This story has become common. In summer 2025, data breaches hit major companies, including Google and TransUnion. Customer data from dozens of sources ended up in criminal hands.
Tackers didn’t break into primary systems. They got access from a weak link in a larger chain. This is the reality of our digital world. There can be no impenetrable barriers.
Effective cybersecurity is built on simple, consistent habits and making yourself a difficult target. This way, when the inevitable threats arrive, they are detected, repelled, or recovered from with minimal damage.
I will walk you through the seven cybersecurity habits that form the core of my defense system on my Android phone and computer.
7
Beat hackers with a manager and 2FA
Data shows over 80% of breaches involve weak, stolen, or reused passwords. Cybercriminals exploit this with automated attacks called credential stuffing.
They take large lists of usernames and passwords from one breach and try them across thousands of sites until some match.
Although everyone knows password reuse is risky, we still do it. The system expects us to remember more than 90 unique logins on average, which isn’t possible.
Password managers are encrypted vaults that solve this issue. They generate long, random passwords, store them behind one master password, and autofill them in apps and websites.
Setting up multi-factor authentication (MFA) is the final step in securing an account. Even if a hacker buys your password on the dark web, it’s useless without the second factor.
6
Train your eye to catch phishing red flags
Cybercriminals have a vocabulary for their manipulative tactics, but they all boil down to trickery.
Phishing comes by email, smishing by SMS, and vishing by phone. A newer vishing variant uses AI.
Nowadays, a few seconds of audio from social media or a public talk can generate a convincing voice clone. A caller mimics a loved one, claims an accident or arrest, and demands money immediately.
Luckily, the red flags are often the same if you train yourself to spot them.
Scammers want you to panic, not think. They use lines like “Your account will be suspended,” “Suspicious activity detected,” or “Act now to avoid a fine.”
While AI makes scams more polished, many still have obvious typos or awkward phrasing that a legitimate company’s communication team would never allow.
Before you click, hover over any link to see the destination URL in the bottom corner of your browser. You can usually long-press the link on a phone to see a preview.
Look for misspellings in the sender’s email address, like support@micros0ft.com.
Unexpected attachments are a warning sign. Legitimate companies rarely send unsolicited invoices or security reports.
These often hide malware. When in doubt, go direct. Never click a link, download an attachment, or call a number from a suspicious message.
5
Practice mindful browsing and clicking
Your browser is your main window to the internet, and basic awareness helps keep it secure.
Always look for the lock. The padlock icon and “https://” at the start of the address confirm an encrypted connection.
HTTPS encrypts data in transit, while HTTP does not. This is critical in public Wi-Fi, where eavesdropping is easy.
Be wary of aggressive pop-ups and unexpected downloads. Scareware uses fake virus alerts to push a “fix” that is malware or junk. Legitimate security companies do not report infections through browser pop-ups.
Finally, treat URL shorteners with suspicion. Services like Bitly and TinyURL can mask a link’s true destination. This makes them a favorite tool for scammers who want to hide a malicious site behind an innocent-looking link.
When you receive a shortened link from a source you don’t fully trust, use a link-expanding website (for example, unshorten.it) to see where it leads before you click.
4
Secure your connection, at home and away
Public Wi-Fi in cafés, airports, and hotels is risky. These networks are open and often unencrypted, making them easy targets.
A common tactic is a man-in-the-middle attack, in which a criminal on the same network intercepts traffic between your device and the internet.
Another risk is an evil twin attack, where a hacker creates a fake hotspot with a legitimate-sounding name and captures your traffic.
Always use a virtual private network (VPN) on public Wi-Fi. It creates an encrypted tunnel for your traffic. With a reliable VPN, people on the same network can’t read your data or see where it’s going.
Your home network needs protection, too. Start by changing the default passwords for your Wi-Fi and your router’s admin settings. Routers often ship with default credentials like “admin” and “password.” Leaving them unchanged makes it easy to compromise your network.
3
Control your digital footprint step by step
Scammers can use every detail you share on social media. Your pet’s name and hometown often answer common security questions.
Cybercriminals excel at social engineering. They use these details to build trust, manipulate you, and craft convincing phishing attacks.
Posting vacation photos in real time signals that your home is empty. Frequent location tags at your favorite coffee shop or gym create a predictable map of your routine.
Treat personal information like a valuable asset. Review your privacy settings on all social accounts and set profile visibility to Private or Friends Only.
Finally, get into the habit of sharing your amazing vacation photos after safely returning home.
2
Backups help you recover fast when disaster strikes
Treat data backups as insurance. Backups are your primary defense against ransomware, which encrypts your files and demands payment.
Backups also help with device failure, loss, or theft. If ransomware hits, a recent, clean backup lets you recover quickly. Wipe the infected device and restore from backup.
Automate backups. The goal here is to set it and forget it. Use the built-in cloud backup on your devices. On your iPhone or iPad, turn on iCloud Backup in Settings.
