A well commented and organized Organization should have a well-documented infrastructure for the Team’s operations. This makes it easy to train new staff with the mind map of devices in the data center. Netbox serves best for this purpose.
Netbox is a free and open-source tool written in Django, that manages and documents computer networks via the web. This highly improves the task of creating virtual implementations of devices in a data center which was being done by drawing on paper.
Netbox has the following features:
- Rack Elevation
- Single Converged Database
- Circuit Provider Management
- Multi-Site (tenancy)
- VRF Management
- Vlan Management
- IPAM – IP Address Management
- Customization Header For Logo’s etc
- Connection Management – Interfaces/Console/Power
- Report Alert
- DCIM – Data Center Infrastructure Management
This guide demonstrates how to secure Netbox IPAM Server with Let’s Encrypt SSL.
Getting Started
In this guide, you will require the following:
- A user with sudo access.
- Netbox IPAM Server installed on your system using the below guides:
- On containers:
- On CentOS|Rocky Linux 8|Alma Linux 8
- On Ubuntu 20.04|18.04
- On Debian 11|10|9
Having installed Netbox IPAM on your Linux system, you will proceed as below.
Secure Netbox IPAM Server with Trusted Certificates.
In this guide, I will illustrate two ways to install get trusted certificates installed on your system. The main objective of this process is to be able to access the Netbox IPAM web page via HTTPS.
- Using Let’s encrypt(Public IPs/FQDN)
- Using a self-signed Certificate(Private IPs)
So let’s plunge in!
Secure Netbox IPAM Server with Let’s Encrypt SSL.
Let’s Encrypt is used to generate trusted certificates for any FQDN for free. For this method to work, you need to have a public IP Address or an FQDN.
Again, I will demonstrate how to secure Netbox Server with Let’s Encrypt SSL for both Apache and Nginx web servers.
1. Create a VirtualHost file
For Apache Web server
I assume you already have the below conf file for Apache with the below lines.
Listen 8085
ProxyPreserveHost On
ServerName netbox.example.com
Alias /static /opt/netbox/netbox/static
<Directory /opt/netbox/netbox/static>
Options Indexes FollowSymLinks MultiViews
AllowOverride None
Require all granted
</Directory>
<Location /static>
ProxyPass !
</Location>
ProxyPass / http://127.0.0.1:8001/
ProxyPassReverse / http://127.0.0.1:8001/
Also, you will be required to make the below adjustment to your Netbox installation.
sudo vi /opt/netbox/netbox/netbox/configuration.pyIn the file, edit your allowed host to your FQDN
# Example: ALLOWED_HOSTS = ['netbox.example.com', 'netbox.internal.local']
ALLOWED_HOSTS = ['netbox.example.com']Restart Apache and supervisor
sudo systemctl restart supervisord
sudo systemctl restart httpdConfirm that the service is listening on port 8085 as below.
$ ss -tunelp | grep 8085
tcp LISTEN 0 128 *:8085 *:* ino:118544 sk:e v6only:0 <->Now install Certbot on your system as below.
##On RHEL 8/CentOS/Rocky Linux 8/Fedora
sudo dnf install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm
sudo dnf install certbot python3-certbot-apache mod_ssl
##On Debian/Ubuntu
sudo apt install certbot python3-certbot-apache
For Nginx
For the Nginx web server, you also need a virtual host file for Netbox with similar lines as below.
server {
listen 80;
server_name netbox.example.com;
client_max_body_size 25m;
location /static/ {
alias /opt/netbox/netbox/static/;
}
location / {
proxy_pass http://localhost:8001;
}
}Now proceed and install Certbot on your system.
##On RHEL 8/CentOS/Rocky Linux 8/Fedora
sudo dnf install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm
sudo dnf install certbot python3-certbot-nginx
##On Debian/Ubuntu
sudo apt install certbot python3-certbot-nginxSecure Netbox IPAM Server with Let’s Encrypt SSL for Apache|Nginx
Now proceed and install SSL certificates for your FQDN as stated in your virtual host file for Apache|Nginx above(netbox.example.com)
##For Apache
sudo certbot --apache -d netbox.example.com
##For Nginx
sudo certbot --nginxNow proceed as below.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): Enter a valid Email address here
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: y
Account registered.
Which names would you like to activate HTTPS for?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: netbox.example.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): 1
Requesting a certificate for netbox.example.com
Performing the following challenges:
http-01 challenge for netbox.example.com
Waiting for verification...
Cleaning up challenges
Deploying Certificate to VirtualHost /etc/nginx/conf.d/netbox.conf
Redirecting all traffic on port 80 to ssl in /etc/nginx/conf.d/netbox.conf
Successfully received certificate.
Certificate is saved at: a2enmod ssl
/etc/letsencrypt/live/netbox.example.com/fullchain.pem
Key is saved at: /etc/letsencrypt/live/netbox.example.com/privkey.pem
This certificate expires on 2022-01-09.
These files will be updated when the certificate renews.
