In this information era, each and every organization whether small or big wants to expand using digital platforms, but the main concern is the security and safety of customers’ data. Transactions can only be secured if the network is properly configured with authentication and authorization features. To understand the network at the micro level, engineers designed Wireshark which is a tool for checking all the security requirements to make a safe and secure network. It comes with many advanced tools which can sniff networks, capture data packets, analyze them, and also for troubleshooting.
IKEv2 or Internet Key Exchange version 2 can be understood as a tunneling protocol that is used for safe and secure communication among different network devices. It uses encryption keys to set up a secure session between devices for communicating confidential data. Keys used in this protocol are generally Diffie Hellmann keys with AES-256-GCM encryption.
IKEv2 Decryption Table in Wireshark:
It is an analysis window in Wireshark which is used to decrypt IKEv2 encrypted payload packets captured while establishing a secured session using the IKEv2 protocol. This table separates ISAKMP and ESP protocol packets from the other captured packets because these protocols are mainly used in generating encryption keys with the help of the IKEv2 protocol. The IKEv2 decryption table can be found by clicking the Edit tab and choosing Preferences.
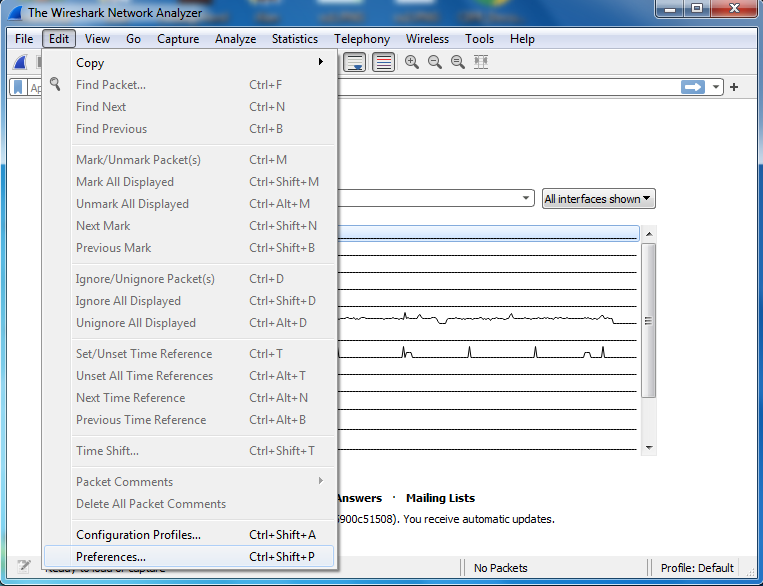
A new window will open click on protocols to open a drop-down protocol list
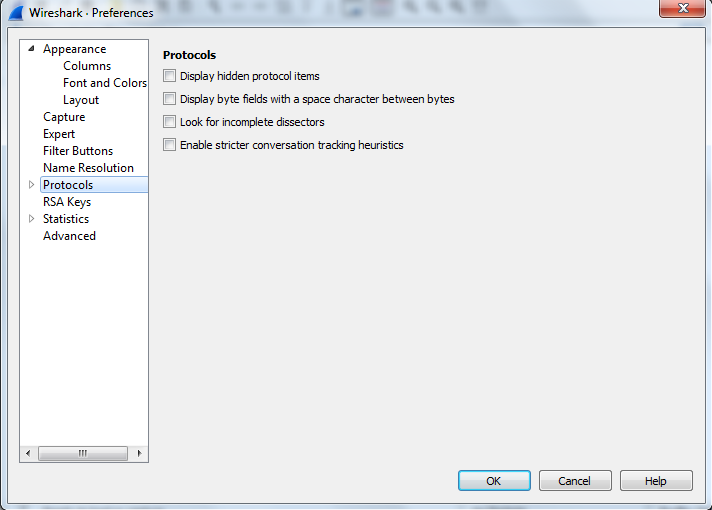
Choose ISAKMP and click on it.