On Android, make sure Google One or Google Drive backup is on.
Use a cloud backup service or built-in tools such as Time Machine (Mac) or File History (Windows) on your computer with an external drive.
1
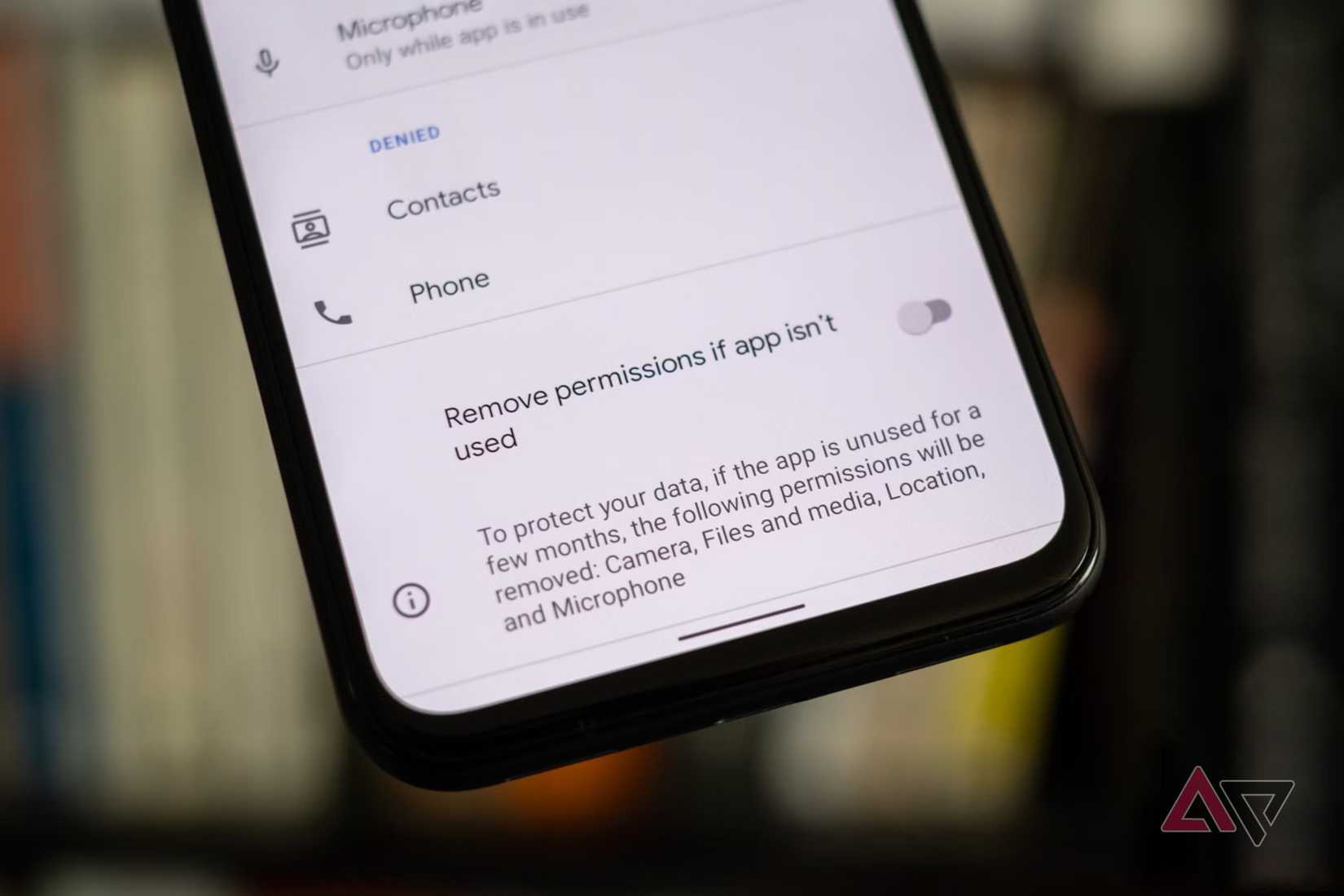
Follow the least privilege rule for apps
Every app you install requests access to your data and hardware (contacts, location, camera, microphone).
Follow the least privilege rule. Give each app only the access it needs. A maps app needs your location only while in use. A photo editor needs your photos, not your contacts or microphone.
Excessive permissions create privacy and security risks.
Some apps collect data for advertising. If an app is compromised and has microphone access, it can listen to your conversations.
Isolate, investigate, fortify
If you suspect an account is hacked, act fast with a focused three-step response.
First, isolate the breach. Change the password for the affected account immediately. If it’s a financial account, call your bank or card issuer to report suspected fraud and request a freeze.
Next, investigate. Check other important accounts for unauthorized activity, especially where you reused the compromised password. Run a full malware scan on your computer to detect malware, including keyloggers.
Finally, fortify your defenses. Set up MFA on the compromised account and other critical accounts lacking it. Use the incident to review and strengthen your security habits.