Cookie tampering is a method in which the attacker manipulates or modifies the information of the stored data on a web browser. This includes all types of data like personal information (name, number, address), and credentials for certain websites, or it can be the settings for specific websites. it is intended to steal valuable information from users.
Cookie Tampering Techniques:
Cookie tampering can be done with session hijacking attacks, cookie poisoning, and many more. Cookie tampering techniques include:
1. Manipulating in Browser: In this method, the cookies that are stored on the client side with the browser itself are manipulated, the easiest way to do this is with Firefox developer tools, the Cookie command is extensive and allows you to list, delete, edit and add cookies. With this, an attacker can send a malicious URL to the user and then take a response from the server which contains valuable information about users.
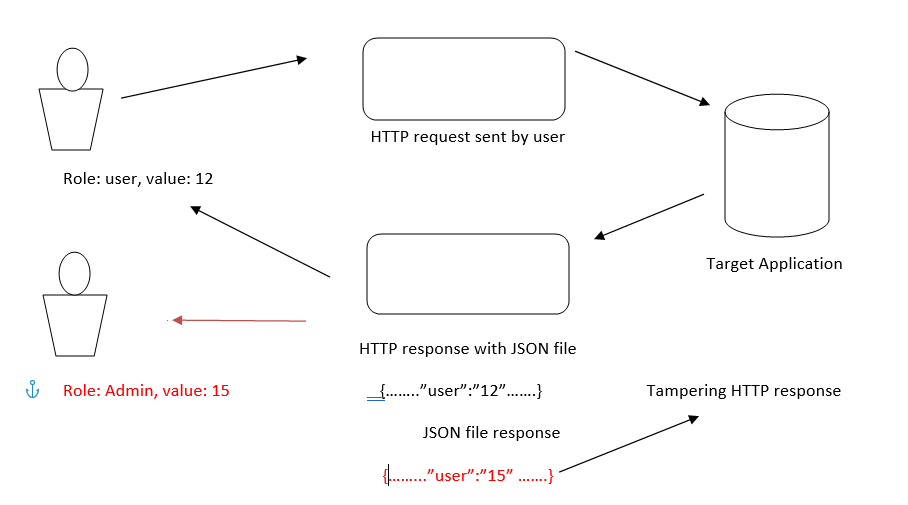
2. Manipulating the Response: An attacker passes malicious data to a vulnerable application or website, and the application includes malicious data in the HTTP response which leads to a way to set arbitrary headers and embed data according to the attacker. response manipulation enables cache-poisoning, XSS (cross-site scripting), page hijacking, or open redirect.
3. Check for Cookie flags: A secure flag is used to declare that the cookie may only be transmitted through an SSL/HTTPS secure connection. If the cookie is set, then the browser will not send any cookies if the connection is HTTP or over other unsecured connections. flags are responsible for preventing cookies from being observed by unauthorized users due to the transmission of cookies in clear text. If the flag is unchecked then third parties can see the cookies that are transferred over an unsecured connection.
4. Common data encoding: The cookies are encoded by the use of some data encoding techniques to prevent unauthorized users. cookies can be encoded in HEX codes, bas64 encodings, URL encoding, etc. base64 encoding you can see in this article: Encode an ASCII string into Base-64 Format.
5. Manipulations:
- Cookies can be manipulated by changing individual bits of data to see the results.
- Swapping key-value pairs or adding duplicates can be used for validation and other purposes.
Prevention of Cookie Tampering:
- Install an SSL certificate: without SSL the data (cookies) are sent in plain text, which is an attacker intercept they can simply read.
- Install a security plugin: this will block malicious IP addresses and prevent hack attempts on your website, if there is malicious activity it will alert you.
- Update your website: Always keep your website up to date, including plugins like themes and WordPress installations.
- Never click on suspicious links or those you don’t have any idea about.
- Avoid storing sensitive information on websites like your bank details on shopping sites or your login details.
- Clear cookies on a regular basis, and by doing this you will get rid of the sensitive information stored in your browsers. you can perform this by going to clear browsing data → in the advance section → select cookies and other site data.




