This guide demonstrates how to encrypt files and directories on Linux using eCryptFS. But before we commence on it, we need to understand a few concepts.
What is eCryptFS?
With the increased importance of privacy and security nowadays, encryption plays an important role in ensuring the protection of confidential data. The following mechanisms are used in encryption:
- Full disk encryption- here, the entire disk or partition in which the filesystem is stored becomes encrypted. Tools used include Loop-AES, DMCrypt, CipherShed e.t.c
- File system-level encryption- such as EncFS and eCryptFS mounted on any directory at the top of the main file system
eCryptFS derived from Erez Zadok’s Cryptfs, and the FiST framework for stacked filesystems is a POSIX-compliant enterprise cryptographic file system for Linux. With ecryptFS, we can easily create an encrypted directory and store confidential data.
It was originally authored by Michael Halcrow and the IBM Linux Technology Center and is currently maintained by Dustin Kirkland and Tyler Hicks from Canonical.
With this information, we are set to dive into the installation and use of eCryptFS.
Step 1: Install eCryptFS on Linux
eCryptFS is available in many Linux distros’ default repositories and can be installed with the below commands:
##Install eCryptFS on CentOS 8/REL 8/Rocky Linux 8/AlmaLinux
sudo yum install epel-release
sudo yum install ecryptfs-utils
## Install eCryptFS on Arch Linux
sudo pacman -S ecryptfs-utils
##Install eCryptFS on Debian/Ubuntu
sudo apt-get install ecryptfs-utils
##Install eCryptFS on openSUSE
sudo zypper --install ecryptfs-utils Step 2: Encrypt Directories With eCryptfs On Linux
With eCryptfs installed on your Linux system, we are set to encrypt directories. the general syntax to encrypt a directory with eCryptfs is:
mount -t ecryptfs [source directory] [Destintaion directory] -o [options]You are required to replace the Destination directory with your own directory. Let’s take a practical example using the directory /demo on my system. The command here will be:
sudo mount -t ecryptfs demo/ demo/You will enter the below information to encrypt your directory
Passphrase: enter your passphrase
Select cipher:
1) aes: blocksize = 16; min keysize = 16; max keysize = 32
2) blowfish: blocksize = 8; min keysize = 16; max keysize = 56
3) des3_ede: blocksize = 8; min keysize = 24; max keysize = 24
4) twofish: blocksize = 16; min keysize = 16; max keysize = 32
5) cast6: blocksize = 16; min keysize = 16; max keysize = 32
6) cast5: blocksize = 8; min keysize = 5; max keysize = 16
Selection [aes]: 1
Select key bytes:
1) 16
2) 32
3) 24
Selection [16]: 1
Enable plaintext passthrough (y/n) [n]: n
Enable filename encryption (y/n) [n]: n
Attempting to mount with the following options:
ecryptfs_unlink_sigs
ecryptfs_key_bytes=16
ecryptfs_cipher=aes
ecryptfs_sig=213dac44e46bb873
WARNING: Based on the contents of [/root/.ecryptfs/sig-cache.txt],
it looks like you have never mounted with this key
before. This could mean that you have typed your
passphrase wrong.
Would you like to proceed with the mount (yes/no)? : yes
Would you like to append sig [213dac44e46bb873] to
[/root/.ecryptfs/sig-cache.txt]
in order to avoid this warning in the future (yes/no)? : yes
Successfully appended new sig to user sig cache file
Mounted eCryptfs
Step 3: Verify the Encryption
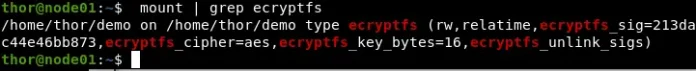
With these steps correctly done, your directory will be encrypted and mounted. You can verify this by issuing the command.
mount | grep ecryptfsSample Output for the above command.

