A footprint is a digital trace of your activity that you leave behind on the Internet. It is like the footprint you leave behind in the sand at the beach. These footprints can be innocuous, such as an e-mail account that you have forgotten about in Hotmail, or they can give away highly sensitive information through your browsing history on your work computer. Footprints also include information about what social networks and other websites people visit, what content they look at and for how long, who their Facebook friends are, and when they were last online; all this data is available with just one click to Google or to a range of specialized search engines.
Primary Sources:
In general, websites and search engines like Google and Bing allow you to create a footprint about yourself by disclosing your name, address, phone numbers, and other information about yourself. This information is then stored and can be found by anyone. Information about you on the web may be used to identify additional information about your social networks or connections. There are a number of software tools that can help find out more information about a person, company, or organization that has been the subject of an investigation. These include:
- Footprinting is essential to identity theft hackers, who must gather as much detailed information on the identities and activities of their targets as possible in order to establish whether enough evidence exists for them to consider a fraud report to the police.
- The Internet allows for a revolution in the way people collect personal information.
- The tool which has been used is e-mail passwords, which are emails that have been sent by an email address.
- This makes it easy for criminals to steal the password for the e-mail and thus gain access to all of their online activities and a lot of their personal information.
- There are many people that do not use their passwords and do not change them often. There are also many people that choose not to use a password at all and still use the same password over and over again.
Installation of Reconwolf Tool on Kali Linux OS:
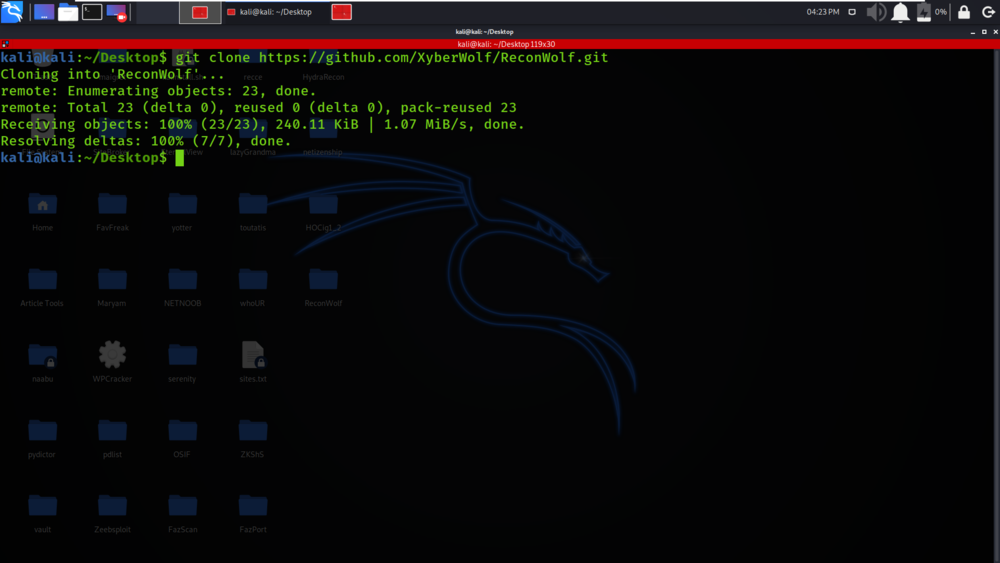
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/XyberWolf/ReconWolf.git
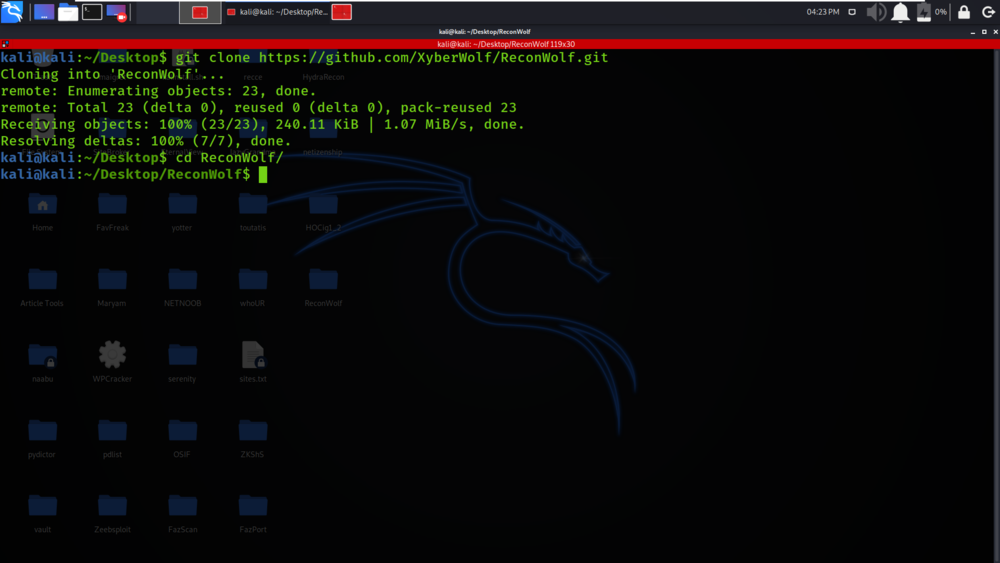
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd ReconWolf
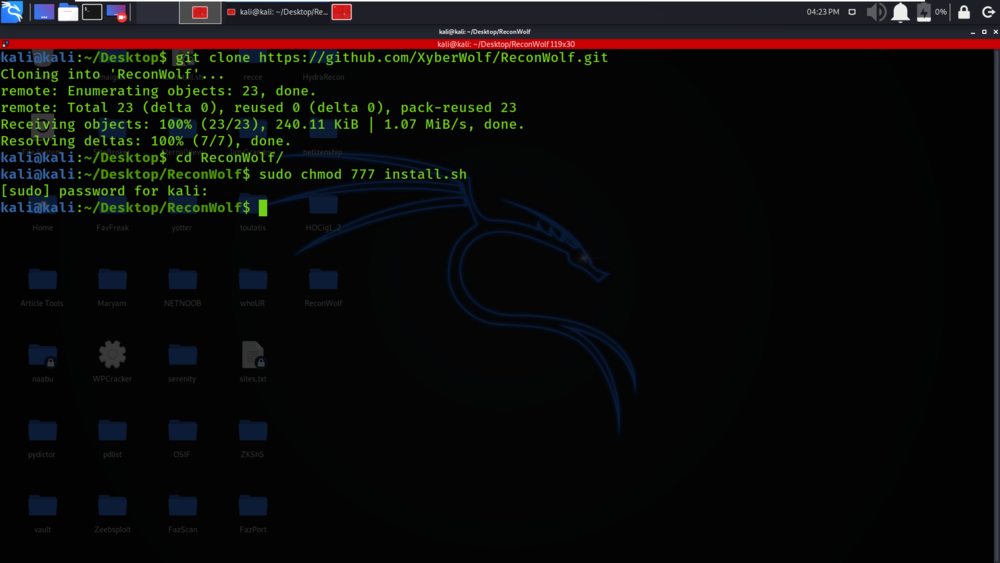
Step 3: Change the permissions of the install.sh file by using the following command.
sudo chmod 777 install.sh
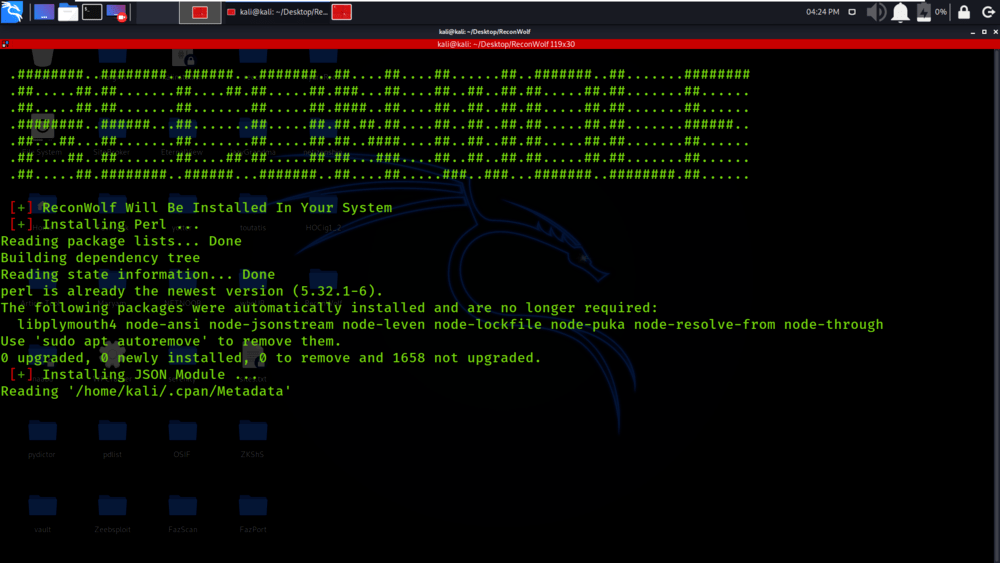
Step 4: Run the below command to verify the installation.
