Configuring inbound (or incoming) traffic to your Linux instance is critical to setting up and managing your server’s security. Without properly configuring it, you risk having your instance compromised and all of your data stolen by a malicious user. This article will review how to configure inbound traffic rules on a Linux instance.
AWS is used here for demonstration purposes, but other services have similar steps and settings.
Incoming traffic rules can be configured in two ways:
- When making a new instance
- Editing the rules after the instance has been created
When making a new instance
Step 1:- Select Launch Instance from the EC2 dashboard to start a new instance.
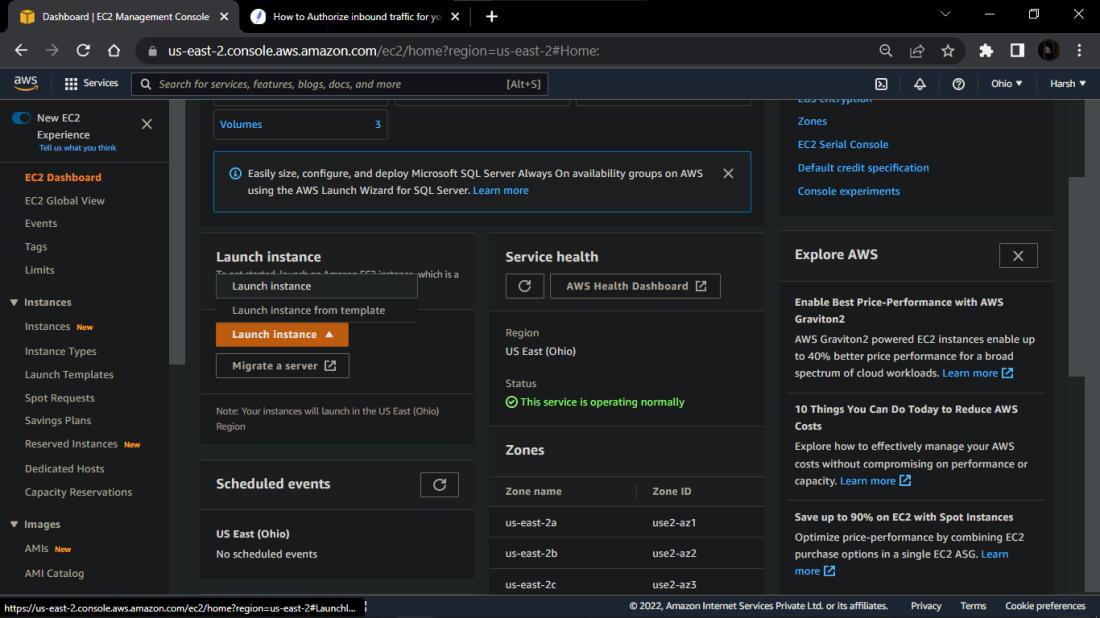
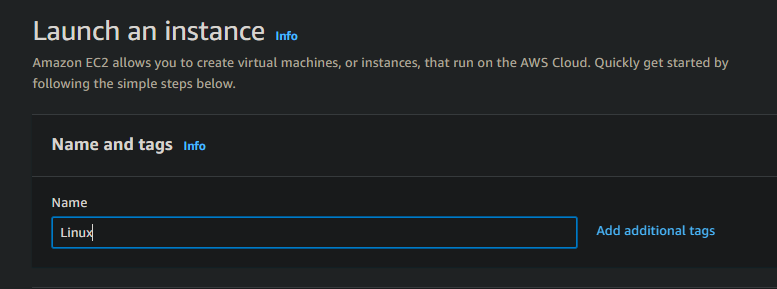
Step 2:- Give your instance a name of your wish.
