This article was published as a part of the Data Science Blogathon.
Introduction
In this article, we will discuss the differences between Telnet and SSH. Compare Telnet and SSH in Terms of Security and User interface. We will also discuss how encryption takes place in SSH, why we use the Telnet Protocol Today, and much more. But before this, let’s understand the basics of Telnet and SSH.
Telnet:
The standard TCP/IP protocol for virtual terminal services is Telnet. It allows you to connect to a remote system and make it appear as though it were locally connected. The full form of TELNET is Terminal Network or Teletype Network, or Telecommunications Network.
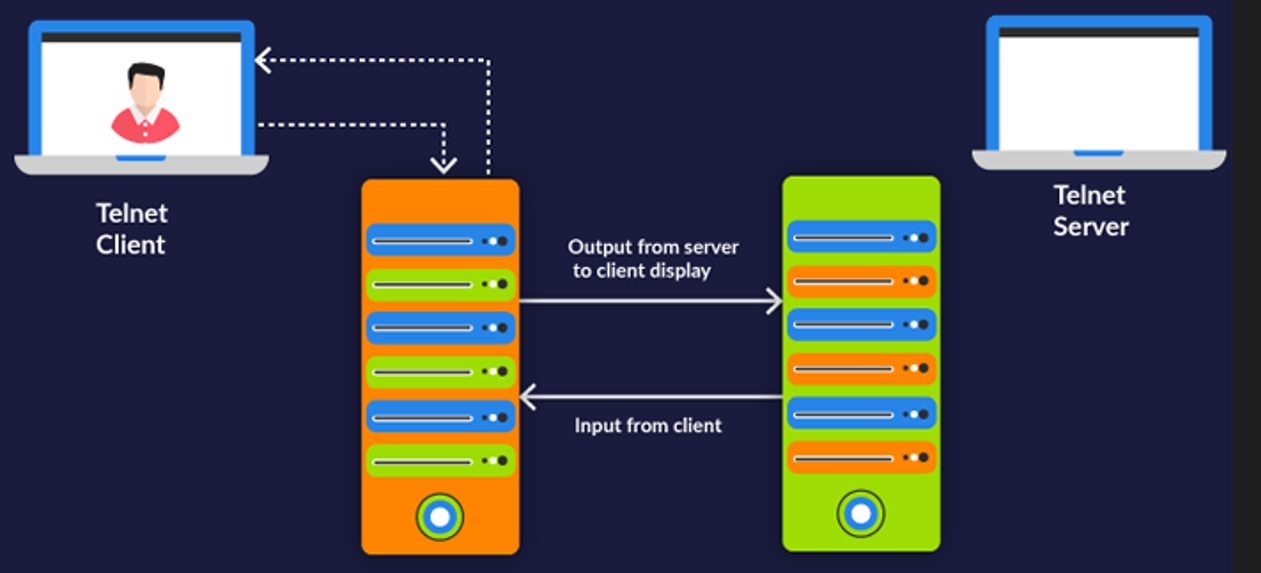
SSH:
SSH (Secure Shell) is a program that allows you to log into another computer via a network and run commands on it. SSH is a network protocol that will enable you to access and manage a device remotely. It is a popular protocol for connecting to network devices and servers over the internet. We can transfer files from one machine to another.
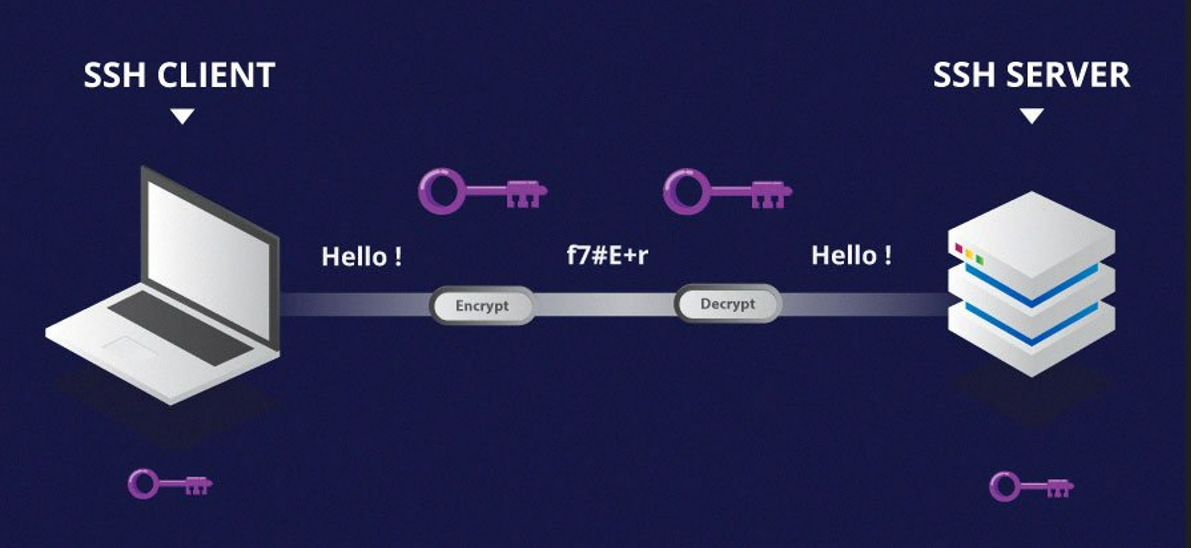
Differences in terms of Security
Telnet:
