The Metasploit Project is a computer security project that provides data about security vulnerabilities and assists in penetration testing. It is owned by Rapid7, a US-based cybersecurity firm. A notable subproject of Metasploit is the open-source Metasploit Framework—a tool used to develop and run exploit code on remote target systems.
What is Metasploit?
The Metasploit project includes anti-forensics and remediation tools, some of which are built into the Metasploit Framework. Metasploit comes pre-installed on the Kali Linux operating system. As we all know Metasploit is a huge framework and can be used to do a lot of tasks. This article will show us how to use Metasploit’s auxiliary modules. These modules are beneficial in many scenarios such as scanning, information gathering, and much more, in this tutorial, we will show you how to a few of them but you can follow the same steps to use most auxiliary modules.
What are Auxiliary Modules in Metasploit?
In Metasploit, any module that is not an exploit is an auxiliary module. Exploit modules always have a payload. Auxiliary modules are a fascinating feature of the framework allowing it to extend for a variety of purposes other than exploitation. You can create your own quick vulnerability scanners, and port scanners, make MSF work as an FTP, HTTP, or SMTP client, and do a whole lot of other cool stuff. You have a ready-to-use code library at your disposal enabling quick development of such tools.
Auxiliary modules are a fascinating feature of the framework allowing it to extend for a variety of purposes other than exploitation:
- admin: Modules that modify, operate, or manipulate something on the target machine.
- analyze: We initially created this folder for password-cracking modules that require analysis time.
- client: We initially created this folder for an SMTP module for social-engineering purposes.
- dos: Pretty self-explanatory: denial-of-service modules.
- fuzzers: If your module is a fuzzer, this is where it belongs. Make sure to place it in the correct sub-directory based on the protocol.
- gather: Modules that gather, collect or enumerate data from a single target.
- scanner: Modules that use the Msf::Auxiliary::Scanner mixin almost always go here. Make sure to place yours in the correct sub-directory based on the protocol.
- server: Modules that are servers.
- sniffer: Modules that are sniffers.
Usage of Auxiliary Modules
Step 1: First, start the Metasploit framework by just running the command msfconsole on the terminal.
msfconsole
Step 2: Now to see all the auxiliary modules available in Metasploit just type the command:
show auxiliary
With almost 1,000 auxiliary modules, Metasploit is probably one of the most complete penetration frameworks out there.
Examples of Auxiliary Module
TCP port auxiliary module
Step 1: We will start with one of the most useful HTTP auxiliary modules, TCP port scan, so we are going to use the “use” command followed by the auxiliary that we want to use:
use auxiliary/scanner/portscan/tcp
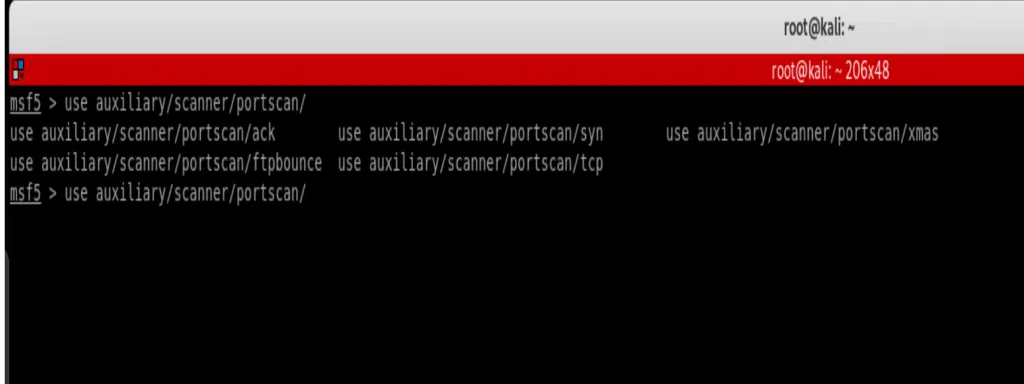
Just like using anything in the Metasploit framework, if you’re stuck at any point just hit the double tab to see all the available modules as shown below.