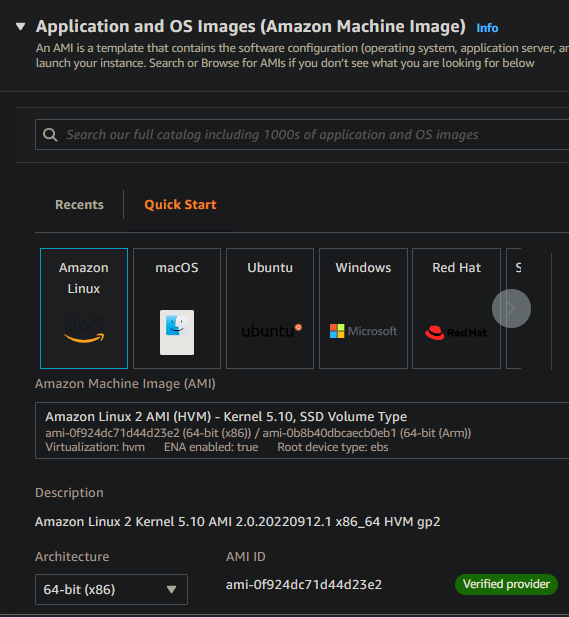
Step 3:- Choose the operating system for which you want to create an instance (Amazon Linux 2 AMI in this case)
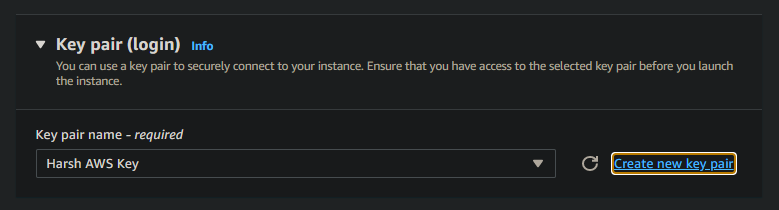
Step 4:- Choose a key pair for accessing your instance.
Step 5:- You can now configure your inbound traffic rules in Network settings.
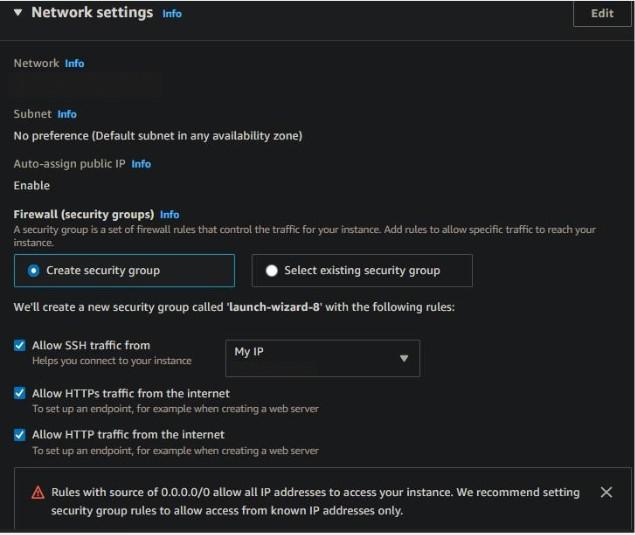
SSH – To connect to your server via the SSH protocol and grant external users access via port forwarding. By default, 0.0.0.0/0 is chosen, indicating that public access to your instance is enabled, allowing any client from any IP address to connect to your instance via SSH.
For more information: SSH
If you intend to access the instance only from your device, select My IP or a custom IP to only allow SSH traffic from that IP and decline if attempted from another.
HTTP and HTTPS – If you intend to run a web server on your instance, both of these options are critical and must be enabled to allow users to access the web server via ports 80 (default for HTTP) and 443 (default for HTTPS). If you only require HTTP access, select the HTTP-only option, which will disable HTTPS traffic.
For more information: HTTP & HTTPS
Step 6:- Allocate the necessary storage to your instance and choose Launch Instance. The instance will go live soon.
Editing the rules after the instance has been created
Follow these steps if you have already created an instance and want to change the inbound traffic rules.
Step 1:- Navigate to your instances list and choose the instance you want to edit.
