Ransomware is a malicious malware code specifically designed to deny users access to their own systems until a ransom payment is paid to the ransomware creator to obtain a decryption key. Far more dangerous than normal malware, ransomware is spread through phishing emails with malicious files, links, or other attachments.
CryptoLocker Ransomware Attack:
Cryptolocker ransomware is a malicious malware code that infects a computer with a Trojan horse and then looks for files to encrypt. The target of the attack is a computer running Microsoft Windows. It starts to infect as soon as it enters the system, with asymmetric encryption it locks the files. Asymmetric encryption methods are based on two keys, one public and one private. The attacker encrypts the data with the public key but holds the unique private key for decryption. The attacker asks for ransom payment by giving a private key for decryption. otherwise, all data will be destroyed.
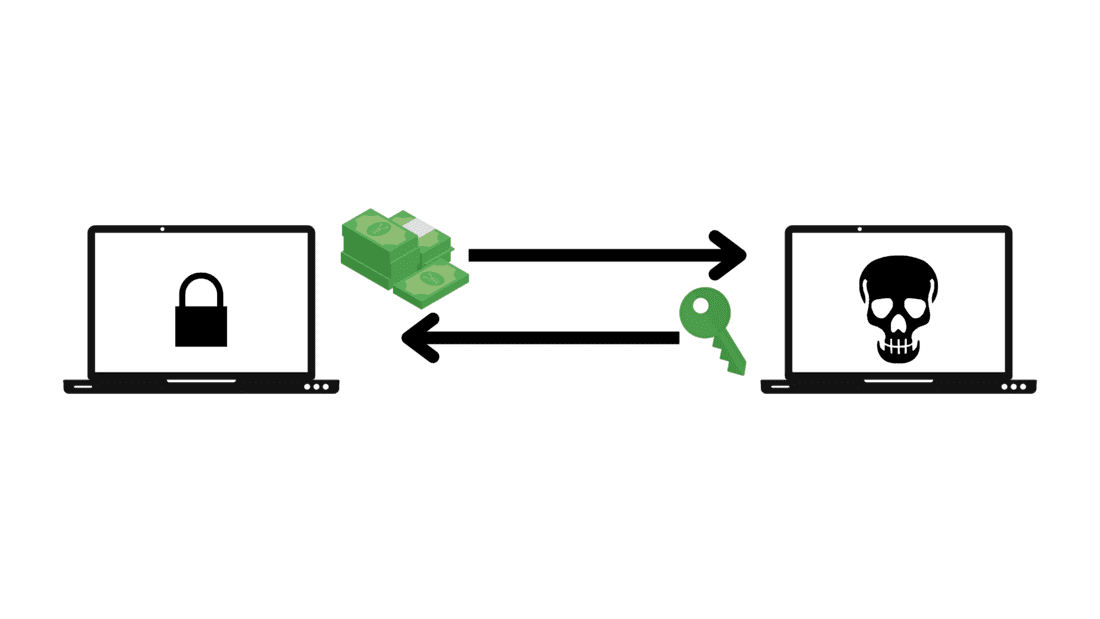
Cryptolocker can cause serious damage to the computer and devices. The primary means of Cryptolocker infection is phishing emails with malicious file, link, or other attachments.
Key points:
- It attacks the user with Trojan horse who uses Microsoft Windows most.
- It uses asymmetric encryption to lock the target user’s files.
- There are two keys, one is the public key for encryption and the other is the private key for decryption.
- For decryption, the attacker hold the unique private key and demands a ransom payment to share the private key.
- The primary mean of spreading cryptolocker ransomware is phishing emails.
Preventive Measures:
- Backup your files regularly to reduce data loss.
- Never Click on attachments from unknown sender in emails.
- Avoid downloading various types of unknown files, such as archive files (.zip, .rar), etc., because attacker hide malicious programs in these types of files.
- Download files, software etc. from verified sources.
- Protect your device or computer from all known and unknown viruses, malware, etc. with a powerful updated security suite and antivirus software.
- Always up-to-date your software, operating system.




