JSON(JavaScript Object Notation) denotes standard text-based-data format . It is widely used to provide a support mechanism between the server and the web application for the transmission of data. JSON Hijacking is a kind of network security attack. In this attack, an attacker targets a system that has access to cross-domain-sensitive JSON data. This attack is similar to Cross-Site Request Forgery holding some differences. In Cross-Site Request Forgery, the attacker forces the user to execute unwanted actions whereas in JSON Hijacking the user is manipulated to access a crafted link that will read the user’s data and pass it to the attacker.
Note: Older Browsers were more vulnerable to JSON Hijacking. As of now, this vulnerability has been fixed in modern Browsers. The users using modern browsers are almost safe.
Detection Methods:
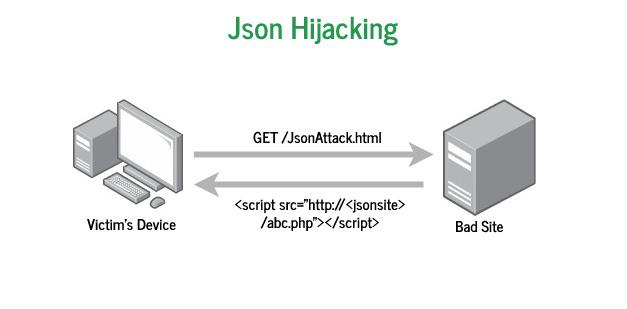
- The attacker gets an authenticated user to visit a malicious page to read their data.
- From where we have logged in, the malicious page will try to access the sensitive data by embedding a script tag in an HTML document. i.e.
<script src=”http://<jsonsite>/abc.php”></script>
This code will run by the browser requesting a GET Request to abc.php and the sensitive data will be sent along with the request.
- One should also be aware of whether the targeted application is compatible with older applications or not.
- This should be checked if Access-Control-Allow-Origin is set to the domain or not. If not, We should set the Access-Control-Allow-Origin to the specific domain, by this JSON Hijacking is not possible.
- Vulnerable JSON Responses should be avoided.
JSON Hijacking Prevention:
- By returning JSON with an object on the outside: We can prevent JSON Hijacking by having the outside primitive be an object for JSON strings. Some examples are-
Vulnerable :
[{ “object” : ” ” }] // Not inside an object, inside an array
Not Vulnerable :
{ “object” : ” ” } // Inside an object
{ “object” : [{ “object”:” “}] //Inside an object
- By Adding Access-Control-Allow-Origin: To prevent JSON Hijacking, we can add Access-Control-Allow-Origin. With this addition, the attacker will lose control over our trusted domains.
- By Preventing Ourselves from Using Older Browsers: One of the methods for preventing JSON Hijacking is that we can prevent ourselves from using older browsers by creating a mechanism in the application. This will prevent us from using our application from an older browser.




