Passwords can be cracked using a variety of techniques, including brute force attacks, social engineering, and dictionary attacks. In this article, we will look at Phishing and Social Engineering Techniques and how they can be used by attackers to crack passwords.
Phishing Attack:
Phishing is a simple and common method of cracking someone’s password. In which attackers create a false webpage or dashboard on which the user must enter sensitive information such as username and password. The webpage will appear valid or original, and the user will simply submit the details and be redirected to another page. Attackers will collect the information provided by the user. The webpage will be an exact copy of a legitimate website, and we will have a difficult time identifying it. For example, you may have seen posts with a link attached and the sender instructing you to click the link to earn rewards or money.
Please refer to the article What is Phishing ? to know more about this.
Social Engineering Toolkit:
Social Engineering Toolkit is a free and open-source tool to perform online social engineering attacks. Phishing is also a Social Engineering Attack. Now we will perform the Social Engineering attack in order to capture the password by creating a phishing website.
Please refer to the article Social Engineering and Social Engineering Toolkit to know more about this.
Requirements to perform this Attack:
Before you begin the attack, you must first install VirtualBox or VMware and configure the virtual machines listed below:
- Kali Linux Virtual Machine
- Windows Virtual Machine
To set up the required system, you can read tutorials and articles or watch YouTube videos. Follow this step-by-step procedure to carry out a social engineering attack in order to crack or collect the user’s password –
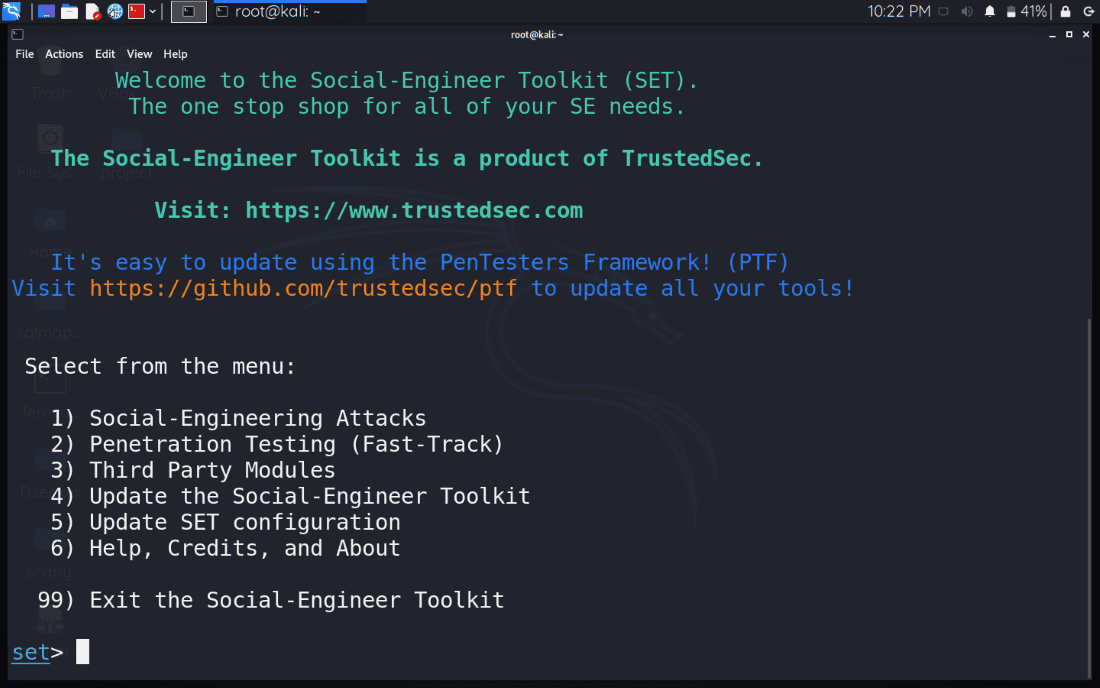
Step 1: Open the root terminal of your Kali Linux Virtual Machine and type “setoolkit” and press enter. You will see an interface similar to the one shown below.