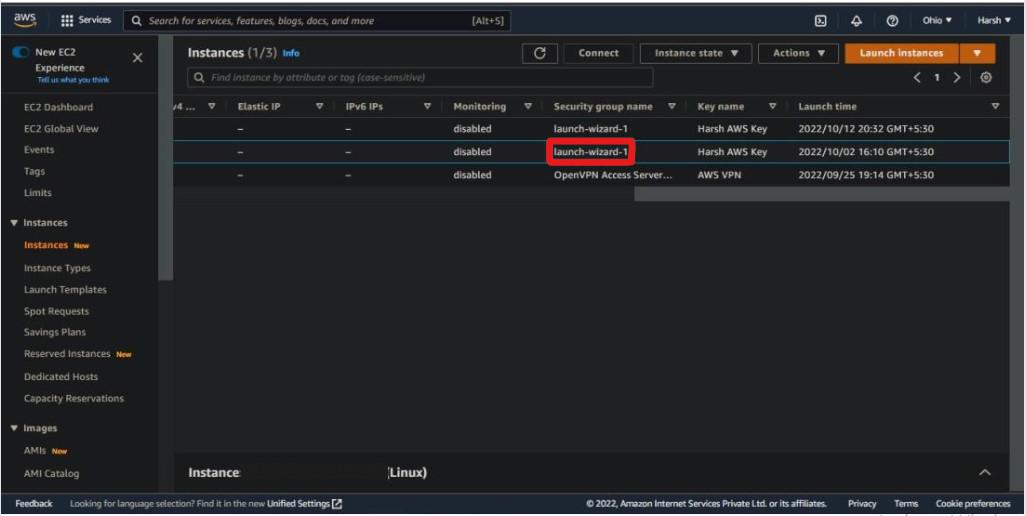
Step 2:- Now, scroll to the right and write down the name of the selected instance’s security group.
Step 3:- Scroll down in the left pane and select Security Groups from the Network & Security dropdown.
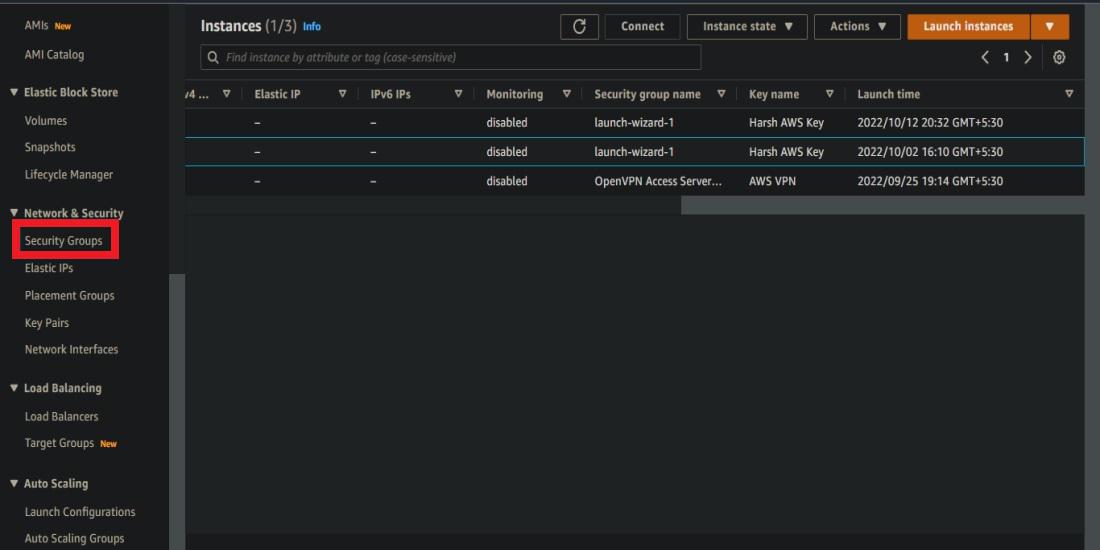
Step 4:- Select the security group for your instance.
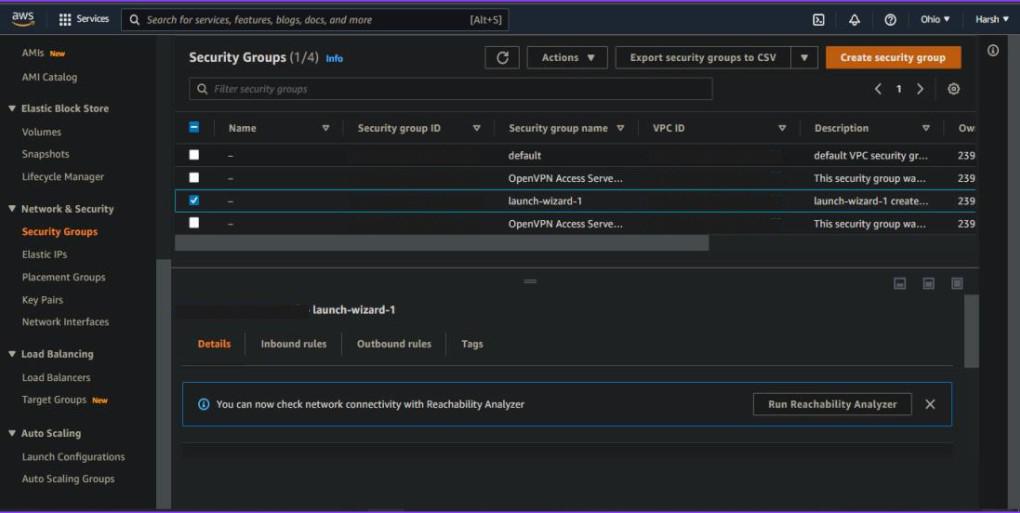
Step 5:- Select Edit Inbound Rules from the context menu.
