A Trojan virus, or Trojan malware, is actually malicious code or software that looks legitimate to the victim but can take full control over the victim’s computer. It is designed to steal, manipulate, disrupt, damage, or do some other destructive action on your data, network, and computer system.
Malicious Activities of Trojans :
Trojans are not able to self-replicate. While a virus can spread to other devices by creating copies of itself and attaching them to the infected computer’s software, files, and folders. They can perform the following malicious activities while residing inside the host system :
- Steal confidential data and sent it back to the attacker.
- Copy and manipulate data.
- Delete and damage important data.
- It can read passwords.
- Record keyboard strokes.
- Open an undetectable backdoor.
Methods to Remove Trojans:
Method 1: Scan with Microsoft Windows Defender.
Microsoft Windows Defender is antivirus software that comes pre-installed with Microsoft Windows. It also provides real-time protection against viruses, spyware, and malware, helping to protect the operating system from infection. To scan the computer running, Windows OS follows the below steps.
Step 1: In the search box, type ‘Windows Security’ and click on “Virus & Threat Protection”.
Step 2: Now click on “Scan Option” then select “Full Scan” and click on “Scan now” to start the full device scan.
Method 2: Restore System from Snapshots.
System Restore is a tool designed to repair computer software. It takes a “snapshot” of some system files and the Windows registry and saves them as Restore Points. In case of any failures or data corruption, the system can be restored back to normal working conditions without having to reinstall the operating system.
Therefore, in case of a trojan infection, system can be restored from the snapshots. The system will restore the uninfected files only if you have a snapshot or a restore point of the system which is taken before the Trojan appeared on your computer.
To create a restore point or to take a snapshot of the system, follow the below steps :
- Type “Restore” on the Windows Search bar and click on “Create a Restore Point”.
- Under the “System Protection tab”, click on “Create” to create a restore point only for the drives that have system protection turned on.
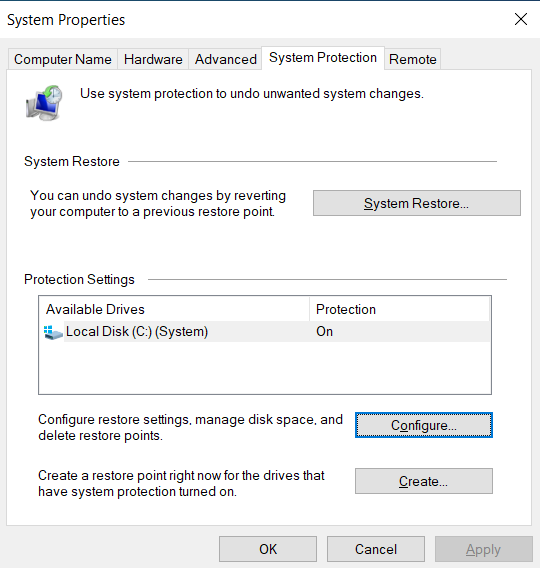
Windows System Protection
- Now give the description of the restore point in the dialogue box that appears.
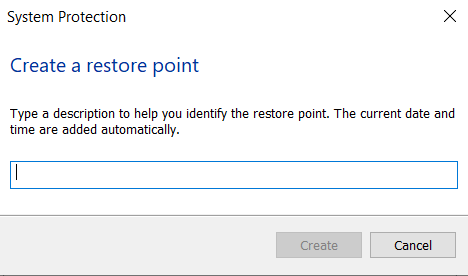
Description of the Snapshot
To restore the system from the snapshot taken above follow the below steps :
- Under the “System Protection tab”, click on “System Restore” and then click on “Next”.
- Select the restore point where the system was working perfectly, and click on “Next”. Finally, click on “Finish”. Your PC will then restart, and your system will restore itself back to its normal condition.
