Near-field communication (NFC) technology allows devices to communicate over short distances and exchange data. NFC tags are small, unpowered devices that store and transmit data to compatible readers through electromagnetic fields. These cost-effective components offer high security features, including encryption, and enable fast, reliable data transfer. They also provide more efficient functionality than traditional RFID chips, allowing for many low-powered applications.
NFC tags are versatile, serving as physical components or emulated on devices like our favorite Android phones, tablets, and wearables. Physical NFC tags are used in contactless payment systems, smart home devices, wearables, and unexpected places like business cards and promotional materials. Hobbyists and smart home enthusiasts can create NFC tags to automate tasks or enhance smart home setups. For example, placing a tag by your door can activate smart home settings with a simple tap of your phone. But what exactly are NFC tags, and how can a small device offer so much functionality?
Understanding NFC tag functionality
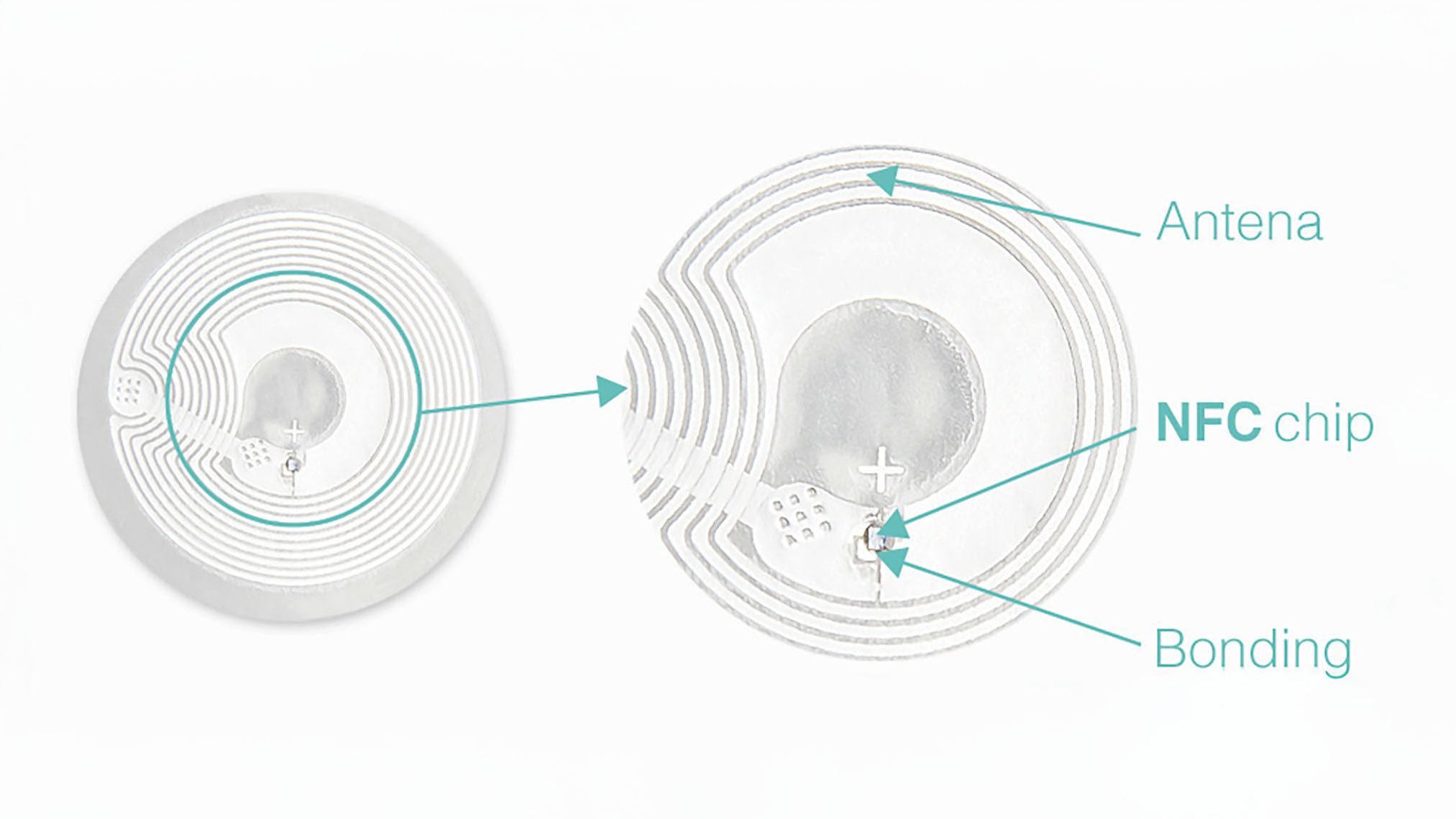
NFC tags are small, passive devices made of three primary components: a thin coil of copper or aluminum wire, a tiny silicon chip, and a protective adhesive or encasing material. The coil functions as an antenna while the chip stores and processes data. Together, these components form a simple circuit that operates without its own power source.
When an NFC-activated device, like a smartphone, is within about 1.6 inches (4 centimeters) of the NFC tag, its circuit generates an electromagnetic field. Both the reader and the tag contain inductors, which are coils of wire that serve as antennas. The reader’s powered inductor generates an electromagnetic field that encompasses the unpowered coil in the tag.