1. It does not provide any privilege for user authentication.
2. Telnet is vulnerable to security attacks.
3. Hackers cannot interpret the data sent using this protocol.
4. Telnet transfers the data in plain text.
SSH:
1. SSH is a more secure protocol that uses public-key encryption for authentication.
2. It overcomes many security issues of Telnet.
3. Usernames and Passwords can be prone to hacker attacks.
4. We should use the encrypted format to send data and a secure channel.
Differences in Terms of User Interface
Telnet:
1. Telnet connects to a network via port 23, created exclusively for local area networks.
2. They are used in Linux and Windows Operating systems.
3. They required low bandwidth usage.
4. By monitoring a user’s connection, anyone can access a person’s username, password, and other private information typed over the Telnet session in plaintext.
5. It is suitable for private networks.
SSH:
1. By default, SSH operates on port 22, but you can alter it.
2. They are used in all of the popular operating systems.
3. They required high bandwidth usage.
4. Because of security concerns, many professional organisations require using SSH, PuTTy, or other options instead of Telnet.
5. It is suitable for public networks.
How does Encryption take place in SSH?
SSH is a protocol, not software. By using these two machines, communicate securely over a network. It is typically used for remote command line access. It helps to:
a) Secure connection between two machines.
b) Allow remote administration of the server.
c) Use it to transfer files to a remote server.
We authenticate in SSH(Secure shell) before client and server communication. In the Authentication system, we access the server using ssh either using a password or a key. For keys, we can have either asymmetric(public and private key) or symmetric key concepts.
Key and password-based encryption is used in SSH for authentication.
Client:
Here we have an operating system where we can use ssh commands.
Server:
There is a machine in which we have an operating system where we need to install OpenSSH for using the ssh facility. For instance, we don’t have any predefined SSH for Windows operating systems, but for MAC and LINUX operating systems, we have predefined ssh as Unix-based systems.
SSH uses various data manipulation techniques at different points in the transaction to ensure the Security of information transmission. These include:
a) Symmetrical and Asymmetrical encryption,
b) Hashing, etc.
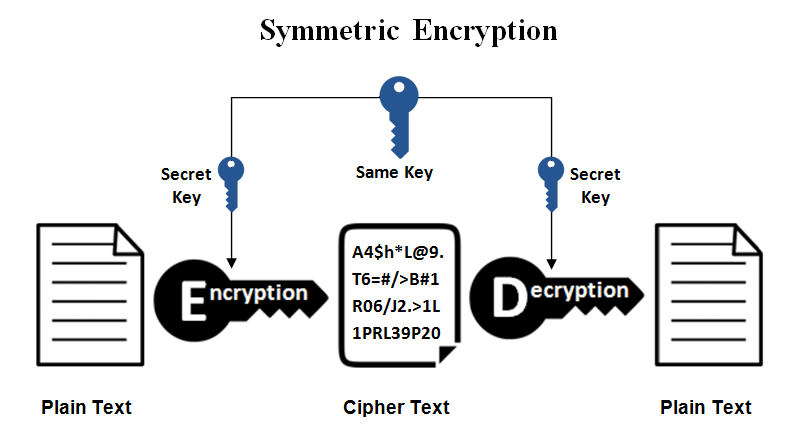
Symmetric Encryption:
SSH makes use of symmetric keys to encrypt the entire connection. Even password authentication is safeguarded against surveillance thanks to symmetrical encryption. The client and server contribute to creating this key, and the resulting secret is never revealed to third parties. We use a key exchange algorithm to generate the secret key. This technique generates a session-based symmetrical encryption key, which is used to encrypt data transferred between the server and the client. After that, the rest of the data must be encrypted using the shared secret.
