This program is available on all Microsoft Windows servers (usually port 5985) that have this feature enabled. Of course, only if you have the credentials and permissions to use it. Therefore, it could be used during the post-exploitation hacking/penetration testing phase. The purpose of this program is to provide convenient and easy-to-use features for hacking. It can also be used by system administrators for legitimate purposes, but most of its functionality is focused on hacking/penetration testing.
Installation:
Step 1: You can install evil-winrm directly with the help of Ruby Gem. Running the following command will automatically install all dependencies on your computer.
sudo install evil-winrm
Step 2: Once installed, you can type “evil-winrm” to get the HELP option. It shows the syntax and other operators for running Evil-winrm against the Windows Remote Management service.
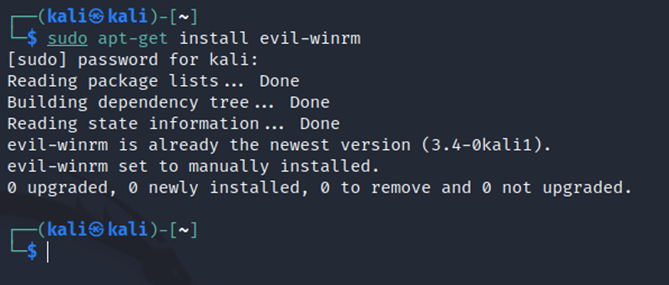
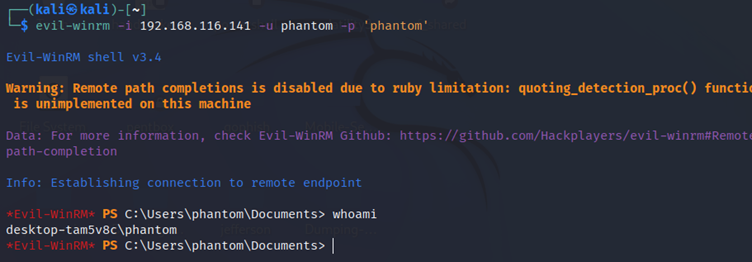
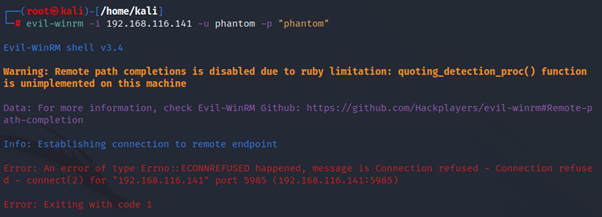
Step 3: Now try to access the remote machine shell using evil-winrm by connecting to the open port 5985 for winrm. As a result, it grants access to the victim’s shell by providing PowerShell as follows:
Syntax: evil-winrm -i <Windows IP> -u <username> -p <’password’>
evil-winrm -i 192.168.116.141 -u phantom -p 'phantom'
Step 4: It will not only provide a shell of the host machine but also provide a menu to load functions such as Invoke-Binary, Dll-Loader, Donut-Loader, and Bypass-4MSI.
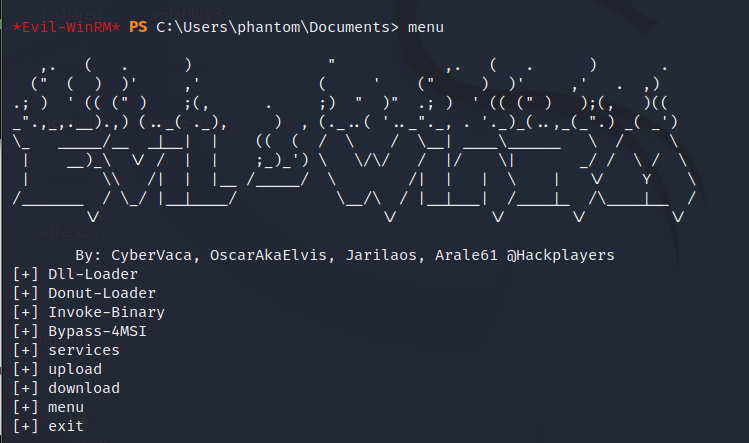
Error Solving:
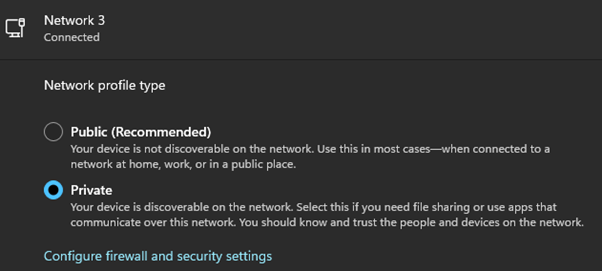
Step 1: If evil-winrm is not connecting, put the network in the private network
Step 2: Type the following commands in PowerShell administrator mode:
Enable-PSRemoting -Force
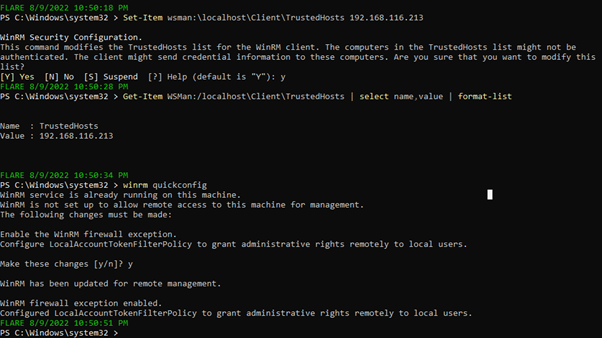
Step 3: Check whether your machine IP is added to the Windows system or not
Get-Item WSMan:/localhost/CLient /TrustedHosts | select name,value | format-list
Step 4: If the IP of your system is not added to the Windows system
Set-Item WSMan:/localhost/ CLient/TrustedHosts <Kali IP>
Step 5: To start the winrm service in the Windows system, use this command.
winrm quickconfig
Feeling lost in OS, DBMS, CN, SQL, and DSA chaos? Our Complete Interview Preparation Course is the ultimate guide to conquer placements. Trusted by over 100,000+ lazyroar, this course is your roadmap to interview triumph.
Ready to dive in? Explore our Free Demo Content and join our Complete Interview Preparation course.