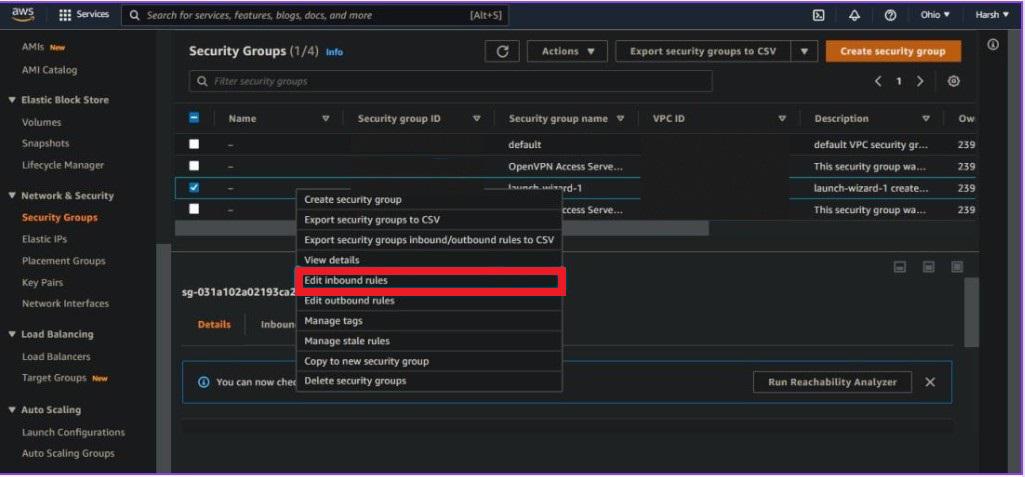
Step 6:- From here, you can add or remove the inbound traffic rules enabled for your instance and edit multiple rules.
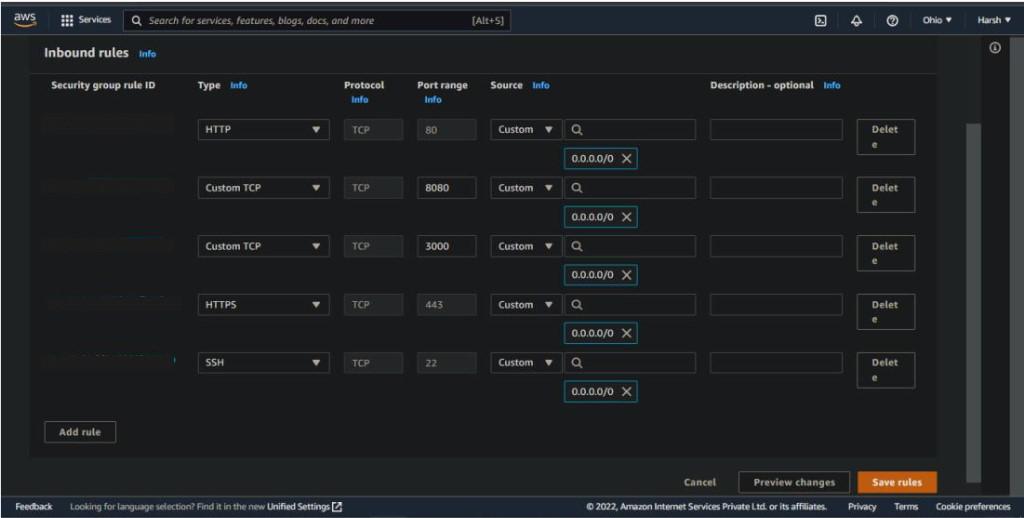
By adding custom TCP, we open a specific port and specify an IP address to access the service hosted on that specific port by only the specified IP address (0.0.0.0/0 means it can be accessed from any IP). For example, suppose you opened a port for your Web Site and want that traffic to be accessed only from your local computer. In that case, you can create an inbound rule and provide the port number you want to open as well as the inbound IP address, which in this case is your computer’s local IP address.