./install.sh
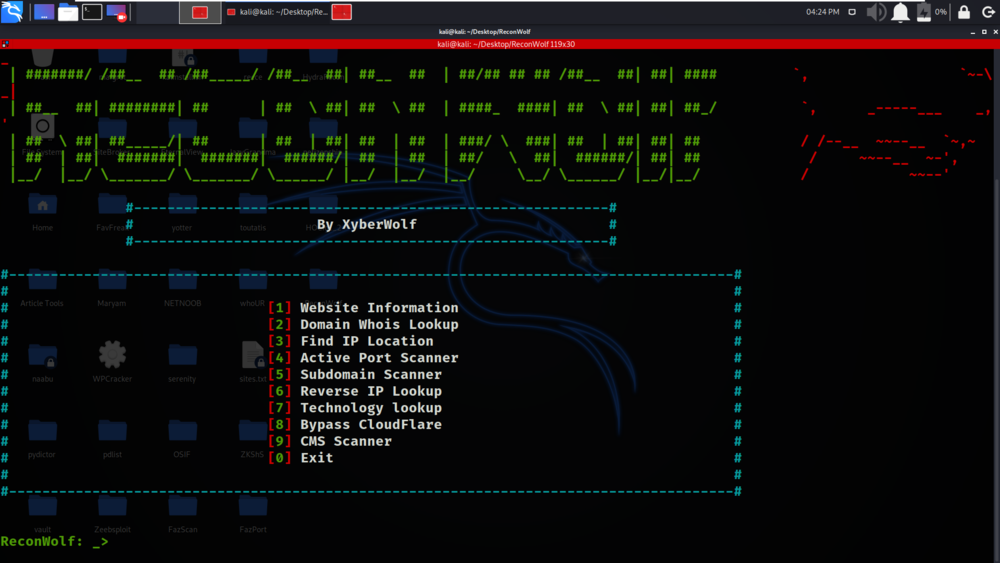
For more details, you can refer to the article: Reconwolf – Web Footprinting Tool in Linux
Countermeasures:
In most cases, when someone is using their username and password, that is the same as their email address or an e-mail from another provider, then this just adds to the list of information that is on the thief’s computer. What you want to do is make sure that the username and password aren’t something that can be found online by anyone.
- Using an IP address: An IP (Internet Protocol) address is a number given to devices connected to the Internet. It lets devices know where they are geographically so that they can send data back and forth across networks and computers properly. Sometimes, though, these numbers can be used as tracking measures as well, which could reveal a person’s location through their computer. Some computers make it simple to obtain their IP address by using their computer’s built-in Internet connection, but this can also be achieved by using a proxy server. Proxy servers are often used for anonymizing internet traffic.
- Using search queries: If your IP address is only one of many being searched, then in most cases the search results will note an IP address first and won’t even bother to look for other information. Anonymizers are sometimes used so that no information is given away at all if possible.
Using geolocation: In the United States, software such as Google and Foursquare are available to help locate a person’s location using their IP address. In some cases, this can be traced back to the individual who was using their computer at that time. - Where possible, using alternative services: Most commonly people will use their e-mail or browser settings to try and mask their actual IP address. If they have used a proxy server though or are accessing other encrypted websites then there is no way of finding out that they have done so. This is one reason why anonymizers should not be used since it reveals exactly where you are located geographically.
Conclusion:
There are many ways that your digital footprint can be collected and used against you. This can be done by a third party or even by yourself. In most cases using search engines like Google, Bing and Yahoo! will be the easiest way to find out information about you or anyone else that has an e-mail address.
A great deal of effort is put into trying to cover up all the information on the internet about you, but once it is out there it can never really be taken back. It may not become public knowledge immediately, but if someone wants to learn something then they will most likely find what they are looking for eventually.