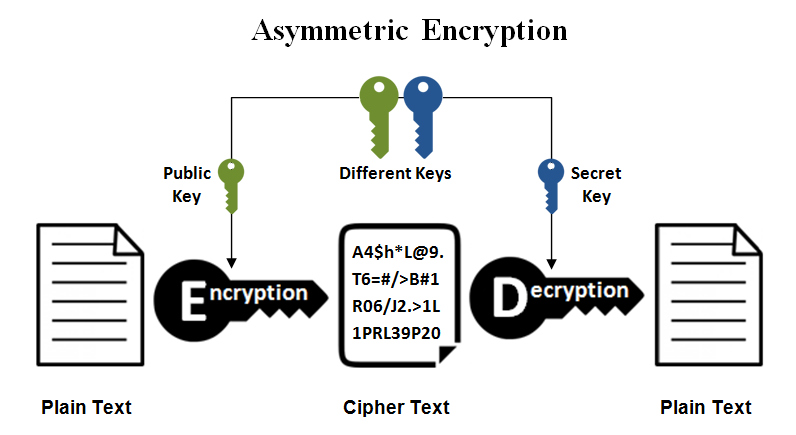
Asymmetric Encryption:
SSH uses asymmetric encryption in a few places. Asymmetrical encryption is used during the first key exchange process to set up the symmetrical encryption (used to encrypt the session). Both parties generate temporary key pairs and exchange the public key to generate the shared secret we will utilise for symmetrical encryption at this stage. SSH key pairs can be used to authenticate a client to a server. Cryptographic hashing is another type of data modification that SSH employs. Hashes are mainly utilised for data integrity and to verify the validity of communication because of these qualities. HMAC, or hash-based message authentication codes, is the most common use in SSH. These are needed to verify that the text of the received message remains unaltered.
Can we encrypt the Telnet Protocol? If yes, how?
Because Telnet is an unsecured interface, you can use Kerberos to authenticate your identity while preventing the disclosure of your login credentials. Kerberos is a user and server authentication technology that requires both parties to authenticate their identities. Kerberos is a symmetric, asymmetric cryptography system that evolved from symmetric key algorithms that use the same key for encryption and decryption. Researchers discovered a few years ago that Kerberos didn’t always encrypt the complete submitted ticket. This particular vulnerability has since been patched, but it remains susceptible. Hence secure shells are used more these days.
5. List the commands used in Telnet with their functionality.
Let’s see some of the essential commands with a simple process. First, we will connect to Telnet. Then we have to connect with a host, and then we have to mark the timing at different stages in the connection and also have to check terminal type and speed. After that, we have to close the connection and quit when we finish work. Now, to implement this small process, we have to use some of the commands which are mentioned below:
1. Status command: This command will tell you whether or not the Telnet client is connected.
2. Open command: To make a Telnet connection to a host, use this telnet command to open the hostname port number.
3. Timing Mark command: This command helps us to define the timing marks.
4. Terminal Type/Speed command sets the terminal type and speed.
5. Close command: This command helps us to close an existing Telnet connection.
6. Quit command: This command is used to exit from Telnet.
Conclusion
In this article, we have talked about the significant differences between the Telnet and SSH Algorithms. After studying various aspects, we have concluded that the SSH algorithm is better than the Telnet algorithm in terms of security. But this does not mean that SSH takes over Telnet in all aspects. There are primary uses where we still use Telnet instead of SSH, like Telnet can be used for various things like a mail server, running different programs, editing files, etc. We can also make servers to enable remote connections using Telnet to access data and play various games.
Other than this, there are some other use cases which are mentioned below:
1. Playing chess:
Is it necessary to play chess with a physical board or a high-tech electronic game? A text-based chess game might be right up your alley if you don’t. Anyway, isn’t chess a mind game?
2. Check The Weather Forecast:
You can always check the weather forecast using Telnet if you become tired of seeing it on TV or some nice-looking app on your smartphone. This free service has been available since 1995 and is still going strong. To check the weather forecast at Weather Underground, run o rainmaker.wunderground.com.
3. Find Good Excuses:
Telnet has your back whenever you need a good reason and can’t come up with one. The Bastard Operator From Hell excuse server shares the proper excuse every time. Even if it has nothing to do with your current circumstances, telling your boss one of these justifications would undoubtedly save you.
Key takeaways of this article:
1. Firstly, we have taken a basic understanding of both algorithms.
2. Then, we talked about their security and user interface differences.
3. Then, we discussed how encryption takes place in the SSH algorithm.
4. Finally, we have concluded the article by discussing some use cases that use the Telnet algorithm today.
It is all for today. I hope you have enjoyed the article. If you have any doubts or suggestions, feel free to comment below. Or you can also connect with me on LinkedIn. I will be delighted to get associated with you. Do check my other articles also.
The media shown in this article is not owned by Analytics Vidhya and is used at the Author’s discretion.