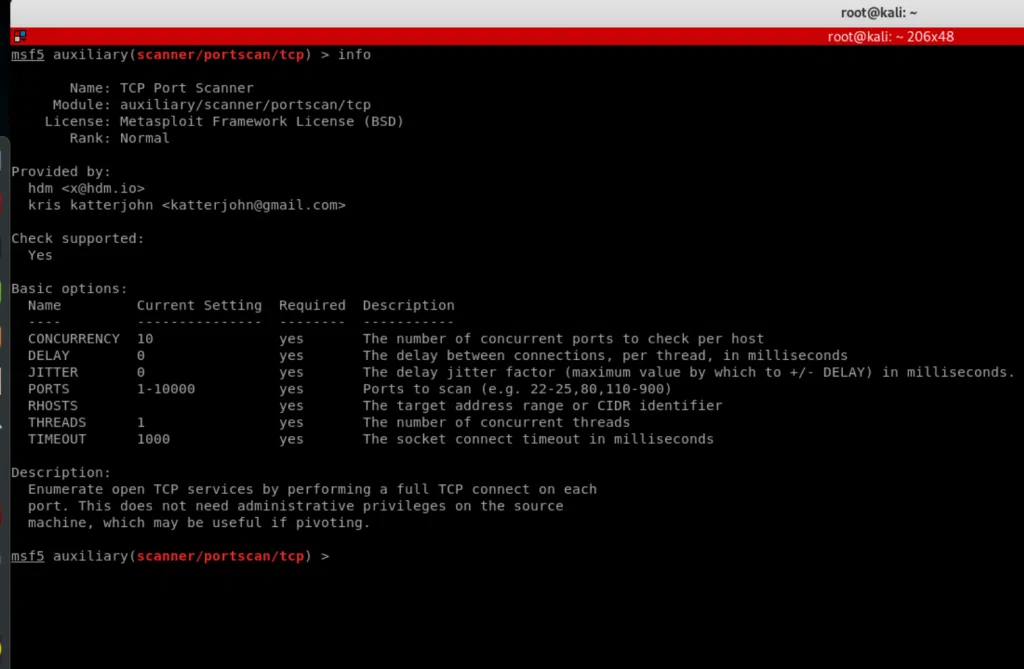
Step 2: We can also use the “info” command to get more information on a specific module (or auxiliary in this case) and see all the options that we can set:
Step 3: Now we need to change the options so the module runs on our target, we are going to run this module against another virtual machine in our network, this virtual machine is running metasploitable so it should have a number of open ports, so the main option that we need to set is the RHOST which is the IP of the machine that we want to run this module against, changing the options here is the same as changing it in any other Metasploit module, it follows the following format
set [option name] [option value]
So in our case [option name] is RHOST and [option value] is 10.0.2.9 which is the IP of the target machine, therefore the command is:
set RHOST 10.0.2.9
We’ll also change the number of threads by running