Adding rules, for inbound SSH traffic over IPv4 or IPv6
If you want to allow IPv4 or IPv6 traffic from any IP, select Anywhere – IPv4 or Anywhere – IPv6 from the drop-down choice for the Source column next to the SSH rule.
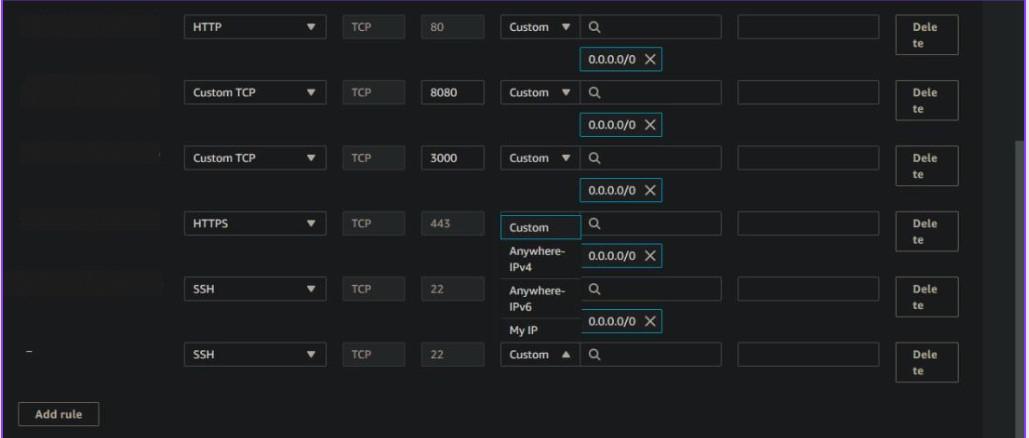
Or if you want to add a custom IP, click Custom and enter the IP address in the CIDR notation.
For instance: To add an IPv4 address, enter (XXX.XXX.XXX.XXX) 104.239.197.100, or (XXX.XXX.XXX.XXX/X) 104.239.197.100/32 for a specified port.
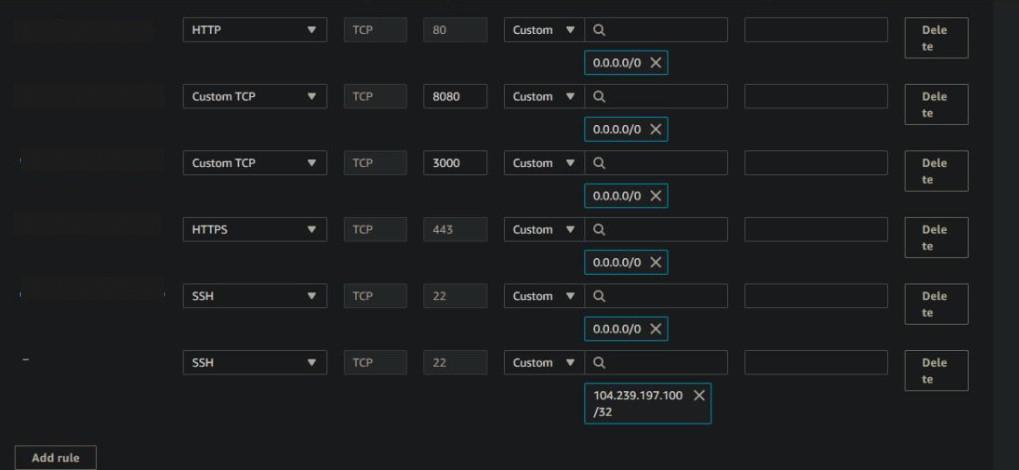
The address should be entered as 2001:0db8:85a3:0000:0000:8a2e:0370(/7334) for IPv6.
