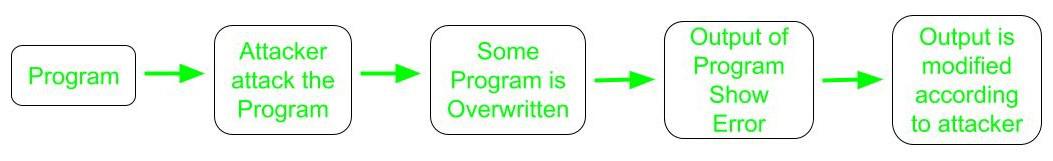
The mechanism in which the attacker starts overwriting a few lines of the program, in such a way that the output of the program becomes incorrect. And later on, the output changes with respect to the program and is called control hijacking.
Control Hijacking
The solution to the above problem is to divide the program into small parts. And check the output of the program at every step, due to which all the output will never be incorrect at the same time. Hence, lines of the program overwritten by the attacker can easily be traced after which the error can also be removed.
Types of Control Hijacking Attacks
- Buffer Overflow Attack
- Integer Overflow Attack
- Format String Vulnerabilities
1. Buffer Overflow Attack:
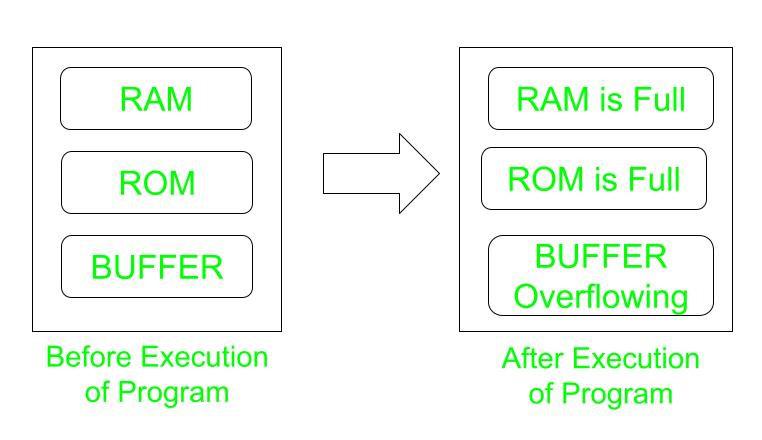
In a computer, the memory organization includes read-only memory (ROM) and random access memory (RAM), and extra space in memory called a buffer.The situation when a program execution starts in such a way that during the execution the entire memory space is full and slowly the buffer starts overflowing, at this instant immediately the hacker attacks the overflow data and therefore extracts the information from the memory is called a buffer overflow attack.
Buffer Overflow
The solution to the problem is that always specify the memory space before the execution of the program, as a result, the execution of the program will stop when the specified memory space is full and therefore the condition of overflow is avoided.
Hence, the memory can be protected from hacker attacks.
Types of Buffer overflow attack:
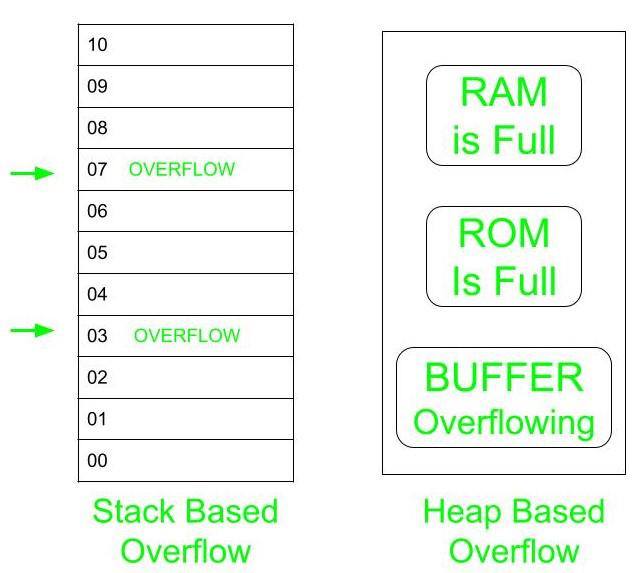
- Stack Based Buffer Overflow
- Heap Based Buffer Overflow
Stack Based Overflow & Heap Based Overflow
- Stack-Based Buffer Overflow: The condition when the different location of stack memory starts overflowing and the data at that memory location can be easily hacked by the hacker. This method is easy to implement and information can be extracted easily. The solution is to initialize the memory location before the program executes. So, that overflow can be prevented and data can be protected.
- Heap-Based Buffer Overflow: The condition when the entire memory starts overflowing can be hacked easily and is called a heap-based buffer overflow. This condition normally doesn’t exist, or else the entire memory of the computer will crash.
The solution is to prevent the overflow by specifying the memory location as a result the execution will stop and data will be saved.
2. Integer Overflow Attack
The integer overflow occurs when the output of the program is in the form of integers. So, that no. of digits in output exceeds the range and results in overflow which is attacked by the hacker. This process of extraction of information is called an integer overflow attack.
The solution again is to change the output to less number of bits. Hence, the overflow is prevented and information is safe.
3. Format String Vulnerabilities
This condition occurs when the output of the program is in form of special characters called strings. So, these characters start overflowing and information can be easily hacked by the attacker which is called format string vulnerabilities.
The solution is to specify the output in standard string format where every string has fewer characters, then the overflow can be prevented.
How To Prevent Control Hijacking?
Defense against control hijacking is a method used to prevent the impact of control hijacking attacks. Control hijacking attacks are a type of cyber attack where the attacker takes control of a program’s execution flow and directs it to malicious code, which can result in a wide range of security issues, system manipulation, and further exploitation.
Types of defense mechanisms against control hijacking attacks include:
1. Platform Defence
The mechanism of which the approach is to protect the information in terms of the hardware of the computer including the memory architecture, different types of pointers, many methods to
implement flow of the program.
The platform defense has the following approaches:
- Memory Architecture Protection: In this approach, the idea is to protect the entire memory architecture in such a way that the space of memory which is not defined should never be accessed. The execution of the program should occupy minimum space in the memory, preferably the buffer space of memory shouldn’t be used along with the required memory space should be used in the minimum quantity during the operation of the device. Therefore, the above method can protect the memory in all respect.
- Code Pointer Integrity (CPI): The approach in which different types of pointers are used during the execution of a program can hint the hacker to interfere in the main execution process for which all the pointers need to be protected under this method called code pointer integrity (CPI), along with this CPI also has the method of isolating the pointers called as code pointer separation (CPS), which means CPI and CPS work together.
- Code Flow Integrity (CFI): The approach in which there’s the execution of interrupt in between the main program. So, that flow of the program should again reach the main program but it can be attacked by the attacker, to protect this the CFI is used in order to correct the output.
2. Runtime Defence
Step 1: Protect the memory from unwanted access.
Step 2: Use standard antivirus and firewall.
Step 3: Allow execution in a given space.
Step 4: Use allocated space in memory.
Step 5: Minimum execution time of the program.
Step 6: Prevent buffer space.
Step 7: End the program for complete execution.
The runtime defense mechanism deals with the flow of the program from one end to another where the execution is done in the allocated space along with the minimum time of execution in the given hardware and software part after which the program is ended, in order to complete the execution process.