set THREAD 50
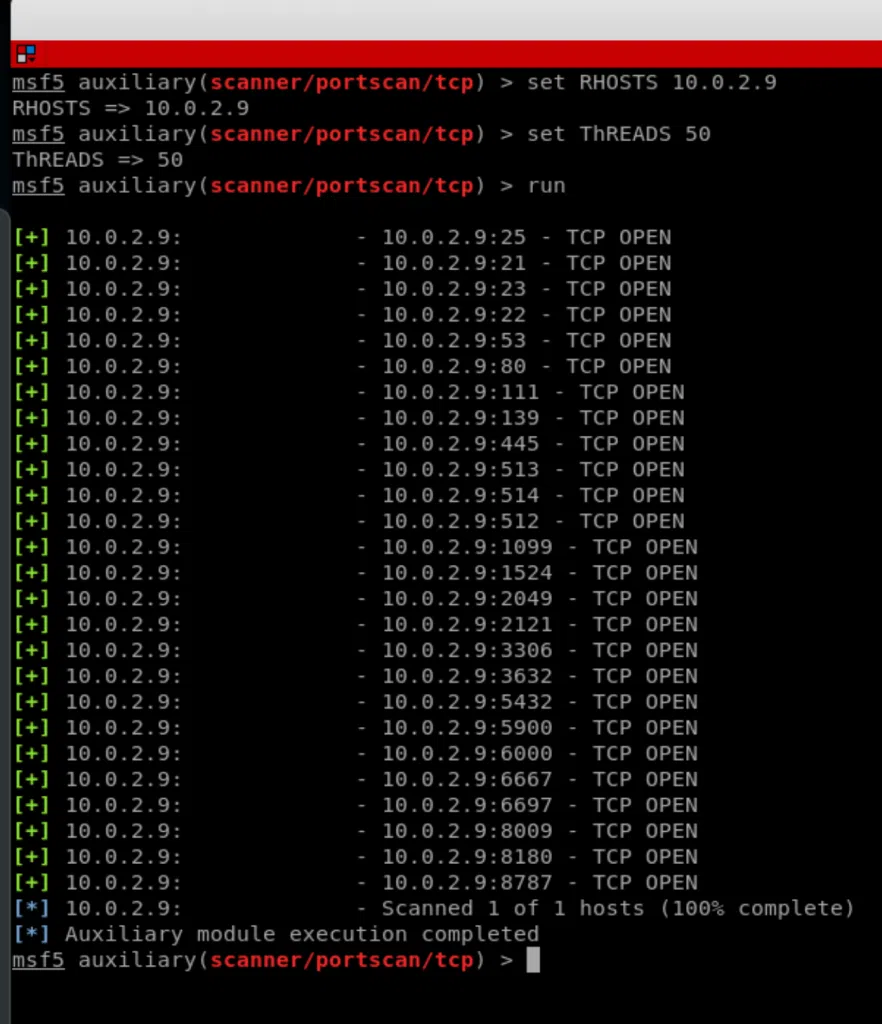
Finally, we can run “info” again just to make sure that all the options are set as we wish and then use the “run” command to run the module, give it some time and you’ll get the results in the same window.
Scanning MSSQL with Metasploit Auxiliary Module
Step 1: Let’s jump into the Metasploit-specific modules for testing the MSSQL server and see what kind of information we can find by using them. The very first auxiliary module we will use is mssql_ping. This module gathers additional service information.
use auxiliary/scanner/mssql/mssql_ping
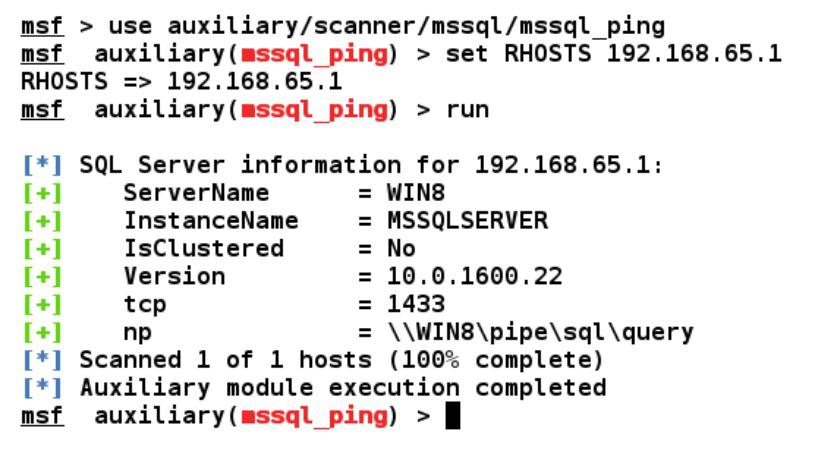
Step 2: The next step in penetration testing a database is to check authentication precisely. Metasploit has a built-in module named mssql_login, which we can use as an authentication tester to brute force the username and password of an MSSQL server database.