Dive further into verification by creating a file. Let’s say a file.txt file in the encrypted folder.
sudo vi demo/file.txtIn the file add a simple text such as.
This is a demo file
Save and exit. Now we will try and read the contents of the file using the cat command.
$ cat demo/file.txt
This is a demo fileThis file is encrypted but still, you can view the content because it is mounted. On is able to view the contents as long as the file is mounted. When you unmount it, the file contents cannot be viewed.
Let’s verify it by unmounting the mounted directory. the syntax used is:
sudo umount [mounted_directory]In our case, the command will be:
sudo umount demoWith the directory now unmounted, we will try and view the contents of the file using the similar command we used above.
cat demo/file.txt Sample Output.

To view the file, you will now need to remount the directory and enter the same passphrase you used before while mounting it.
sudo mount -t ecryptfs demo/ demo/
Here enter the same passphrase you used:
Passphrase: enter your passphrase
Select cipher:
1) aes: blocksize = 16; min keysize = 16; max keysize = 32
2) blowfish: blocksize = 8; min keysize = 16; max keysize = 56
3) des3_ede: blocksize = 8; min keysize = 24; max keysize = 24
4) twofish: blocksize = 16; min keysize = 16; max keysize = 32
5) cast6: blocksize = 16; min keysize = 16; max keysize = 32
6) cast5: blocksize = 8; min keysize = 5; max keysize = 16
Selection [aes]: 1
Select key bytes:
1) 16
2) 32
3) 24
Selection [16]: 1
Enable plaintext passthrough (y/n) [n]: n
Enable filename encryption (y/n) [n]: n
Attempting to mount with the following options:
ecryptfs_unlink_sigs
ecryptfs_key_bytes=16
ecryptfs_cipher=aes
ecryptfs_sig=213dac44e46bb873
WARNING: Based on the contents of [/root/.ecryptfs/sig-cache.txt],
it looks like you have never mounted with this key
before. This could mean that you have typed your
passphrase wrong.
Would you like to proceed with the mount (yes/no)? : yes
Would you like to append sig [213dac44e46bb873] to
[/root/.ecryptfs/sig-cache.txt]
in order to avoid this warning in the future (yes/no)? : yes
Successfully appended new sig to user sig cache file
Mounted eCryptfsYou can view the contents of the file again.
Step 4: Mount the Directory automatically on Boot.
Each time your system boots, you will be required to remount your directory in order to view the contents. This can be tiresome at times. to curb this situation, you can configure eCryptFS to automatically mount the directory on boot.
Now in this guide, we will use a USB stick. Plug the USB stick into your system and identify the device using:
fdisk -lSample Output.

From this output, my USB stick is /dev/sdb3
Create a mount point at /mnt/flashdisk as below.
sudo mkdir /mnt/flashdiskMount the USB stick to this created mount point:
sudo mount /dev/sdb3 /mnt/flashdiskNow copy the signature from the output of this command:
$ sudo cat /root/.ecryptfs/sig-cache.txt
213dac44e46bb873Create a signature using the command:
sudo vi /root/.ecryptfsrcIn the file, paste the copied signature as shown
key=passphrase:passphrase_passwd_file=/mnt/flashdisk/key_file.txt
ecryptfs_sig=213dac44e46bb873
ecryptfs_cipher=aes
ecryptfs_key_bytes=16
ecryptfs_passthrough=n
ecryptfs_enable_filename_crypto=nCreate a passphrase on the USB stick
sudo vi /mnt/flashdisk/key_file.txtIn the file, add the below content replacing mypassphrase with your own passphrase
passphrase_passwd=mypassphraseThe next step is to edit the fstab file.
sudo vi /etc/fstabIn the file add the following lines
/dev/sdb3 /mnt/flashdisk ext3 ro 0 0
/home/thor/demo /home/thor/demo ecryptfs defaults 0 0In the above fstab file, replace the device and document roots appropriately.
Now save this file and reboot your system. When the device powers on, the home/thor/demo should be mounted using eCryptfs.
That is it! In this guide, we have learned how to encrypt Files and Directories on Linux using eCryptFS. I have also demonstrated how to view the contents of the encrypted file. I hope this article was of value.
See more on our page:
- Enable SSL Encryption and SCRAM-SHA-256 Password Authentication in PostgreSQL
- Secure FreeIPA Server With Let’s Encrypt SSL Certificate
- Install macOS Big Sur & Catalina on VirtualBox