The domain name system, or DNS, is a naming system for computers, services, and other internet resources that is hierarchical in nature. It’s essentially the internet’s phone book. Each domain name has a corresponding set of ten or so numbers that make up the domain name’s IP address. Simple, user-friendly domain names were developed so that users would not have to remember complicated IP addresses for each website they visited. It is the DNS’s responsibility to match domain names with internet IP addresses so that users can access websites.
DNS Poisoning and Spoofing Attack:
DNS spoofing or poisoning is a type of computer security hacking in which fraudulent Domain Name System data is launched into the DNS resolver’s cache, causing the name server to return an inaccurate result record, such as an IP address. All a DNS spoofing attack requires is a target. This can be an ‘Authoritative Name Server’ (which can be easily obtained by performing a domain WHOIS on any domain on the Internet) as well as a vulnerability in the system hosting the DNS cache. Someone can easily adjust the cache of that DNS server and start directing traffic from ‘yahoo.com’ (or any other desired host) to anywhere else on the internet (or even more devious, the local LAN). The main issue with this is that using DNS’s ubiquity to provide ‘spoofed’ or ‘hijacked’ answers can lead to a slew of issues such as phishing attacks, SPAM, password leaks, social engineering attacks, political disorder, and so on.
Working:
In a web browser, a user types example.com. Following that, the client device requests IP address information and attempts to locate the answer locally on the device. When a browser or application connects to the internet, it first asks a local DNS server for the address of a name (such as bluecatnetworks.com). The local DNS server will query the root servers that own that domain, and then query the authoritative name server for that domain.
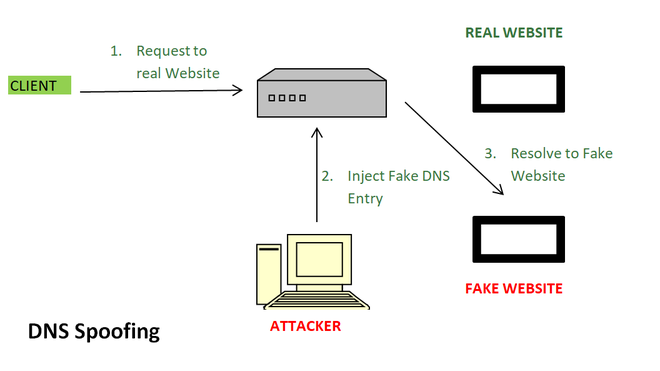
- DNS poisoning occurs when a malicious actor intervenes in the process and provides an incorrect answer.
- DNS spoofing attacks are another name for man-in-the-middle attacks. In essence, the malicious actor deceives the DNS server into believing it has located the authoritative name server when, in fact, it has not.
- Once the malicious actor has tricked the browser or application into believing it has received the correct answer to its query, it can redirect traffic. This allows it to feed any fake website it wants back to the host device. These are typically pages that resemble the desired website. In reality, they are phishing websites attempting to obtain sensitive information such as passwords or account numbers.
Risks Related to DNS Poisoning and Spoofing:
The following are some of the most common risks of DNS poisoning and spoofing:
- Theft of data: Data theft can be especially profitable for DNS spoof attackers. Banking websites and well-known online retailers are easily spoofable, which means that any password, credit card, or personal information could be compromised. The redirects would be to phishing websites designed to steal personal information.
- Malware infection: Another common threat associated with DNS spoofing is malware infection. The destination of a spoof redirect could be a site infested with malicious downloads. Drive-by downloads are a simple way to infect someone’s system automatically. Finally, if internet security is not used, they become vulnerable to threats such as spyware, keyloggers, and worms.
- Security updates have been halted: A DNS spoof can cause security updates to be halted. Legitimate security updates will not be performed if spoofed sites include internet security providers. As a result, the computer may become vulnerable to new threats such as viruses or Trojans.
- Censorship: Censorship is a threat that is all too common in some parts of the world. China, for example, modifies the DNS to ensure that all websites viewed within the country are approved. The Great Firewall, a nation-level block, is one example of how powerful DNS spoofing can be.
Prevention:
There are several DNS security best practices available to help defend against attackers and keep systems safe and secure. Since DNS servers are constantly communicating with one another, the more companies that implement these best practices, the greater the overall protection. The following are the most important steps that should be taken to avoid DNS poisoning:
- DNSSEC (Domain name system security extensions): It is a type of protocol that can be used as a security extension, that is used to add additional methods of verification to our DNS in order to secure it. DNS messages can be authenticated using DNSSEC. This DNSSEC protocol generates a unique cryptographic signature, which is stored alongside our other DNS records. The DNS resolver then uses this signature to validate a DNS response. The DNSSEC system ensures that the DSN lookup remains spoof-free and authentic.
- Active Monitoring: It is critical to monitor DNS data for new patterns, such as the appearance of a new external host, which could indicate the presence of an attacker.
- Patches: DNS servers are vulnerable to exploits. Keeping up with the latest patches can protect against attackers looking to exploit these well-known flaws.
- DNS Updates: To help protect against DNS attackers, updated versions of DNS include port randomization and cryptographically secure transaction IDs. Make sure the server being used is always up-to-date.
- Policies Concerning Passwords: It is critical to implement password protection policies. A faulty router password could endanger every device and user in their organization.
- HTTPS Indicators: The HTTPS indicator should always be visible in the browser’s address bar. This indicates that the site is legitimate. If the appearance of the HTTPS indicator changes, it could indicate the start of an attack.
- Flush our DND cache: Because the system can tolerate cache poisoning for a long time, we should remove the injected data. This process is similar to opening a window, running programs, and typing “ipconfig /flushdns.” Android, iOS, and MAC users can also use the flush options. These are typically found in the URL of a specific native web browser or in the option of “network setting reset,” which allows us to toggle airplane mode by rebooting the device. We can refer to our specific device method for more information.
- End-to-end encryption: This method encrypts the DNS request for data and keeps attackers away since it is not possible for them to duplicate the website’s unique security license.
- Never click on an unknown link: Users occasionally click on a link that they are unfamiliar with. These links could appear in any text message, social media post, email, and so on. This should be avoided as much as possible since the link destinations can be further masked by URL shortening tools. In order to be secure in the address bar, the URL must be entered manually. After confirming that the website entered in the URL is official and legitimate, it can be safely visited.
- Use VPN: These services provide an encrypted tunnel for all web traffic. It also provides the end-to-end encrypted security that a private DNS server requires. As a consequence, it gives us requests that cannot be obstructed and servers that are much more resistant to DNS spoofing.




