Black hole filtering is something you can do in the realm of ethical hacking that is meant to protect an organization’s private data. This kind of software has been around for a few years, but as more and more malware emerges, it’s important that we understand what black hole filtering is, so we know how to best protect ourselves and our clients. Black hole software allows an organization’s employees access only to the network they should be able to view on the inside of the organization’s firewall; this prevents unnecessary exposure of personal information or data on private networks, rendering cyber-attacks useless.
Principle:
The basic idea behind black hole filtering is that the program filters the network out to only those who are entitled to view it. It has no advanced capabilities such as HTTP proxy software; however, it can have a great impact on the types of attacks that get through. Black hole filtering can eliminate any malware that uses a Windows server remotely in an unauthorized manner since the server is blocked from being accessed by outside users and there’s no port on which to send data. However, it does not mean that all malicious code will be eliminated. At best, it prevents malware from being able to send data to remote servers.
Anything that sends data over a TCP/IP protocol will be blocked by black hole filtering. However, a black hole filter does not block all types of attacks.
For example, if an attacker sends a file to an internal email server, the server will think that the file arrives from outside and then use an SMTP proxy to send the information out on port 25 for delivery. With black-hole filtering enabled, though, the packets being sent between the internal email server and external recipients will be blocked in transit only.
Work Function:
Black hole filtering works in conjunction with content filtering to provide maximum protection. Content filtering examines the packet and determines if it is malicious or simply an allowed file/application. Both types of filtering are critical pieces of an organization’s overall security framework. With both systems in place, companies can be reasonably assured that their private information is protected on a corporate network and beyond. Protecting your company’s private data from exposure to cyber-attacks is important for any company that relies on data for its income. Black hole filtering can be the first line of defense to make sure that your clients’ information stays where it belongs: inside your organization’s firewall, where it can be protected from any unauthorized access attempts.
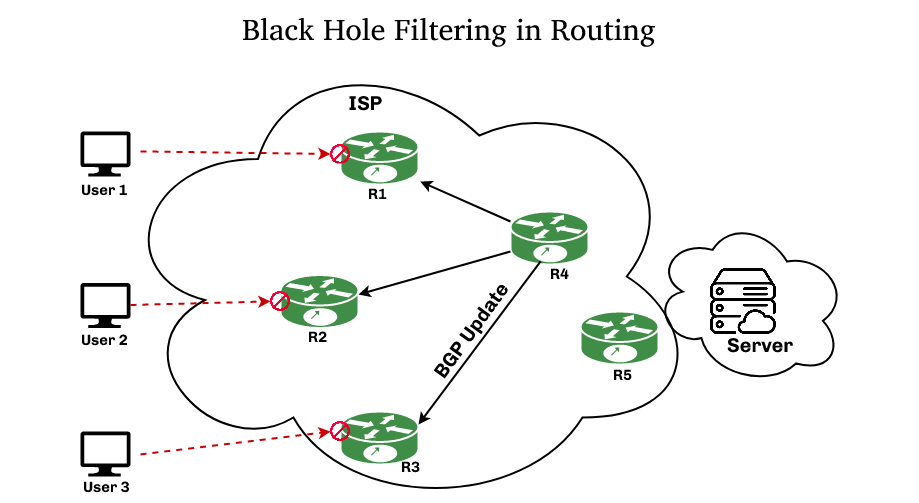
Key Points:
- Black hole filtering can be a cost-effective way to protect your company’s private data and eliminate attacks from data that leaves your network.
- The filtering system works by blocking any information from leaving the network on an external or internal server.
- Black hole filtering is typically used in conjunction with another security system, such as content filtering, to provide maximum protection against cyber-attacks.
Countermeasures:
- Prevention: Use security software to scan outbound traffic, this can prevent malware from sending data out of the network and infecting other systems. Also, use content filtering to make sure that only the users who are authorized to access your private information can do so. It may also be a good idea to limit internet access from your private networks as much as possible, which will make it harder for cyber attacks by reducing exposure.
- Detection: You can use a host-based IDS or IPS in order to detect intrusion into your network or system. You can also use a firewall as the first line of defense and block attacks from your network. You can also use a proxy server to filter inbound traffic and prevent traffic from coming into the company network.
- Response: The response would be to alert the users, you can do this by using banners or pop-ups on their computer screen, which will tell them that they are accessing private information and if they take no action will possibly data may be compromised. If they are already infected, then you should remove the malware and inform the users that it is being removed.