Step 2: Select option 1 – “Social -Engineering Attacks” and press enter.
List of options
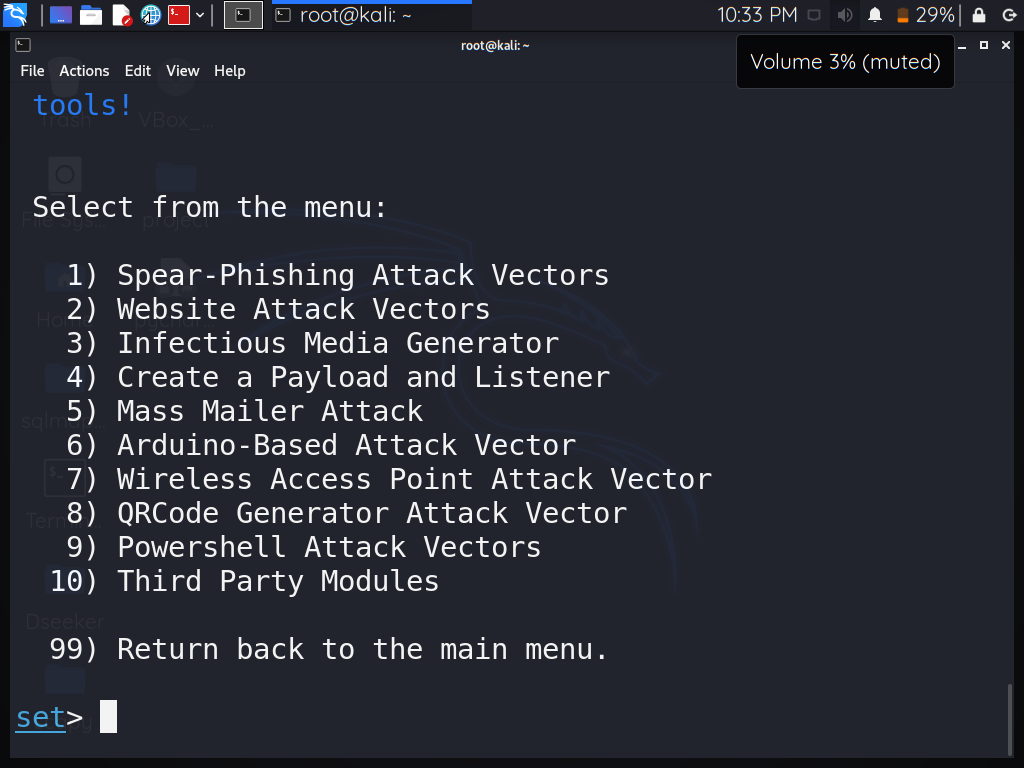
Step 3: Select option 2 – “Website Attack Vectors ” and press enter.
