SonarQube® is an automatic code review tool to detect bugs, vulnerabilities, and code smells in your code. It can integrate with your existing workflow such as Jenkins to enable continuous code inspection across your project branches and pull requests.
In this brief guide, we shall be installing this fantastic Open Source tool so that you can have the opportunity to review your team’s code before they are deployed in production. It will help in streamlining your applications as well as improving in their security by detecting outdated software used and making apt recommendations on the fly.
Pre-requisites
- SonarQube is built on Java, so we shall ensure that Java 11 is installed
- Another user apart ffrom root to run elasticsearch hence SonarQube
- PostgreSQL
To have this tool installed in your CentOS 7 box, follow the steps shared below:
Step 1: Update and install required tools
In this step, ensure that your server is well updated as well as install all tools you will require during the installation process. We shall also tweak system settings such as SELinux, max_map_count and fs.file-max. Run the commands below to update your server.
sudo yum update -yOnce the system is updated perform a reboot
sudo shutdown -r
Install necessary utilities required to configure SonarQube Code Review Tool in CentOS 7.
sudo yum install vim wget curl unzip -yConfigure SELinux as Permissive
This can be done by running the commands below:
sudo setenforce 0
sudo sed -i 's/^SELINUX=enforcing$/SELINUX=permissive/' /etc/selinux/configTweak max_map_count and fs.file-max
From Linux Kernel Documentation, this file contains the maximum number of memory map areas a process may have. Memory map areas are used as a side-effect of calling malloc, directly by mmap, mprotect, and madvise, and also when loading shared libraries.
To tweak the settings to befit SonarQube requirements, open “/etc/sysctl.conf” file and add the settings as shown below:
sudo tee -a /etc/sysctl.conf<<EOF
vm.max_map_count=262144
fs.file-max=65536
EOFApply the settings:
sudo sysctl --systemCreate a user for sonar
It is recommended that a separate user is created to run SonarQube. Let us create one as follows:
sudo useradd sonarThen set a password for the user
sudo passwd sonar
Step 2: Install Java 17 on CentOS 7
As it had been mentioned in the introductory section, SonarQube is written in Java and it needs Java installed
Confirm Java version after installation:
$ java --version
openjdk 11.0.15 2022-04-19 LTS
OpenJDK Runtime Environment 18.9 (build 11.0.15+9-LTS)
OpenJDK 64-Bit Server VM 18.9 (build 11.0.15+9-LTS, mixed mode, sharing)For Java 17: Install Java 17 (OpenJDK 17) on CentOS 7 / RHEL 7
Step 3: Install and configure PostgreSQL
In this example guide, we are going to install PostgreSQL server on the same sever SonarQube will reside. You can host it in a different server depending on your needs. To install PostgreSQL on your CentOS 7 Server, follow the steps below to get it up and running real quick
Add PostgreSQL Yum Repository
Add PostgreSQL Yum Repository to your CentOS 7 system by running the shared command below.
sudo yum install -y https://download.postgresql.org/pub/repos/yum/reporpms/EL-7-x86_64/pgdg-redhat-repo-latest.noarch.rpmInstall PostgreSQL Server and Client packages
After adding PostgreSQL Yum Repository, install PostgreSQL Server/Client packages:
sudo yum -y install postgresql14-server postgresql14After installation, initialize the database and enable automatic start
Now that the database packages have been installed, Initialize the database by running the following command
sudo /usr/pgsql-14/bin/postgresql-14-setup initdb
Then start and enable the service to start on boot
sudo systemctl enable --now postgresql-14After you have installed PostgreSQL server, proceed to configure it as follows. Open pg_hba.conf file and change “peer” to “trust” and “idnet” to “md5“.
$ sudo vim /var/lib/pgsql/14/data/pg_hba.conf
##Change this
local all all peer
# IPv4 local connections:
host all all 127.0.0.1/32 ident
# IPv6 local connections:
host all all ::1/128 ident
##To this:
local all all trust
# IPv4 local connections:
host all all 127.0.0.1/32 md5
# IPv6 local connections:
host all all ::1/128 md5Enable remote Access to PostgreSQL
In case your application is on a remote location, then you will need to allow it to access your database as follows:
Edit the file /var/lib/pgsql/14/data/postgresql.conf and set Listen address to your server IP address or “*” for all interfaces.
listen_addresses = '*'Then add the following to “pg_hba.conf” file
$ sudo vim /var/lib/pgsql/14/data/pg_hba.conf
# Accept from anywhere
host all all 0.0.0.0/0 md5
# Or accept from trusted subnet
host all all 10.38.87.0/24 md5Restart PostgreSQL service
sudo systemctl restart postgresql-14Set PostgreSQL admin user
We will need to change the password for the admin postgres user as shown below:
$ sudo su - postgres
-bash-4.2$: psql
postgres=# alter user postgres with password 'StrongPassword';
ALTER ROLE
postgres=# exitCreate a SonarQube user and database
