This article is about Wireless Encryption Protocol or commonly known as WEP. This protocol is one of the two most popular protocols used by wireless networks to send data across the network. It provides a good level of security, and some parameters can be set to provide an even stronger level of security.
WEP:
- The Wired Equivalent Privacy (WEP) was designed by the IEEE Security Task Group in late 1997 to provide wireless communications with the same level of security as wired networks. It basically provides 64 bits of data at a time to encrypt and/or decrypt your data. The algorithm used to encrypt and decrypt data is RC4, which is a stream cipher that uses an initialization vector (IV).
- As with all encryption schemes, WEP has two modes of operation – text mode and hexadecimal mode. In-text mode, the encryption key is a plain text string, while in hexadecimal mode, it is represented as six 8-bit integers. An IV has to be at least 24 bits, and it has to be unique if you want the same encryption key to encrypt more than one data frame. Even if the data frame is more than 64 bits, both have to have the same IV.
- WEP uses RC4 stream cipher, which takes plain text and an initialization vector (IV), and encrypts them using a pseudo-random sequence of bits. The RC4 stream cipher was developed by Ron Rivest in 1987 and has been widely used since then. In the RC4 cipher, a linear feedback register is used with an internal state that generates all the pseudo-random numbers for encryption purposes. This register is capable of generating any number from 0 to 4 billion in 1-byte increments.
- The initialization vector (IV) is used to generate the key stream for encryption. RC4 requires an 8-byte IV for 40- or 104-bit WEP keys, 16 bytes for 128-bit keys, and 24 bytes for 152-bit keys. The IV is transmitted along with the data as part of the message so that the receiver can properly decrypt it.
- For each packet sent using WEP encryption, four things are required:
The initialization vector (IV) is optional. If it is not specified, the first 16 bytes of a packet will be used as the IV.
WEP Crack:
- There are many ways to break the WEP security, but only three are possible with the use of a wireless card. The first one is Man in the Middle attack, ARP Cache Poisoning attack, and Simple WEP Crack.
- A few years ago, there was only one technique called ARP Cache Poisoning attack, using which anyone can easily decrypt the data if he has physical access to the network or access to some router or a computer on that network.
- But this method was not so easy to be used in practice because it required physical or login access to a computer.
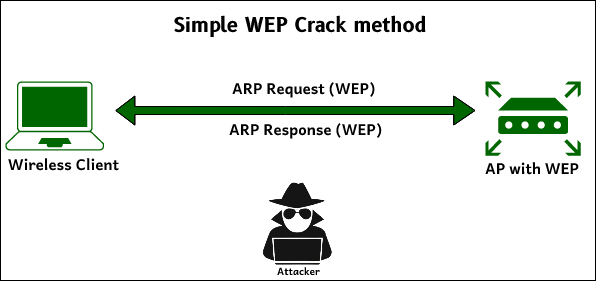
The simple WEP Crack method is a wireless encryption cracker that uses the hardware tools to decode the data stream or tunnel them through your computer. The idea behind this technique is that you are able to find out plain text information because of missing parts of IV. This method first uses the IV to know the plain text, and then it guesses the WEP key provided by the manufacturer.
Usage of Simple WEP Crack:
- The usage is simply because it does not even require an installation. Find out the MAC address of the access point, as given on the back side of your card, and type them in the text box present on the main page. Then select encryption type, which I would recommend you to be 64 bits. After that, click on the “Crack” button and after a few seconds, you will get the key with a percentage of key strength.
- Nowadays, most wireless cards are supported WEP encryption, such as (Aironet 350 series). If you want to check whether your card is capable of doing this or not, just open a command prompt and type winipcfg in the Run box and then press enter.
Countermeasures of Simple WEP Crack method:
- Every wireless connection is vulnerable to being cracked.
- All a hacker needs to do is have the proper software tools, tools that can easily be found online, and then steal an entire network’s password or Wi-Fi credentials. The only way not to have your wireless connections captured by a hacker is not to use wireless networks at all.
- Always make sure they are always plugged in with wired connections before clicking “connect”. An added bonus-users may experience less time waiting for their computers due to less processing power needed for communication and conversions. Also, wireless connections are more vulnerable to eavesdropping and are less secure than wired connections.
The methods of defending against the WEP cracking method can be done through simple passwords or through more complex means. First, a person could install their own router and change the default password. The password should be strong and consist of at least 12 characters, lowercase and uppercase letters (randomly mixed), numbers, and special characters like @ # $ % ^. Another method is to enable WPA2 encryption along with a long password. This method ensures that any hacker will have to spend a lot of time trying all possible combinations in order for them to gain access to your network.
They use a software program to guess passwords using words from the dictionary. It runs through all the password possibilities until it finds one that works.
A third method of preventing WEP cracking would be to place your wireless router out in the open. This will make it easier for you to detect if someone is trying to hack into your network. If you can see that there are no suspicious-looking laptops sitting out around your wireless router, then there’s probably nothing wrong with your Wi-Fi connection. Everyone should be able to learn more about the dangers of internet security today and take precautions, so it doesn’t happen again.