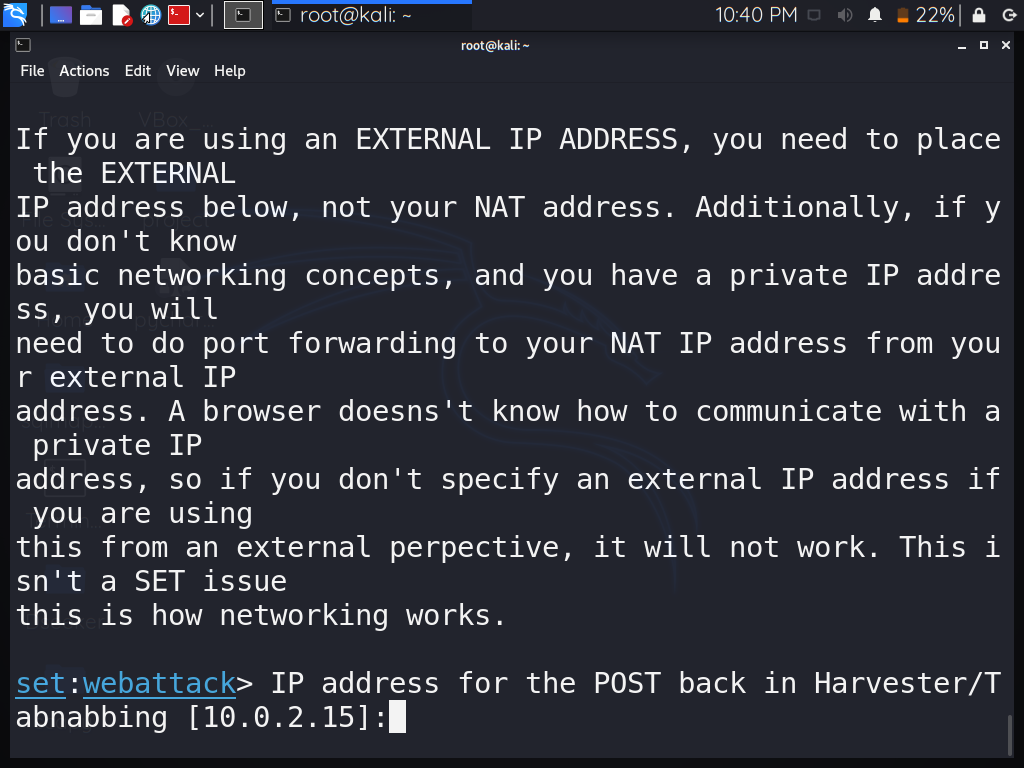
Step 4: It will prompt you to enter the IP address. Simply enter your Kali Linux IP address, or if the IP address is already displayed in the message, leave it blank and press enter.
Step 5: Select option 3 – “Credential Harvester Attack Method” and press enter.
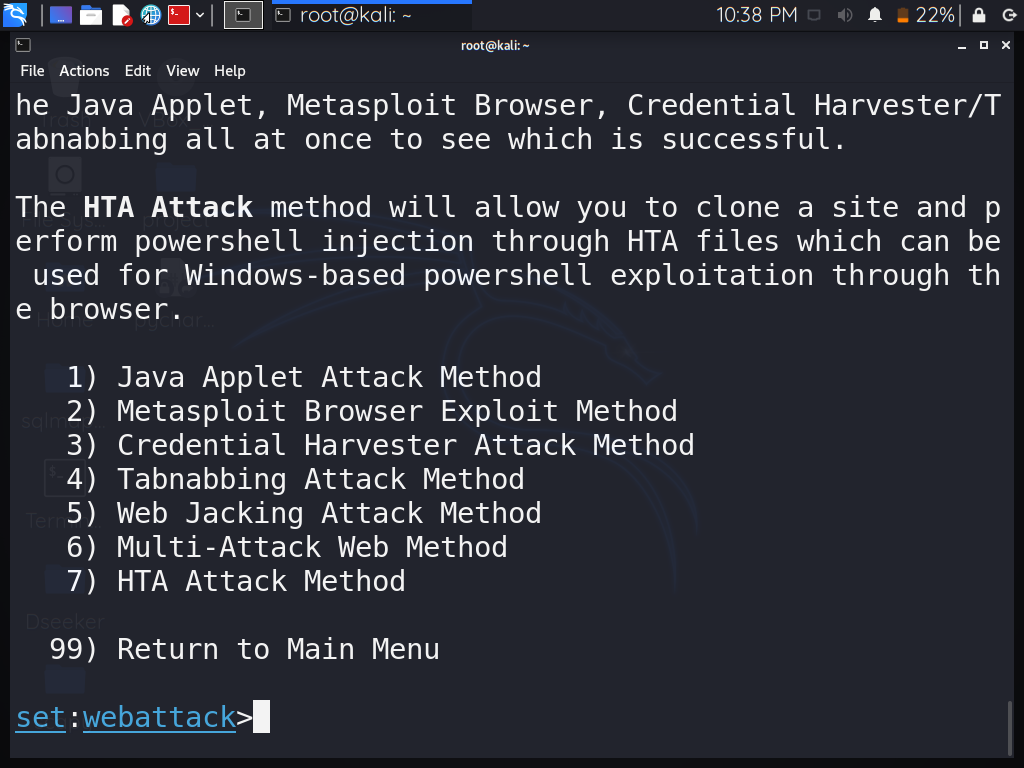
Step 6: Select option 1 – “Web Templates” and press enter.