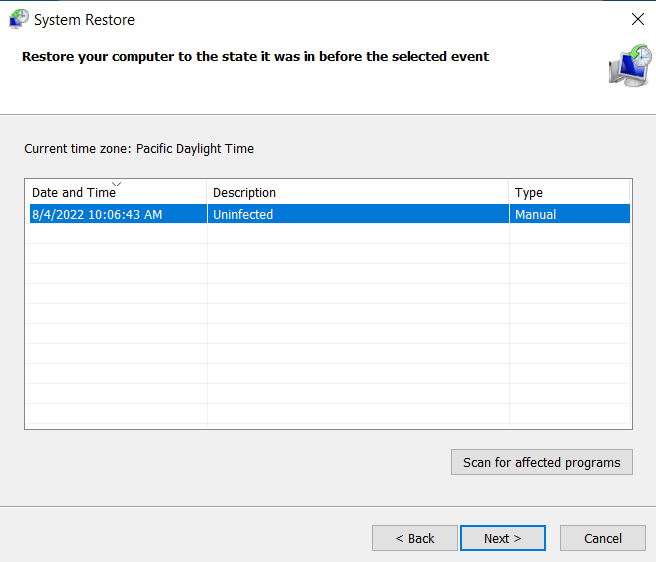
Windows System Restore
Method 3: Windows Safe mode.
A safe mode is a troubleshooting option for windows that starts the computer in a limited state. Only the basic files and the drivers necessary to run Windows are started. Therefore if there are any trojans they can easily be spotted and deleted from the system.
Steps to enter the Safe mode in Windows :
- Search for “System Configuration” or just type “MSCONFIG” and click on run as administrator.
- In the System Configuration dialogue box, click on the “Boot” tab and then tick the Safe mode >> Network.
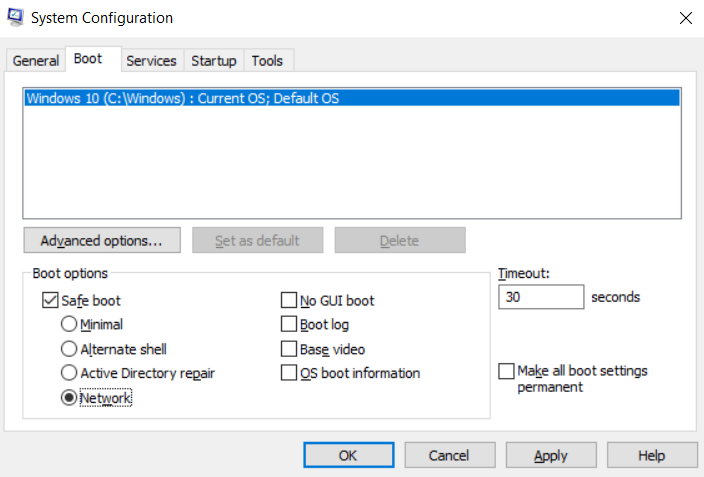
Windows System Configuration
- Click on apply and then ok to restart the Windows in safe mode.
Windows Safe Mode
- Now open the System Configuration box again and click on the “Startup” tab. Check for any suspicious files in the list. If you find something unusual remove it.
We must choose the “Safe Mode with Networking” option since that will allow us to download and update the tools if needed we need to fight off the trojan malware.
Method 4: Use a Reliable Anti-Virus Software.
Antivirus software is the best, easiest, and most reliable way to keep your device safe from all types of cybersecurity threats. Antiviruses are able to quickly detect and safely remove these threats from your devices. It will scan all the files on your computer as well as the files you download from the internet. It will also scan your file system periodically to detect and remove any malicious software on the computer. Some of the commonly used and reliable antivirus software available in the market are McAfee, Norton 360, TotalAV, Bitdefender etc.
Method 5: Full Reset or Factory Reset of the System.
A Factory Reset erases all of the information on an electronic device and restores the software to its original state. This means all your apps, files and folder will be deleted. Only apps that come pre-installed by the manufacturer will only be reinstalled. It will remove all unwanted or any newly installed executable files. Since if there is any infection it will get removed but there is no way to recover the important files and folders and previously installed apps.
To fully reset the Windows system follow the below steps :
- Type “Reset this PC” on the Windows search box, then click “Get Started”.
Windows Reset
- Click Remove everything to remove all your personal files, apps and setting and to erase all data securely.
- Click on Next if there is a warning you won’t be able to revert to the prior version of Windows.
- Click on Reset when you see Ready to reset this PC.




