SQL Injection is an attack that employs malicious SQL code to manipulate backend databases in order to obtain information that was not intended to be shown, The data may include sensitive corporate data, user lists, or confidential consumer details. This article contains types of SQL Injection with their examples. SQL Injections-LABS (a platform to learn SQL Injections) to showcase how you can perform each type of SQL Injections.
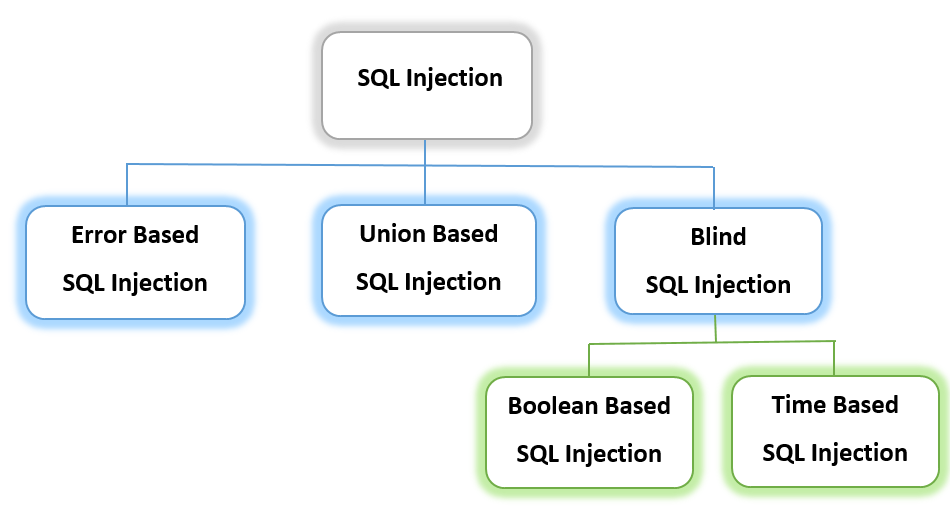
1. Error-Based SQL Injections:
Error-based SQL Injections obtain information about the database structure from error messages issued by the database server. In rare circumstances, an attacker may enumerate an entire database using only error-based SQL injection.
Example:
In SQL Injections labs, if you type ?id=1 in the URL and press enter, it gives you the login name and password.

But if we type ?id=1’ it gives an error.

This error will now assist us in locating the backend query.
If we remove the first and last quote from “1” LIMIT 0,1′, then it becomes ‘1” LIMIT 0,1.
1′ is our input, and a single quote after this input indicates that our input is enclosed in single quotes. This means that the query that was executed back in the database was the following:
Query:
select * from table_name where id='1
which is syntactically incorrect. Now, we will fix this query by giving input ?id=1′ –+.
–+ will comment out all that comes after it. So, our backend query would be:
Query:
select * from table_name where id='1' --+'
and again we get the login name and password.

Now we can insert a query between the quotation and -+ to retrieve data from the database.
2. Union-Based SQL Injections:
Union-based SQL Injections use the UNION SQL operator to aggregate the results of two or more SELECT queries into a single result, which is subsequently returned as part of the HTTP response.
Query:
SELECT EMP_ID, EMP_DOJ FROM EMP UNION SELECT dept_ID, dept_Name FROM dept;
This SQL query will produce a single result set with two columns, including values from EMP columns EMP_ID and EMP_DOJ and dept columns dept_ID and dept_Name.
Two important needs must be met for a UNION query to function:
- Each query must return the same number of columns.
- The data types must be the same, i.e., it is not changed after query execution.
To determine the no of columns required in an SQL injection UNION attack, we will Inject a sequence of ORDER BY clauses and increment the provided column index until an error is encountered.
?id=1' order by 1 --+ no error ?id=1' order by 2 --+ no error ?id=1' order by 3 --+ no error ?id=1' order by 4 --+ we get error

This demonstrates that the query lacks the fourth column. So we now know that the query in the backend has three columns.
Now we will use the UNION statement in order to join two queries and to be able to discover the vulnerable columns.
Query:
id=1‘ UNION SELECT 1,2,3 --+

There is no issue, but we are obtaining the result set of the first query; to receive the result of a second select query on the screen, we must make the first query’s result set EMPTY. This may be accomplished by supplying an ID that does not exist (negative ID).
Query:
?id=-1‘ UNION SELECT 1,2,3 --+

This demonstrates that we are getting values from columns 2 and 3 as output. As a result, we can utilize these two columns to retrieve information about and from the database.
Query:
?id=-1‘ UNION SELECT 1,version(),database() --+
This will provide the database we are currently using as well as the current version of the database utilized at the backend.

3. Blind Boolean-based SQL Injections:
Boolean-based SQL Injection works by submitting a SQL query to the database and forcing the application to produce a different response depending on whether the query returns TRUE or FALSE.
Example:
In SQL Injections LABS if we type ?id=1 in the browser URL, the query that will send to the database is:
Query:
SELECT * from table_name WHERE id=1
It will output “you are in” in yellow font on the web page, as seen in the image.

When an attacker tries to use a comma (‘) ?id=1’ to break this query, he will not be able to find an error notice using any other method also. Furthermore, if the attacker attempts to inject an incorrect query, as illustrated in the figure, the yellow text will vanish.

The attacker will next use blind SQL injection to ensure that the inject query returns a true or false result.
?id=1' AND 1=1 --+
Now, the database checks if 1 is equal to 1 for the supplied condition. If the query is legitimate, it returns TRUE; as seen in the screenshot, we have the yellow color text “you are in,” indicating that our query is valid.

As a result, it confirms that the web application is vulnerable to blind SQL injection. We will get database information using true and false conditions.
Now, we will inject the following query, which will question whether the length of the database string is equal to 1, and it will respond by returning TRUE or FALSE via the text “you are in.”
?id=1' AND (length(database())) = 1 --+
As you can see in the image, the text disappears again, indicating that it has returned FALSE to respond NO the length of the database string is not equal to 1.

When we test for a string length of 8, it returns yes, and the yellow text “you are in” shows again.

4. Blind Time-Based SQL Injections:
Time-based SQL Injection works by sending a SQL query to the database and forcing it to wait for a predetermined length of time (in seconds) before answering. The response time will tell the attacker if the query result is TRUE or FALSE.
Depending on the outcome, an HTTP response will either be delayed or returned immediately. Even though no data from the database is returned, an attacker can determine if the payload used returned true or false. Because an attacker must enumerate a database character by character, this attack is often slow (particularly on big databases).
And SLEEP(10) if sleep then Vulnerable OR SLEEP(10) if sleep then vulnerable