Let’s load the module using the command and analyze the results:
use auxiliary/scanner/mssql/mssql_login
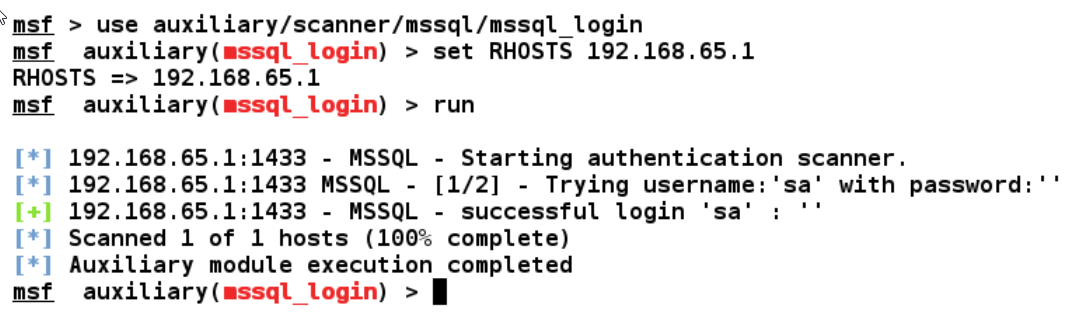
So this is just a simple example of using it soon as we run this module, it tests for the default credentials at the very first step, that is, with the sa username and the blank password, and finds that the login was successful. Therefore, we can conclude that the default credentials are still being used. Additionally, we can try testing for more credentials if the sa account is not immediately found.
Step 3: To achieve this, we can set the USER_FILE and PASS_FILE parameters with the name of the files that contain dictionaries to brute force the username and password of the database management system:g an auxiliary in Metasploit, here we used a port scanner but you can use most modules the same way, so the main steps are:
show options
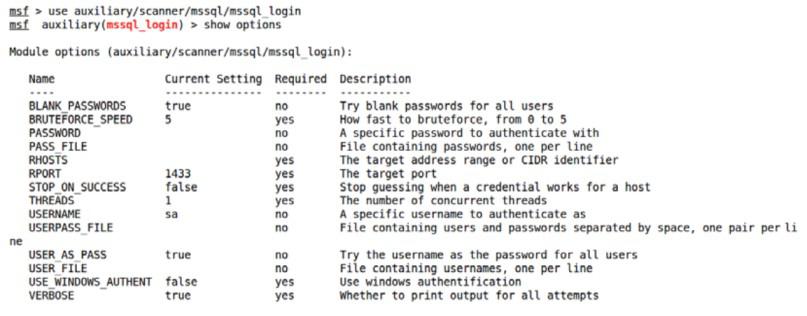
Step 4: Let’s set the required parameters, which are the USER_FILE list, the PASS_FILE list, and RHOSTS, by issuing the set USER_FILE user.txt, and set PASS_FILE pass.txt, and set RHOSTS 192.168.65.1 commands, respectively, to run this module successfully, as follows:
set USER_FILE user.txt set PASS_FILE pass.txt set RHOSTS 192.168.65.1
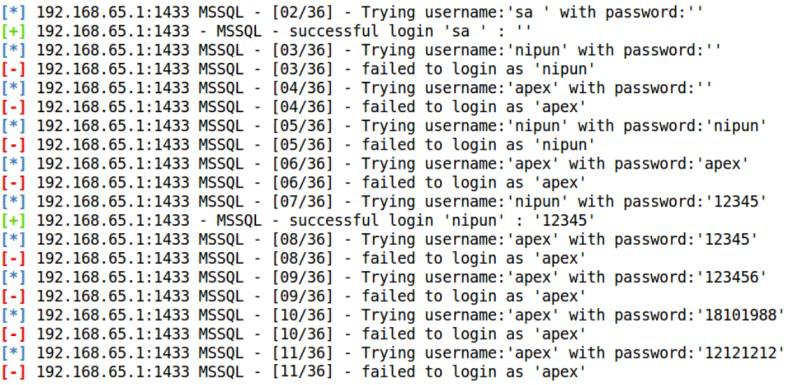
Step 5: When we will run this module against the target database server, we will get an output similar to the one in the following screenshot:
As we can see in the preceding output, we have two entries that correspond to the successful login of the user in the database. We found a default user, sa, with a blank password, and another user, nipun, whose password is 12345.
Conclusion:
These are modules that provide additional functionalities such as scanning, fuzzing, sniffing, and much more. Metasploit offers various exploits, post exploits, and auxiliary, scanner, evasion, and exploit development tools.