up ads that promise to fix your computer. Interacting with these pages can often initiate malware installation on your device.
Installing trusted anti-spyware software will also add an extra-layer of protection.
Antivirus Is the Best Solution
Outside of practicing safe browsing and download behaviors, the best thing you can do is install a good antivirus, keep it up to date, and run regular health checks of your machine.
Any reputable antivirus should be able to easily remove botnet malware from your computer and prevent any future infections.