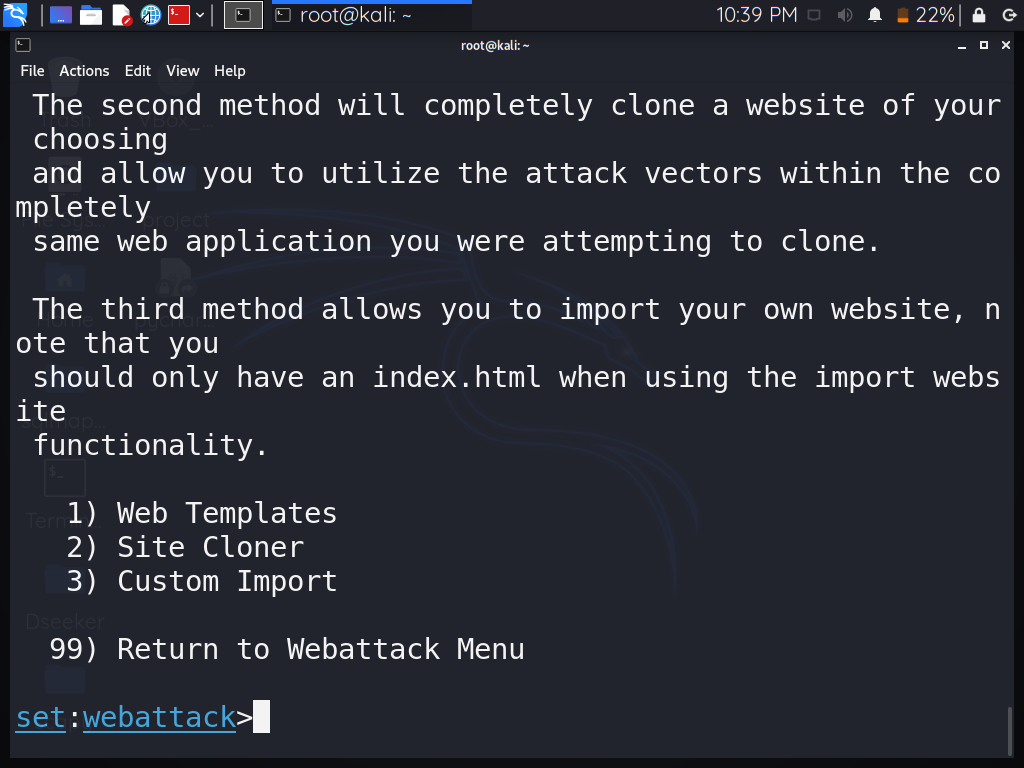
Step 7: Select a template. I will use Option 2 “Google” because I want to show the sign-in page of Google.
