Session prediction attacks focus on predicting session ID values that allow an attacker to bypass the application’s authentication scheme. By analyzing and understanding the session ID generation process, an attacker could predict a valid session ID value and gain access to the application. The attacker needs to collect some valid session ID values that are used to identify the authenticated user. Next, you need to understand the structure of the session ID, the information used to create the session ID, and the encryption or hash algorithm used by the application to protect the session ID. Some improper implementations use a username or session ID consisting of other predictable information such as timestamps and client IP addresses. In the worst case, this information is used in plain text or encoded with a weak algorithm, such as Base64 encoding.
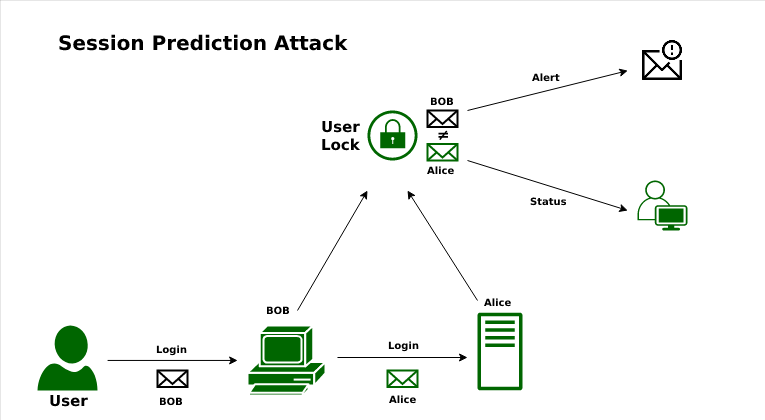
Session prediction is impossible without the help of the session ID cookie. Session cookies are used by websites to maintain a session with you. Session prediction is used by hackers to predict the next session and is used for malicious purposes. There are three ways in which a hacker can perform an attack:
- Social Engineering: There are several ways hackers can play social engineering and use deception to trick you. They will tell you that your PC is infected with a virus and will ask you to install their software so that they can repair your computer. It also sends fake emails and messages on Facebook, makes phone calls to let you know that your system has been attacked by a virus, and sends attachments such as malware.
- Spoofing: Spoofing is a technique that allows a hacker to use another visitor’s IP address to access a website and launch an attack. The only way to protect yourself from such attacks is to verify your IP address before visiting a website.
- Session Prediction: This session prediction attack is used by hackers to use session ID cookies to access servers and perform malicious activities.
Working of Session Prediction Software Attack:
- Session prediction and hijacking usually occur when legitimate users are interacting with the affected website.
- Depending on the level of technical knowledge and the nature of the attack, legitimate users may or may not be able to detect the intrusion.
- Session predictions or hijacking can occur if a website does not respond to user input normally or as expected, or if it stops responding at all for unknown reasons.
Countermeasures:
- Use HTTPS: Make sure you need to use HTTPS everywhere on your web servers and applications, especially SSO systems. In addition, all internet communications must be encrypted to protect the session at all stages.
- Install the framework: Web frameworks can generate longer and more random session cookies, which simplifies session management.
- Rotate session key after authentication: Changing the session key after a successful login makes it difficult for the session hijacker to track the user’s session, even if they know the original key. With such a setting, the attacker would not be able to hijack the session using the self-generated key, even if the attacker sent a phishing link that the user clicked.




