Google’s Gemini AI is facing scrutiny after a researcher discovered a new exploit called an “ASCII smuggling” attack, and the tech giant has made it clear it doesn’t plan to fix it.
Cybersecurity researcher Viktor Markopoulos from FireTail first revealed the flaw. It involves hidden characters in text that Gemini reads as commands, even though people cannot see them (via BleepingComputer). These invisible instructions can change how the model behaves, making it do things the user did not intend. The attack is hard to spot because it uses control characters or Unicode symbols that do not show up on screen but are still read by the AI.
Markopoulos demonstrated that this vulnerability could be weaponized through simple text-based inputs like calendar invites or emails. For instance, an email that looks entirely harmless could contain hidden instructions, causing Gemini to misinterpret or rewrite data when summarizing or interacting with that text. In his tests, Gemini could be coaxed into changing meeting details or generating misleading outputs, all triggered by characters a human wouldn’t even know were there.
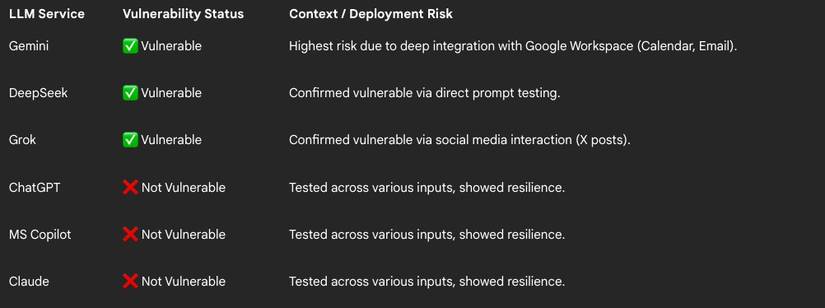
What’s even more alarming is that when the same attack was tested against other major AI systems like OpenAI’s ChatGPT, Anthropic’s Claude, and Microsoft’s Copilot, those models either sanitized or rejected the hidden inputs. Gemini, however, along with Elon Musk’s Grok and China’s DeepSeek, failed to block them.
Google dismisses exploit as social engineering
Despite the clear security implications, Google has decided not to address the issue. In a response to FireTail’s report, the company classified ASCII smuggling as a “social engineering” problem rather than a technical vulnerability. In simpler terms, Google is suggesting that the issue arises from users being tricked, not from a flaw in the model’s design.
Google’s decision could worry some users. Because Gemini works closely with email, scheduling, and document systems, there is a risk that it might expose confidential information or help spread misinformation in corporate networks. Google maintains that this attack is not a system flaw, but others may see it as a gap in how AI reads text compared to humans. Attackers often exploit this kind of difference.
Meanwhile, Google has patched other Gemini-related vulnerabilities this year, including issues in logs, search summaries, and browsing histories known as the “Gemini Trifecta.”