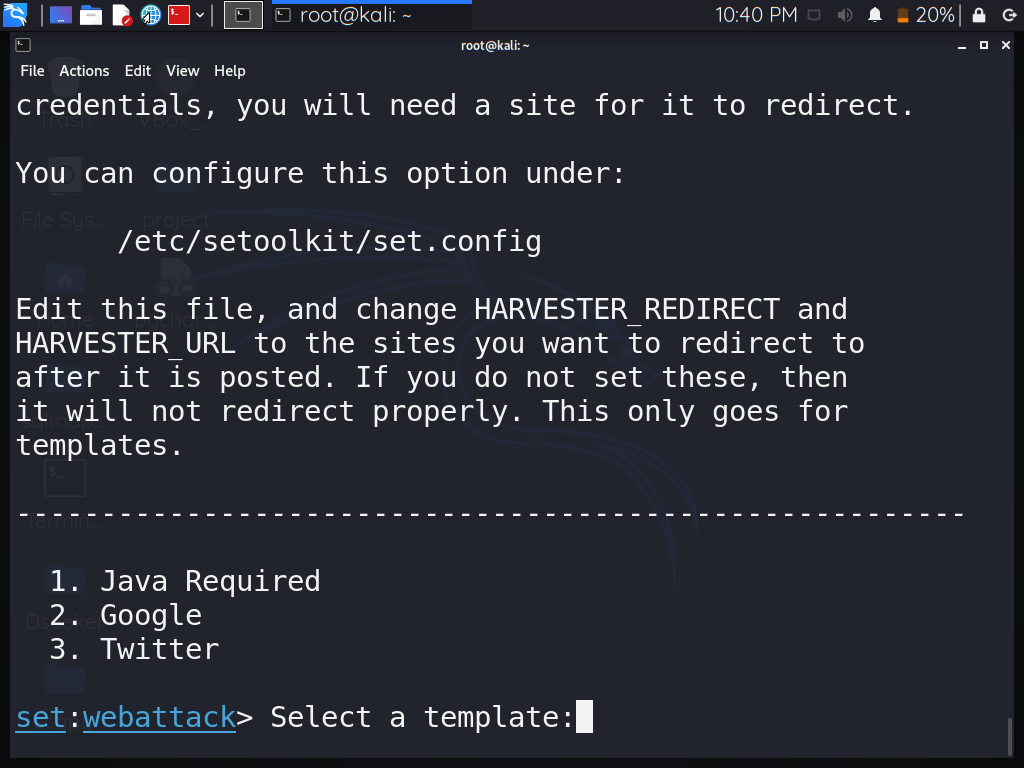
Step 8: The tool is currently in listening mode, waiting for the user to interact with the webpage that we created with this tool.
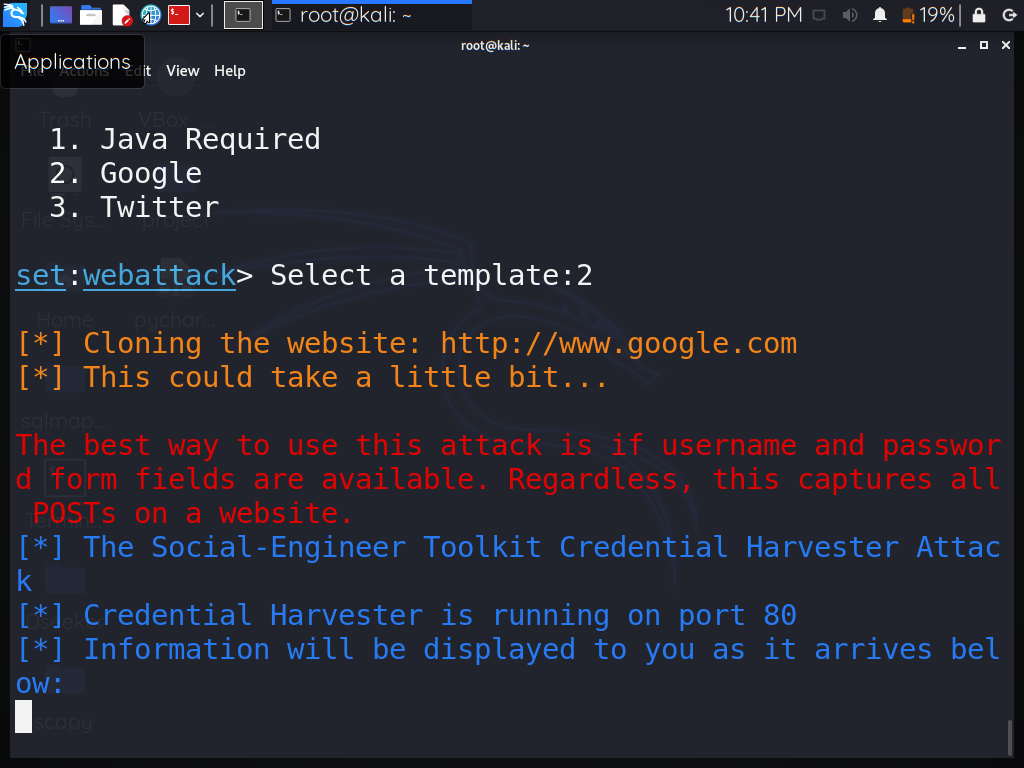
Step 9: To test, simply enter the IP address of your Kali machine into the web browser’s search bar because we shared our IP address with the tool when we built the site. A fake Google sign-in page appears.