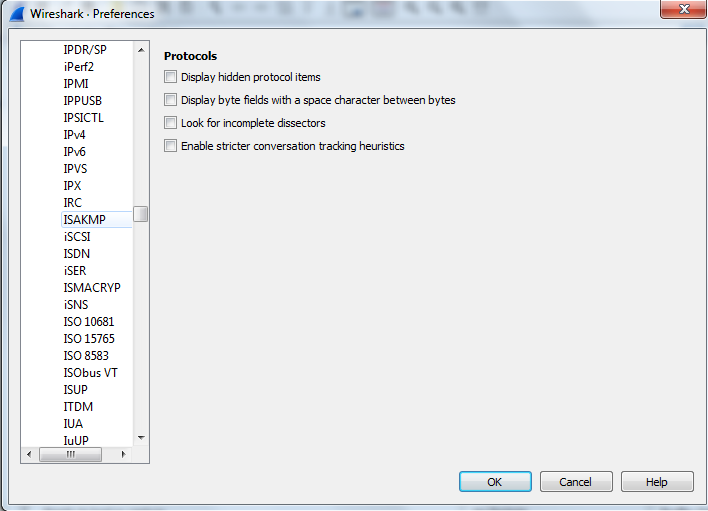
A new window will open with the IKEv2 Decryption table.
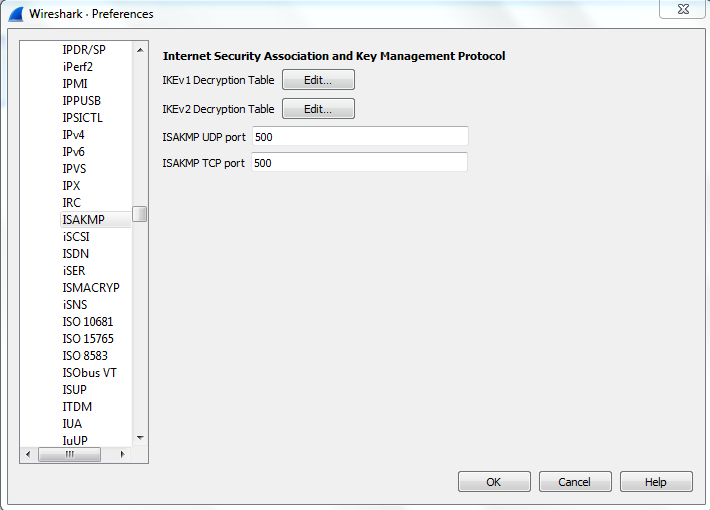
Click on the edit button and a new window with different fields will open.
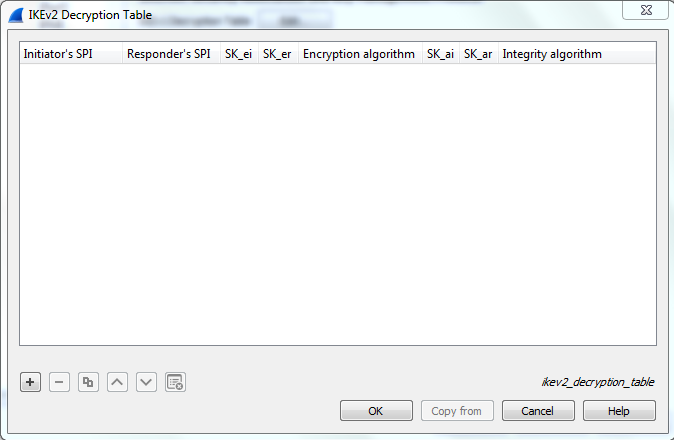
A lot of information fields can be seen here which are:
- Initiator’s SPI: It indicates the security parameter index of the initiating device, it is a combination of 16 hex characters.
- Responder’s SPI: It indicates the security parameter index of the responding device, it is also a combination of 16 hex characters.
- SK_ei: It indicates the security key used to encode or decode a message sent from the initiator to the responder, generally it is a combination of 32 hex characters.
- SK_er: It indicates the security key used to encode or decode a message sent from the responder to the initiator, it is also a combination of 32 hex characters
- Encryption Algorithm: It shows the algorithm used for encryption.
- SK_ai: It indicates the security key which calculates the checksum for data packets sent from the initiator to responder, it is a combination of 40 hex characters.
- SK_ar: It indicates the security key which calculates the checksum for data packets sent from the initiator to the responder, it is also a combination of 40 hex characters.
- Integrity Algorithm: It shows the algorithm used for generating integrity checksum.
All the data can be copied and saved in different formats for later use.




