Right on schedule, the group from Kaspersky that said they would take the stage at the 37c3 conference on Wednesday to discuss their findings and showcase a KTRR bypass for arm64e devices (A12-A16, and maybe even A17) did exactly that this morning.

We’ll give a brief overview of what led the team to find what they did below, but if you’d rather watch the presentation yourself, then you may certainly do so.
The group, which was comprised of Boris Larin (@oct0xor), Leonid Bezvershenko (@bzvr_), and Georgy Kucherin (@kucher1n) shared an interesting story about how themselves and colleagues were targeted by malware and how they responded with careful triangulation and reverse engineering techniques to learn more about it.
After observing strange behavior in the form of unexpected communications to and from iOS devices connected to their Wi-Fi network, their interest was piqued and they decided to dive deeper. This led them to find an attack that could be triggered with a malicious iMessage.
The attackers appeared to try covering their tracks by removing any trace of the iMessage and assets that could lead the Kaspersky team to find out what was going on, but they made a vital error — they didn’t remove all traces.
The Kaspersky team then set up a server to intercept the traffic where it could later be decrypted and inspected via forensic analysis. Through this method, they acquired the email addresses of their attackers and learned more about the workings of the attack.
Enter the KTRR bypass — a way to bypass security mitigations put in place by Apple to prevent access to kernel memory in the kernel text readonly region — which can be leveraged in a full exploit chain to make a jailbreak.
