In essence, password auditing programs make guesses about the credentials being used on your network. They accomplish this using a combination of brute force and dictionary assaults, among other techniques, and then inform you of any other ways the passwords may be compromised, such as by being pwned.
L0phtCrack:
An application called L0phtCrack is used to audit and recover passwords used on networks to make sure they are hard to crack, frequently changed, and never recycled. As the first commercially accessible password auditing solution in the world, it was developed by hackers in 1997. Since then, multiple L0phtCrack versions have been released, with the most current one debuting in 2016. L0phtCrack was purchased by Terahash in 2020 for an undisclosed sum of money. L0phtCrack 7.2.0 is now available as an open-source project. You can download the software from the official website as shown below:
Features of L0phtCrack:
- All versions of Microsoft Windows and its higher versions can run this software. It can also be used to run over networks with the help of Windows XP, 2000, NT, Server 2008 R1/R2, and Server 2006 R1/R2. The operating system is compatible with both 32-bit and 64-bit settings. For BSD and Linux variations, there is a different version of this software that includes a different SSH Daemon.
- The sixth iteration of L0phtcrack (L0phtcrack 7) additionally gives you a scoring metric that you can use to quickly assess the strength of the password. Passwords can be compared to any of the industry’s current best practices and further categorized as Fail, weak, medium, or firm.
- L0phtcrack 7, the seventh iteration of the application, can import and import any UNIX password files. Because of this, it can do network audits using just one interface.
- Additionally, there exist some Pre-Computed password files, which are essential components of all password cracking and auditing tools. Both those files and the pre-generated password hashes are supported by L0phtcrack 7. Now, instead of taking days or hours to accomplish, these kinds of password cracking and auditing simply need a few minutes.
- You must carry out various scans at various times with the assistance of the most recent version of L0phtcrack. The scheduled scans feature of this program is another alternative. It performs a scan on the many expected times that you select according to your convenience.
- The most recent version of L0phtcrack seeks to provide remediation aid to required system administrators, as well as guidance on how to take serious action against bad passwords that can be used on multiple accounts. Passwords for these types of reports can be disabled and expire from within the L0phtcrack interface.
- This software’s Graphical User Interface (GUI) is exceptionally user-friendly and can be quickly comprehended by any new user. This new version of the L0phtcrack has various settings that are presented on the main window of the software and can be readily accessible and utilized by the user; using this software does not require any particular education.
- The L0phtcrack update has been coded to produce many reporting types, each of which is displayed in a separate tabbed form interface. The auditing findings of this software can also display the severity of the risk and the auditing techniques used for the password character.
- The most recent update to L0phtcrack additionally provides you with a risk rating for the password. There are four different classifications for these password danger statuses: low risk, medium risk, high risk, and empty.
Steps of L0phtCrack Audits and Cracks Passwords:
L0phtCrack is software that aims to break any Windows passwords using hashes so that it can acquire access to (take full control of) network servers, standalone Windows computers, Active Dictionary, or primary domain controllers. Even if the hashes are off the wire in some other situations, it can still find them.
- To start off, L0phtcrack needs password hashes.
- Network administrators can easily retrieve password hashes using L0phtCrack’s capability to remotely access other computers on the network.
- L0phtCrack audits can be executed manually or on a schedule at predefined intervals. Groups of password hashes are subjected to many attacks once L0phtcrack obtains them.
- The application uses a dictionary attack, a hybrid attack, a pre-computed assault using rainbow tables, and a brute-force attack after verifying that the password and username are distinct.