This interaction induces an electromotive force (EMF) in the tag’s coil through magnetic induction, effectively transferring energy. The induced current powers the silicon chip in the tag that did not have its own power source, allowing it to process and transmit data back to the reader.
This setup functions as a miniature transformer, with the reader and tag forming the primary and secondary coils. The induced current powers the silicon chip, allowing it to send stored data back to the reader using the same coil as an antenna. This type of bidirectional communication is very energy efficient, and the circuits can be very compact.
The NFC reader’s circuit differs from the tag in that it actively generates the electromagnetic field and includes a receiver to decode the data sent by the tag. In comparison, the tag’s circuit is minimal, designed solely to store small amounts of data. The two commonly used NFC tag types in consumer goods have storage capacities ranging from 48 bytes to 2 kilobytes. They are ideal for storing and transmitting small pieces of information such as contact details, Wi-Fi credentials, product IDs, or basic commands for smart home automation.
The five types of NFC tags
Two types of NFC tags are most common in consumer applications, but there are five types in the official standards. The NFC Forum, which sets the global standards for NFC technology, has a distinct definition for each. These standards ensure compatibility. Each tag type is designed for specific use cases.
- Type 1 Tags: These are the lowest memory capacity tags, ranging from 96 bytes to 2 kilobytes. They are used for low-security, simple information transfer, like embedding website links in posters.
- Type 2 Tags: These are the commonly used NFC tags in consumer goods. They are versatile, faster than Type 1 tags, and offer greater memory capacity. Examples include storing Wi-Fi credentials or embedding tags in business cards to share contact information.
- Type 3 Tags: These tags are designed for more complex operations and are compatible with Japanese Industrial Standards (JIS). An example is their use in electronic ticketing systems in public transportation.
- Type 4 Tags: Another common NFC tag type. These feature advanced security and are widely used in contactless payment systems, like embedding in credit and debit cards. This technology is also inside a card that lets someone wave it in front of a reader to open secure doors. It is integrated into many smart home devices.
- Type 5 Tags: These tags utilize NFC-V technology and are known for their extended range and durability. They are typically used in industrial IoT applications, like asset tracking or maintenance scheduling in manufacturing.
All types of NFC tags can be reprogrammed to change their data or commands. However, some data, like unique ID info, cannot be modified. To prevent unauthorized reprogramming, an NFC tag can be locked after programming by setting it to read-only mode.
NFC tag security and risks
NFC technology incorporates typical methods to enhance security, particularly in sensitive applications like payments and access control. Encryption protocols protect user data during transmission, such as Advanced Encryption Standard (AES) or public key cryptography. For contactless payments, the NFC reader initiates a secure channel and exchanges cryptographic keys to authenticate the transaction. In addition, dynamic data is often used in payment systems, meaning unique codes are generated for each transaction, further enhancing security.
In access control applications, NFC-activated cards use unique identifiers (UIDs) in combination with challenge-response authentication. For example, each access card at a hotel is individually programmed when you check in. When the reader sends a random challenge number, the card processes it using its cryptographic key and responds with an encrypted value. The system validates the response, granting access only if the values match. Still, NFC technology is not without its vulnerabilities.
Eavesdropping
Eavesdropping occurs when an attacker intercepts the communication between an NFC tag and a reader. Because NFC operates at 13.56MHz, the range of interception is typically very short, often less than 10 centimeters. While possible, eavesdropping is made difficult by NFC’s short-range nature and the encryption protocols that secure the transmitted data. Even if an attacker intercepts the communication, encrypted data remains unreadable without the proper decryption keys.
Relay attacks involve two connected devices. One device intercepts the communication from the NFC tag and relays it to the NFC reader in real time.
Relay Attacks
Relay attacks involve two connected devices. One device intercepts the communication from the NFC tag and relays it to the NFC reader in real time. The attacker does not need to clone the tag but instead uses specialized hardware to extend the range of the NFC signal. For example, one device could be near the payment card and another near the payment terminal to trick the system into authorizing an illegitimate transaction. This is generally addressed with time-outs for transactions and by requiring user confirmation.
Tag Cloning
Tag cloning occurs when an attacker duplicates the data stored on an NFC tag to create their own copy. Many NFC tags use unique identifiers (UIDs) and cryptographic authentication to prevent cloning. Dynamic protocols, like changing an access card’s security code daily, reduce the risk of using a cloned tag maliciously.
NFC tags are a reliable and secure technology. Most NFC vulnerabilities stem from improper implementation or a lack of user awareness. NFC is as safe as similar encryption methods used in other technologies. It also benefits from the short-range proximity needed to initiate an interaction between the tag and the reader.
NFC tags simplify everyday life
NFC tags bridge the physical and digital worlds, making everyday interactions smoother and faster. It made sense when credit card transactions moved from signing a receipt to a quick contactless “touch” of a card or phone to a payment terminal. Their applications span industries from retail and healthcare to IoT and creative fields. As NFC technology advances, these tiny tools will continue to simplify and enrich our lives, supporting secure payments, sustainability initiatives, and more.
Anyone can program their own NFC tags with a device like the Flipper Zero. Its hardware and firmware are open source, and its good documentation gets you started quickly. NFC tags make tasks easier and faster. NFC technology seems to be implemented in more places than you would think, so why not take control and use it in your own life?