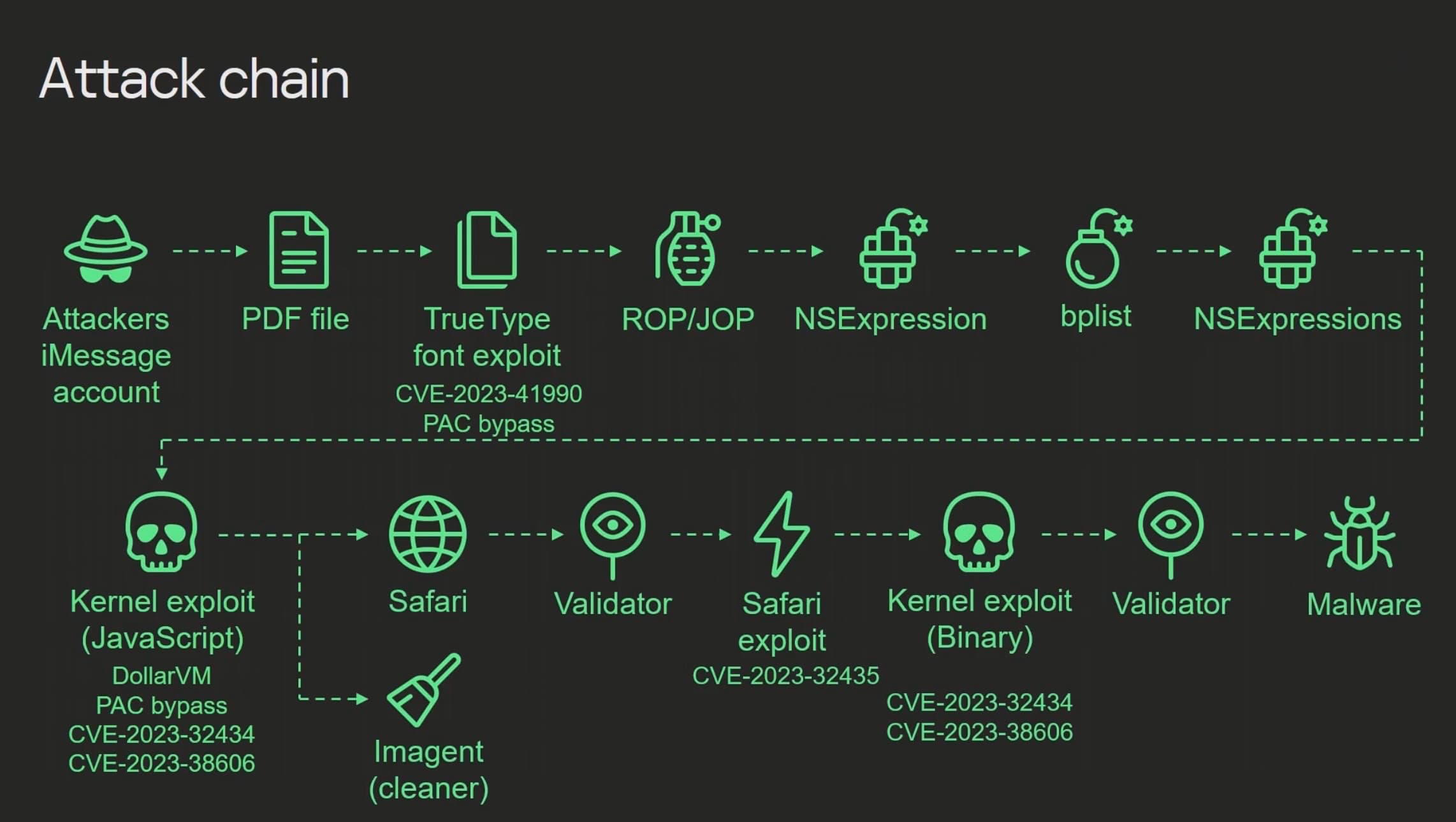
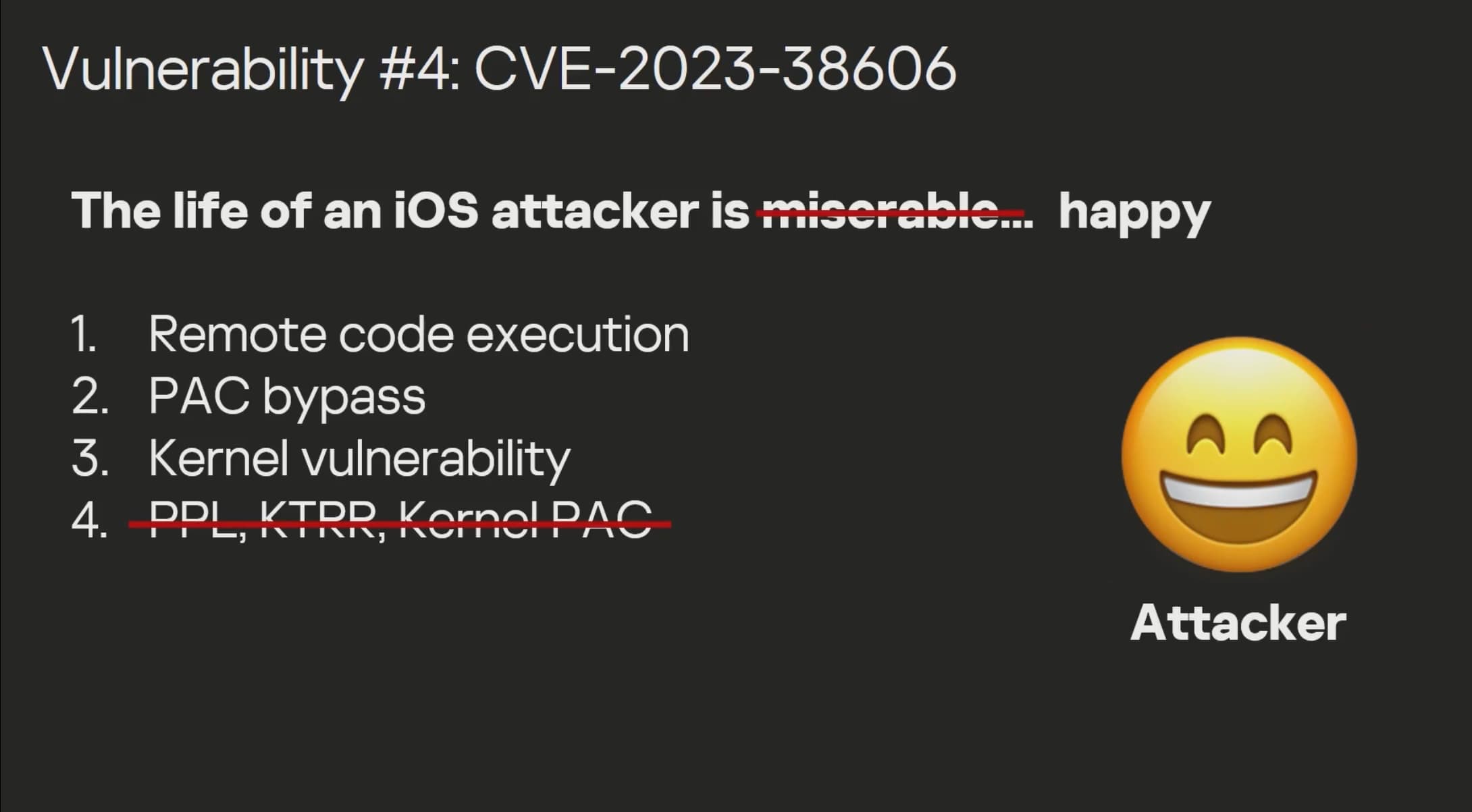
The KTRR bypass is hardware-based, which means that Apple can’t patch it with software updates. All the company can hope to do is obscure it with bandaids, but that won’t be enough to keep determined jailbreak creators out for long.
To be clear, while the KTRR bypass is hardware-based, it’s not the same as a hardware-based bootrom exploit like checkm8. However, since it’s hardware based, it can be used on affected handsets time and time again for as long as needed to create new jailbreaks.
Apple is likely to tweak their hardware in future iPhones to ensure that they aren’t vulnerable to the KTRR bypass. Still, doing so won’t fix the many devices that are already in circulation, which is why this is such a huge deal.
While newer software updates have obviously fixed the unique attack described by the Kaspersky team in detail today, anyone on an affected device type or firmware with a little bit of know-how can use the team’s open-source tool to see if their device has been compromised by the same attack that their team was hit with.
As of now, the Kaspersky team’s KTRR bypass isn’t yet publicized, but that is expected to change soon enough. It supports all firmware lower than iOS & iPadOS 16.6, which includes iOS & iPadOS 16.5.1 and older. Furthermore, the bypass works only on arm64e devices (A12-A16, and possibly A17, albeit the latter remains unconfirmed).
It will be interesting to see what becomes of the KTRR bypass, as it has the potential to bring us several more seasons of jailbreaking just when everyone was beginning to give up.