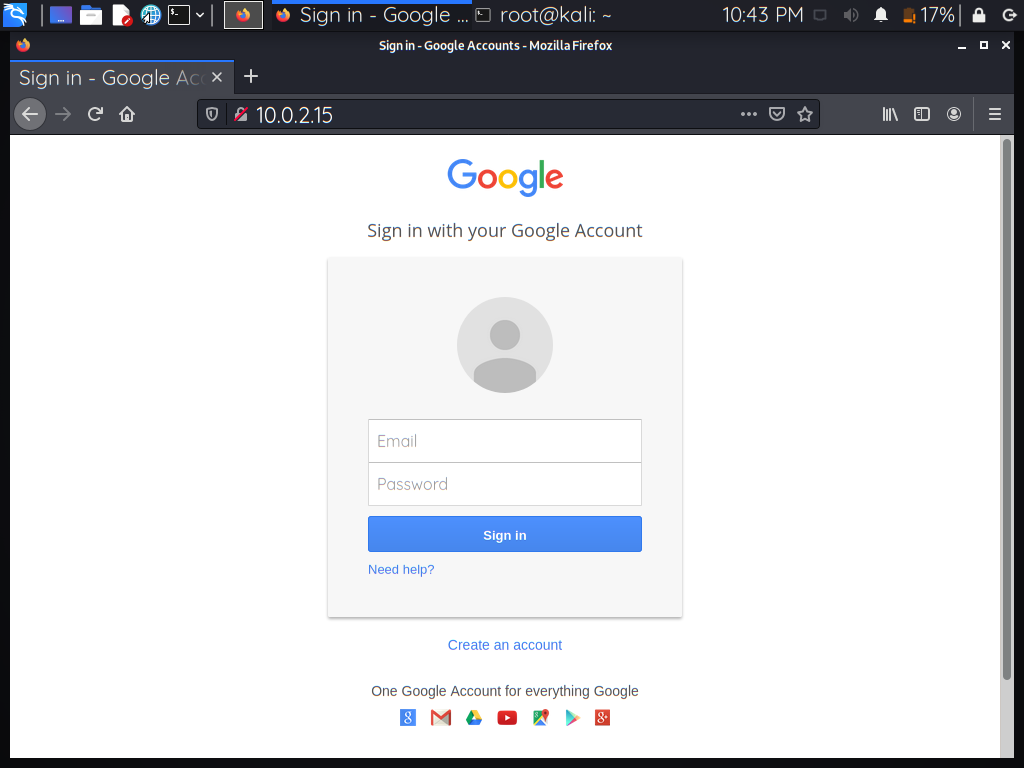
Step 10: When the user clicks on the sign-in button after filling out the required fields, the data is recorded in our terminal because our tool was waiting for the user to interact and share his/her personal information, and now the tool has the details.