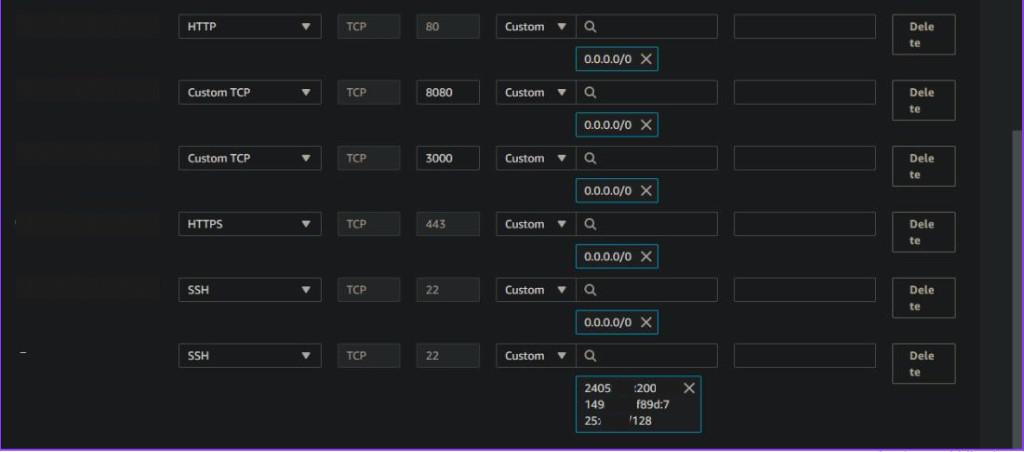
After making changes, click Save Rules to apply the changes, and you’re all set!
Assigning Security groups to an instance
Go to the All Instances tab, right-click on the instance you want to modify the security group for, and pick Security -> Change Security groups from the menu that appears.
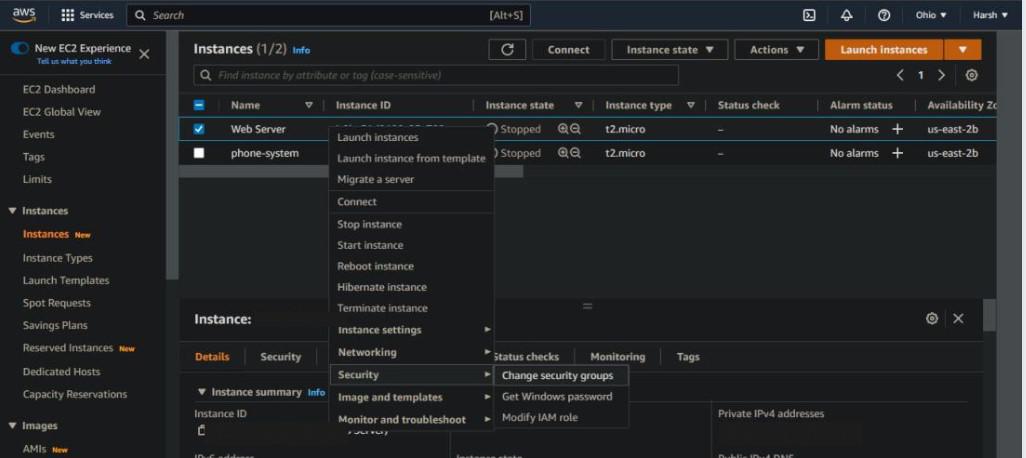
Now To assign an existing security group, first, click the search bar, then click Remove to remove the current security group.
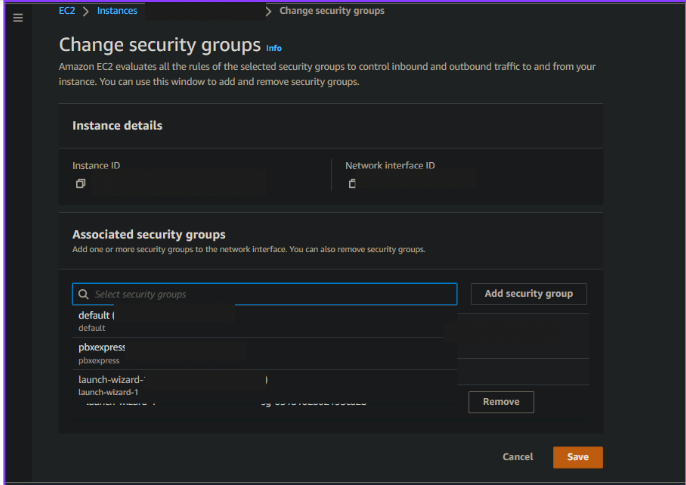
After making modifications, press Save to give the instance a new security group.