Next, we are going to create a user for SonarQube. Proceed as shown below before exiting your database.
-bash-4.2$ createdb sonarqube
-bash-4.2$ psql
postgres=# CREATE USER sonarqube WITH PASSWORD 'StrongPassword';
postgres=# GRANT ALL PRIVILEGES ON DATABASE sonarqube to sonarqube;
postgres=# \qStep 4: Fetch and install SonarQube
Now we are at the point we have been waiting to arrive at for a long time. We shall download Long Term Release of SonarQube then install in our Server. Proceed as follows to get our SonarQube installed.
Fetch SonarQube LTS Version
You can visit SonarQube Downloads Page to view their various offerings. We shall be downloading the Long Term Release (LTS)
Downloading via command line interface:
cd ~/
wget wget https://binaries.sonarsource.com/Distribution/sonarqube/sonarqube-9.9.1.69595.zipThen unzip the file
unzip sonarqube-*.zipAfter that, rename the folder to sonarqube
sudo mv sonarqube-*/ /opt/sonarqube
rm -rf sonarqube*Step 5: Configure SonarQube
Once the files have been extracted to /opt/ directory, it is time to configure the application.
Open “/opt/sonarqube/conf/sonar.properties” file and add database details as shown below. In addition to that, find the lines shared and uncomment them.
$ sudo vim /opt/sonarqube/conf/sonar.properties
##Database details
sonar.jdbc.username=sonarqube
sonar.jdbc.password=StrongPassword
sonar.jdbc.url=jdbc:postgresql://localhost/sonarqube
##How you will access SonarQube Web UI
sonar.web.host=0.0.0.0
sonar.web.port=9000
##Java options
sonar.web.javaOpts=-server -Xms512m -Xmx512m -XX:+HeapDumpOnOutOfMemoryError
sonar.search.javaOpts=-Xmx512m -Xms512m -XX:MaxDirectMemorySize=256m -XX:+HeapDumpOnOutOfMemoryError
##Also add the following Elasticsearch storage paths
sonar.path.data=/var/sonarqube/data
sonar.path.temp=/var/sonarqube/tempGive SonarQube files ownership to the sonar user we created in Step 1.
sudo chown -R sonar:sonar /opt/sonarqube
sudo mkdir -p /var/sonarqube
sudo chown -R sonar:sonar /var/sonarqubeIn case Java cannot be found in the default location, you will have to specify the binary files for SonarQube to find. You can specify where java is located in the “/opt/sonarqube/conf/wrapper.conf” file. Look for “wrapper.java.command” line and place your Java location beside it thus.
wrapper.java.command=<custom-path-to-java-binary>Add SonarQube SystemD service file
Finally we are going to ensure that we shall be able to manage our SonarQube application via Systemd so that we can start and stop it like other services in your server
$ sudo vim /etc/systemd/system/sonarqube.service
[Unit]
Description=SonarQube service
After=syslog.target network.target
[Service]
Type=forking
ExecStart=/opt/sonarqube/bin/linux-x86-64/sonar.sh start
ExecStop=/opt/sonarqube/bin/linux-x86-64/sonar.sh stop
LimitNOFILE=65536
LimitNPROC=4096
User=sonar
Group=sonar
Restart=on-failure
[Install]
WantedBy=multi-user.targetAfter editing systemd files, we have to reload them so that they can be read and loaded.
sudo systemctl daemon-reloadThen start and enable the service
sudo systemctl start sonarqube.service
sudo systemctl enable sonarqube.serviceCheck its status if it successfully started and is running.
systemctl status sonarqube.serviceStep 6: Alter Firewall rules to allow SonarQube Access
At this juncture, sonarqube service should be running. In case you cannot access the web interface, visit the log files located in “/opt/sonarqube/logs” where you will find
- elasticsearch logs (es.log)
- Sonar logs (sonar.log)
- web logs (web.log)
- Access logs (access.log)
- And others
We enabled SonarQube web to listen on port 9000 and we should allow this on this on the firewall. Proceed to do this as shared below
sudo firewall-cmd --permanent --add-port=9000/tcp && sudo firewall-cmd --reloadStep 7: Access the Web User Interface
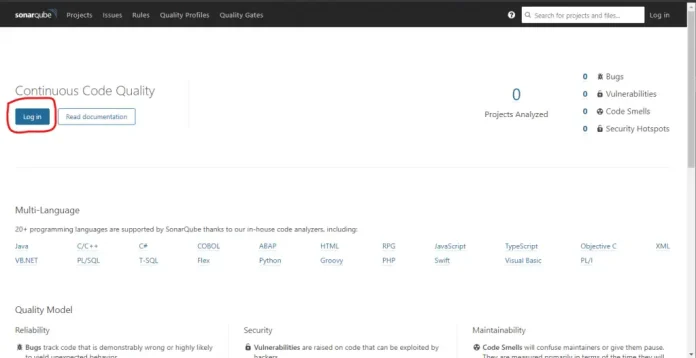
The time we have been waiting for has finally showed up. We are now ready to access SonarQube interface and begin assessing our code for security. To access the interface, open your favorite browser and point it to http://server-ip-or-fqdn:9000. You should see a page similar to the one below.

Step 8: Logging in
To log in, simply click on the “Log In” button as shared above and you should be ushered in a page similar to the one shared below. Use username as “admin” and password as “admin“.

Reset admin user password as required.

And you should be ushered into the main area as illustrated below

Conclusion
Now we have our automatic code review tool that you can use to scan various applications before they are approved for production. It is simple, thorough and complements your organizational security needs. Try it out.
Otherwise, we appreciate your visit and for the tremendous support you continue to extend. other guides you might enjoy include:
- Best Cybersecurity Books To Read
- Best Books To Learn Data Security & Encryption
- Top Certified Information Security Manager (CISM) study books
- Best CCNA Security (210-260) Certification Study Books