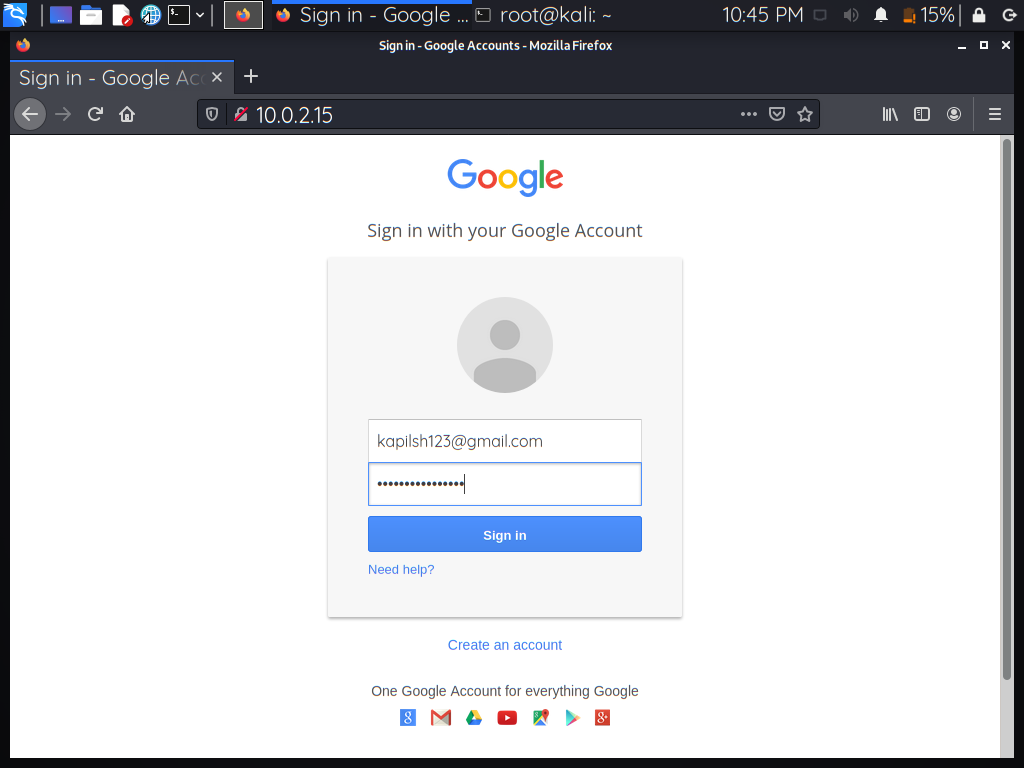
Step 11: After clicking the sign-in button, the user will be automatically redirected to another page.
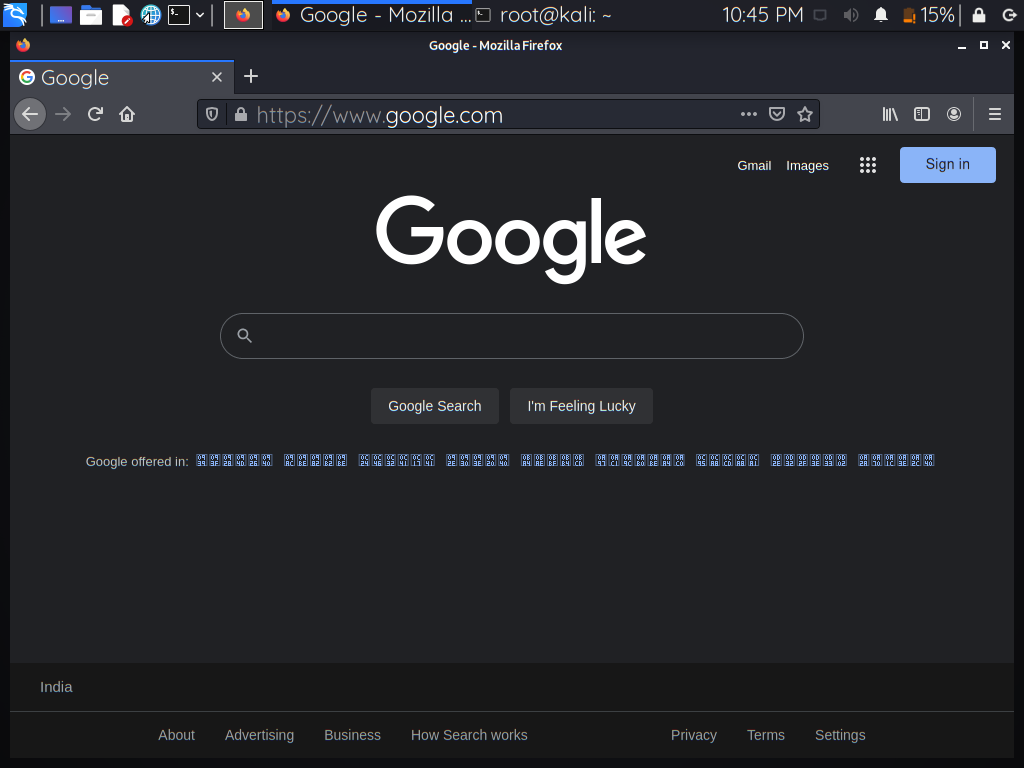
Step 12: Finally Go to your terminal and look for the user’s username or email address, as well as the