Zeus is a powerful and pervasive botnet that has been designed to steal information from infected computers, mainly banking credentials such as logins and passwords. Zeus was first detected in 2007 and has since grown to prominence as one of the most prolific malware families, with over one million infected computers worldwide at its peak in 2011. One of the most notorious features of Zeus is that it captures information on every keystroke performed by its victim, giving it access not only to banking logins but also passwords for email accounts and other high-value sites. This means that users can be hit by malware through a variety of vectors, from email attachments or links in chat messages to drive-by downloads on vulnerable web pages.
Impacts of Zeus:
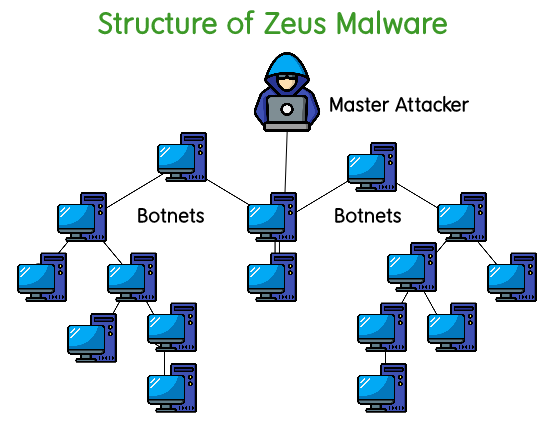
Zeus’ virus can do a lot of suspicious things once it infects your computer, but it really has two main functions. First, create a botnet. This is a network of corrupted machines secretly controlled by a command and control server under the control of the malware owner. Botnets allow their owners to gather vast amounts of information or launch large-scale attacks. Zeus also functions as a financial services Trojan designed to steal banking information from infected computers. This is accomplished through website monitoring and keylogging. The malware detects that the user is on her bank’s website and records the keystrokes used to log in. This means that the keystrokes required to log in are recorded as user types, allowing Trojans to bypass the security of these websites. Some forms of this malware also affect mobile devices and attempt to circumvent two-factor authentication, which is becoming increasingly common in the world of financial services. Initially, the Trojan only impacted computers running versions of the Microsoft Windows operating system, but new versions of the malware have been found on his Symbian, BlackBerry, and Android mobile devices. The malware author released his Zeus source code in 2011, opening the door for creating numerous new and updated versions of the malware. Today, the Trojan survives, but the original Zeus malware has been largely neutralized as its components are used (and built) in a number of newer malware.
Capability of Zeus:
Zeus uses a “man-in-the-browser” attack that monitors web traffic and intercepts sensitive information such as usernames and passwords, thus bypassing two-factor authentication. These credentials are then sent back to the botnet controller, who may use them to commit fraud or further infect the victim’s computer by downloading other malware. The Zeus code is very sophisticated; it allows the botnet operator to remotely install new features in infected computers. Zeus was reported to be used for financial fraud and theft of user credentials for online banking, payment processors, auction sites, stockbrokers, money transfer agencies, gaming sites, and social networks.
Zeus also steals is a non-exhaustive list from Secure Works security researchers.
- Data submitted in an HTTP form
- Account credentials stored in protected Windows storage
- Her X.509 public key infrastructure (PKI) certificate on the client side.
- Credentials for FTP and POP accounts
- HTTP and Flash cookies.
Initialization of Zeus:
Zeus Trojan/malware can be initialized on any system by two methods:
- Spam messages: Spam messages are frequently sent in the form of emails, but there are social media campaigns designed to spread malware through messages and posts on social media websites. When users click on links in emails or messages, they are redirected to websites that automatically install malware. Because this malware is adept at stealing credentials, it can be configured to steal email and social media credentials, allowing botnets to spam messages from trusted sources and greatly increase their reach.
- Drive-by downloads: Drive-by downloads occur when hackers can bring down legitimate websites by injecting malicious code into websites that users trust. The malware then installs itself when the user visits her website or when the user downloads and installs a harmless program.
Conclusion:
Zeus has been listed in the “Hacker’s Choice” section of Virus Bulletin since July 2007. In 2007, Zeus Trojan malware was created by programmers with nicknames ybbob and hlux. In 2010, cyber criminals used Zeus Trojan malware and its variants to install malicious software called ransomware, or Cryptolocker. According to Wikipedia, Cryptolocker is a type of ransomware that infects devices running Microsoft Windows. It is typically spread by e-mail with malicious attachments that exploit unpatched security vulnerabilities in a computer’s operating system or browser.