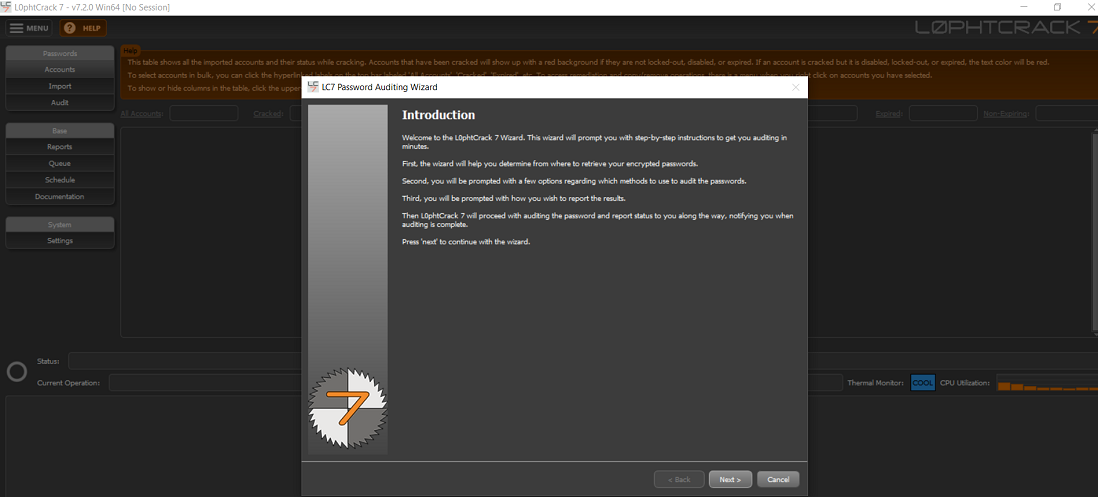
Interface of L0phtCrack Password Auditing Wizard:
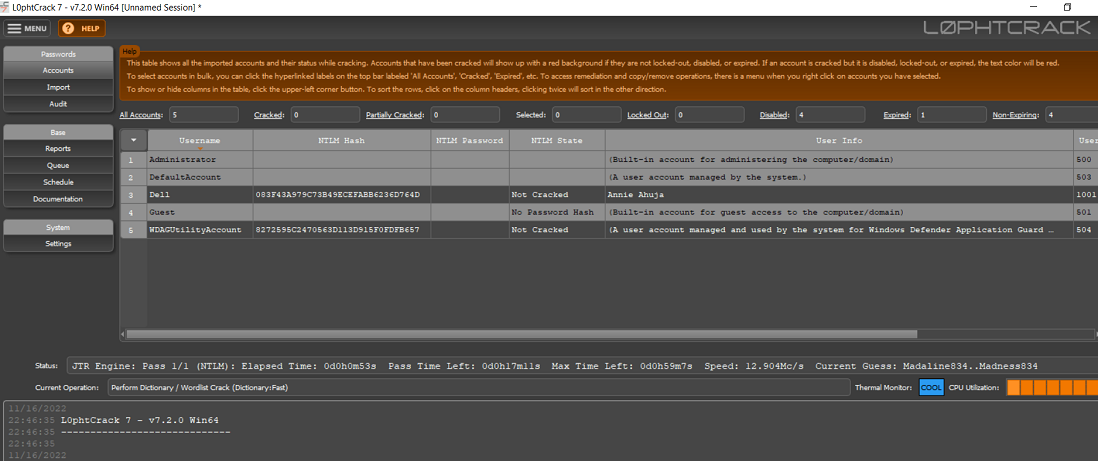
Result:
Usage:
There’s a good chance that your clients, staff, or both use passwords to secure sensitive data. The usage of passwords is still prevalent across almost all operating systems and applications, including desktop, mobile, and online, despite decades of expert predictions to the contrary. Passwords that are easy to guess, stuff, or brute force are currently the biggest security risk. You need L0phtCrack to carry out regular audits if your staff or clients utilize passwords. In addition to auditing passwords, L0phtCrack can assist by fixing password issues. Following an audit, L0phtcrack generates a report with details on the security level and age of the various passwords used on the network. The network administrator can then either disable these accounts or demand a password change for the subsequent login.
Conclusion:
L0phtCrack 7 provides enhancements to its user-friendly password auditing wizard, scheduling, and reporting in addition to auditing passwords significantly more quickly. All Windows versions, including Windows 10 “Anniversary Edition,” are compatible with an improved password hash importer that operates without a hitch locally and remotely. Numerous novel UNIX password hash types are also supported. Future password hash crackers and importers for new sorts of passwords can be created by third parties thanks to a new plugin interface. The methods used by cyber criminals to acquire private client information are constantly being improved.




