You may remember the once popular Misaka package manager app by iOS developer @straight_tamago, which could be used in conjunction with the Kernel File Descriptor (KFD) exploit on compatible handsets to customize non-jailbroken devices.
Well, as it would seem, @straight_tamago is back, and they’re working with iOS developer Huy Nguyen (@little_34306) to offer an entirely new project to the general public that’s based on the SparseRestore exploit of the TrollRestore utility called MisakaX — no KFD exploit required.
From what we can gather, MisakaX works similarly to previously available tools like Cowabunga Lite by allowing users to customize their handsets without a jailbreak using only the backup-based trickery that these tools harness to make modifications to the iOS & iPadOS mobile operating systems.
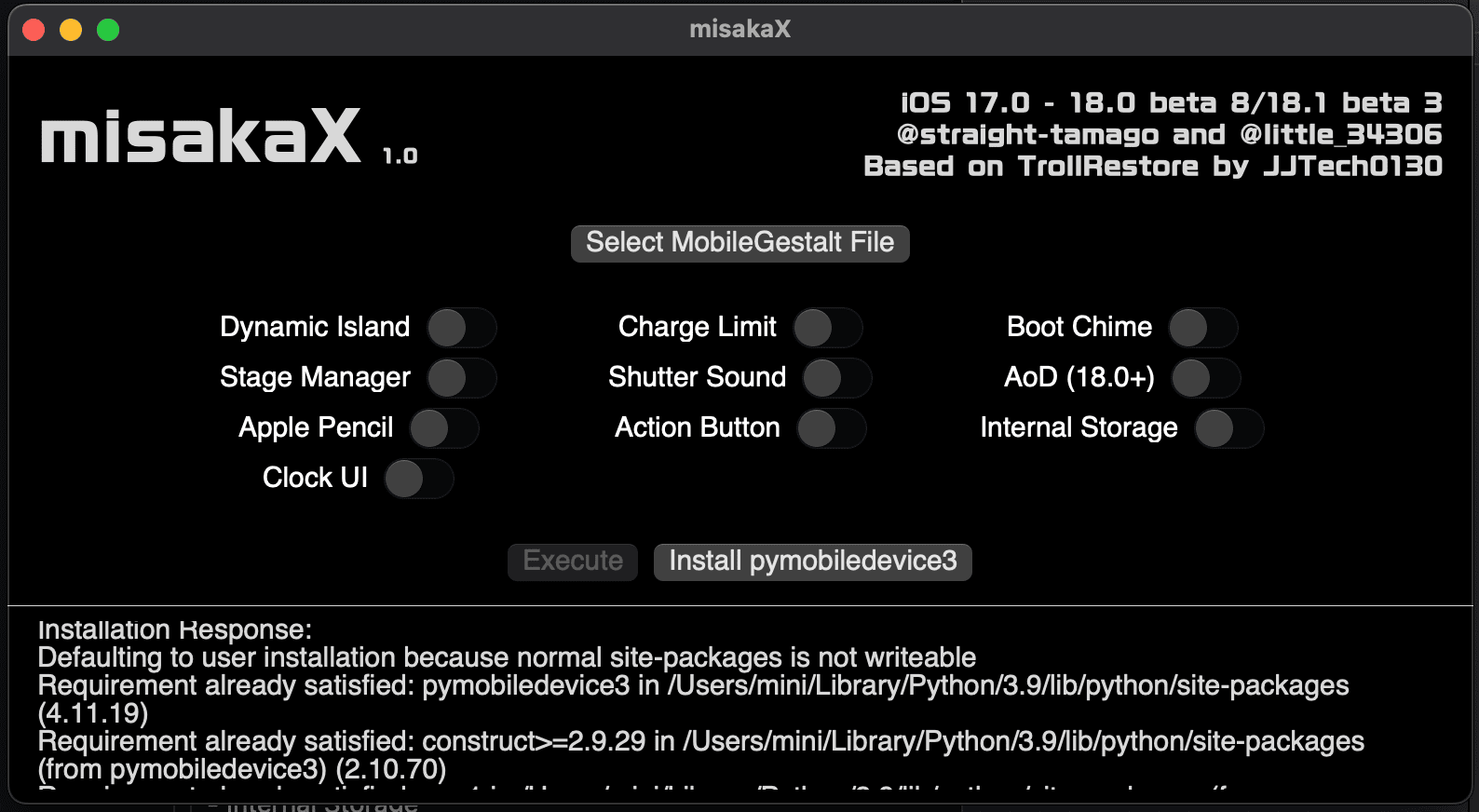
MisakaX is available as an application for macOS, and according to the project’s GitHub page, it supported the following kinds of customization as of version 1.0:
- Dynamic Island
- Charge Limit
- Boot Chime
- Stage Manager
- Shutter Sound
- Always-on Display
- Apple Pencil
- Action Button
- Internal Storage
- Clock UI
The tool was updated to version 1.1 shortly after the initial release with a fix for the pip error many users were getting, as well as a fix for an alert issue. Version 1.2 was also just released this morning with additional fixes, including support for macOS 11.0+, the Clock UI not working as expected, the duplicate_copy.plist, and adding new features such as SOS Collision, Tap to Wake on unsupported devices, and iPad multitasking.
MisakaX isn’t a jailbreak and appears to support iOS & iPadOS versions 17.0-18.0 beta 8/18.1 beta 3, which is important since there isn’t a jailbreak for these firmware versions on newer non-checkm8-vulnerable devices. That said, you can even use MisakaX with the latest devices running the latest firmware.
If you’re interested in giving MisakaX a try, then you can head over to the project’s GitHub page to learn more about it and how it can benefit you as the end user.
Are you going to be making use of MisakaX? Tell us why or why not in the comments section down below.