password. The username and password are identical to what I entered on the sign-in page.
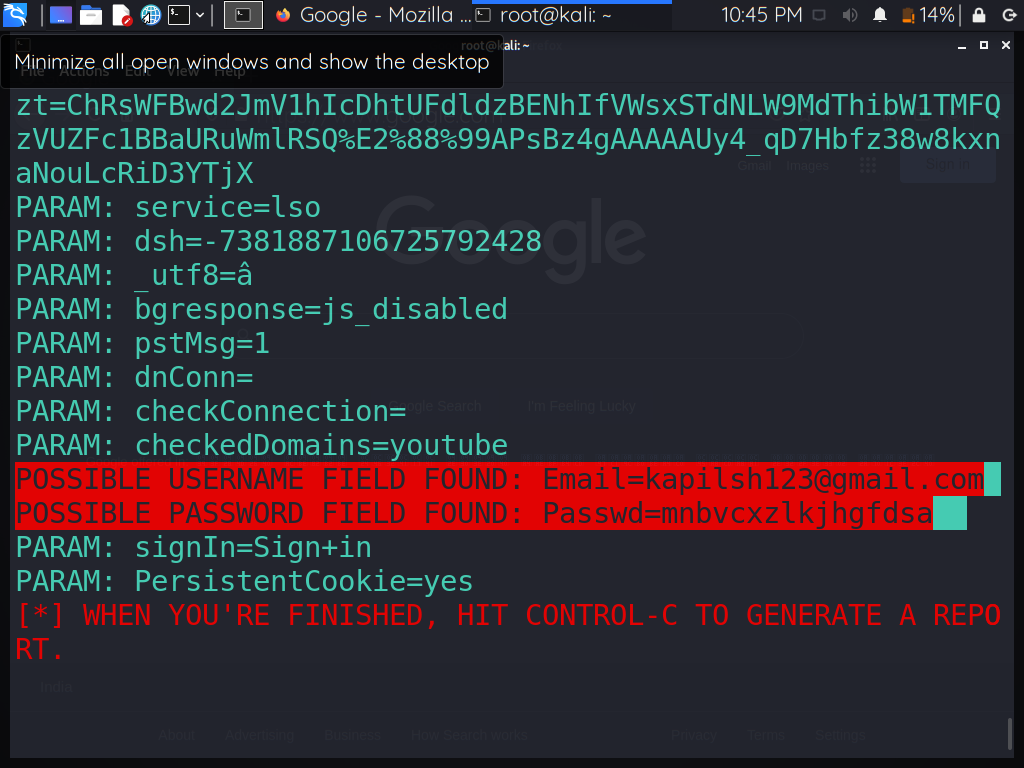
Conclusion:
Using the social engineering attack phishing, we successfully cracked the password.
Disclaimer: Use this information only for educational purposes.