Certbot has set up a scheduled task to automatically renew this certificate in the background.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -For apache, proceed as above but choose to install the certificates on the SSL conf as below
Which virtual host would you like to choose?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: ssl.conf | | HTTPS | Enabled
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press 1 [enter] to confirm the selection (press 'c' to cancel): 1That is it! You will have the SSL certificates added to your configuration file as below.
For Apache. (the below will be added in the ssl.conf file at the bottom)
.............
CustomLog logs/ssl_request_log "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
ServerName netbox.example.com
SSLCertificateFile /etc/letsencrypt/live/netbox.example.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/netbox.example.com/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
</VirtualHost>For Nginx. (In the Nginx conf)
server {
server_name netbox.example.com;
client_max_body_size 25m;
location /static/ {
alias /opt/netbox/netbox/static/;
}
location / {
proxy_pass http://127.0.0.1:8001;
}
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/netbox.example.com/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/netbox.example.com/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = netbox.example.com) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
server_name netbox.example.com;
return 404; # managed by Certbot
}Now you can proceed and access your Netbox IPAM web page via HTTPS.
Secure Netbox IPAM Server with self-signed Certificates
This is an alternative way to secure your Netbox IPAM site in case you do not have a Fully Qualified Domain Name. In this method, we will use OpenSSL to generate self-signed certificates. Ensure you have OpenSSL installed on your system.
##For RHEL 8/CentOS/Rocky Linux 8/Alma Linux 8
sudo yum install openssl
##For Debian/Ubuntu
sudo apt install opensslNow with the virtual host file for Nginx, proceed and generate self-signed certificates as below.
Create a configuration file for the certificates as below.
vim netbox_ssl.confIn the file, add the below lines replacing appropriately.
[req]
default_bits = 2048
default_keyfile = netbox_ssl.key
distinguished_name = req_distinguished_name
req_extensions = req_ext
x509_extensions = v3_ca
[req_distinguished_name]
countryName = Country Name (2 letter code)
countryName_default = KE
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Nairobi
localityName = Locality Name (eg, city)
localityName_default = Nairobi
organizationName = Organization Name (eg, company)
organizationName_default = Netbox
organizationalUnitName = organizationalunit
organizationalUnitName_default = Development
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_default = Your_IP-Address
commonName_max = 64
[req_ext]
subjectAltName = @alt_names
[v3_ca]
subjectAltName = @alt_names
[alt_names]
DNS.1 = localhost
DNS.2 = Your_IP-AddressReplace “Your_IP-Address” with the IP address of your system and proceed to generate the certificates.
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout netbox_ssl.key -out netbox_ssl.crt -config netbox_ssl.confPress “Enter” till the end and you will have your certificates generated. Now copy them to the /etc/ssl/certs directory as below.
sudo cp netbox_ssl.crt /etc/ssl/certs/netbox_ssl.crt
sudo mkdir -p /etc/ssl/private/
sudo cp netbox_ssl.key /etc/ssl/private/netbox_ssl.keyNow add the certificates to your Virtual Host file as below.
For Nginx, your conf file should appear as below.
server {
listen 80;
server_name 192.168.205.2;
client_max_body_size 25m;
location /static/ {
alias /opt/netbox/netbox/static/;
}
location / {
proxy_pass http://127.0.0.1:8001;
}
listen 443 ssl;
ssl_certificate /etc/ssl/certs/netbox_ssl.crt;
ssl_certificate_key /etc/ssl/private/netbox_ssl.key;
}In the above file add the paths for your generated certificates appropriately.
Access Netbox IPAM Web Interface Via HTTPS.
At this point, we can access the Netbox IPAM Web Interface Via HTTPS regardless of the method used to secure it. You need to allow HTTPS through the firewall.
sudo firewall-cmd --add-service=http --permanent
sudo firewall-cmd --add-service=https --permanent
sudo firewall-cmd --reloadFor ufw.
sudo ufw allow http
sudo ufw allow httpsNow restart Apache/Nginx and proceed to access the Web UI via the URL https://netbox.example.com or https://IP_address.com.
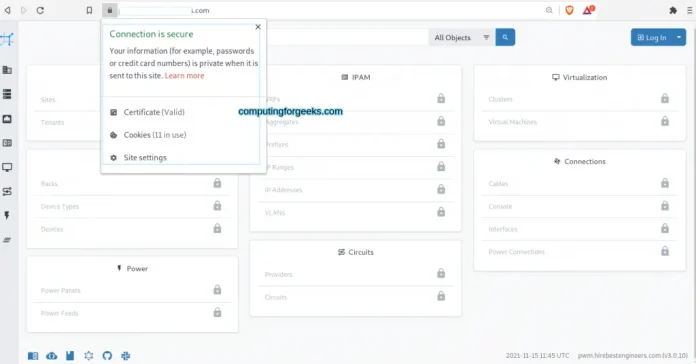
You should see the page secure as below.

That is it! I hope you too learned a lot from this guide on how to secure Netbox IPAM Server with Let’s Encrypt SSL.
See more on this page:
- How To Install phpIPAM on CentOS 8 / RHEL 8 Linux
- Secure FreeIPA Server With Let’s Encrypt SSL Certificate
- How To Secure osTicket with Let’s Encrypt SSL Certificates